What Is a Software Supply Chain Attack?
The software supply chain consists of any code, component, binaries components and tools that are involved in taking an application from development to production. It begins with a repository or package manager, any CI tooling, and build and packaging scripts that enable you to deploy and run the application. The supply chain usually involves phases like build automation, QA and testing, and deployment automation.
Supply chain attacks occur when a malicious actor infiltrates the development or distribution process of software to insert malicious code into a product or service. By targeting less-secure elements in the supply chain, attackers can compromise the integrity of the software and exploit it to gain unauthorized access, steal data, or disrupt operations.
These attacks often go unnoticed until after the compromised software has been widely distributed or used. The stealthy nature of supply chain attacks makes them particularly dangerous, as the malware or vulnerability introduced can remain hidden within trusted applications for an extended period. This makes supply chain security a top priority for security teams and development organizations everywhere.
In this article:
- Statistics About Software Supply Chain Attacks
- 6 Recent Supply Chain Attack Examples
- 5 Types of Supply Chain Attacks
- 6 Ways to Defend Against Supply Chain Attacks
Statistics about Software Supply Chain Attacks
The facts about software supply chain attacks are alarming. Here are some key statistics:
- Gartner predicts that by 2025, 45% of organizations would have experienced a software supply chain attack.
- The FBI has reported a 62% increase in ransomware attacks from 2020 to 2021.
- A Cloudbees survey showed that 45% of enterprises have admitted that they’ve secured only half of their software supply chain.
- Argon, an Aqua Security company, has found that software supply chain attacks grew by over 300% in 2021.
These statistics tell us that software supply chain security will become even more important in the coming years as software supply chain attacks are on the rise.
6 Recent Supply Chain Attack Examples
SolarWinds Attack
The SolarWinds attack is without a doubt the watershed moment that woke the technology world up to the perils of software supply chain attacks. SolarWinds is a leading Network Performance Monitoring (NPM) tool that is used by organizations of all sizes, including government institutions.
The attackers had access to the SolarWinds supply chain for over a year before it was actually discovered. Every customer organization of SolarWinds was, in turn, compromised leading to a ripple effect that is so massive that it cannot be easily quantified.
Mercedes-Benz Source Code Leak
Taking place a year after, in May 2020, an attacker was able to register an account on a code-hosting portal and then downloaded 580 Git repositories through Gitlab containing the source code of onboard logic units (OLUs) installed in Mercedes vans. The hack was due to a lack of account authorization processes.
The source code leak was allowed due to exposed passwords and API tokens of Daimler’s internal systems to make matters worse. Bad actors could use passwords and keys to execute future intrusions against Mercedes-Benz cloud and internal network.
CodeCov Attack
CodeCov is a leading code coverage solution that shows the testing coverage on any code base. In April 2021, the CodeCov Bash Uploader script was compromised and modified. The attacker leveraged the Docker image that was used in CodeCov’s supply chain to gain access. This led to all customers of CodeCov also being vulnerable to the attack as CodeCov is a tool that is embedded into their customers’ software supply chain.
By now, you probably notice the pattern of supply chain attacks where one breach opens up innumerable other supply chains that are connected.
The following image shows a full list of major supply chain attacks, published by the US National Counterintelligence and Security Center (NCSC).
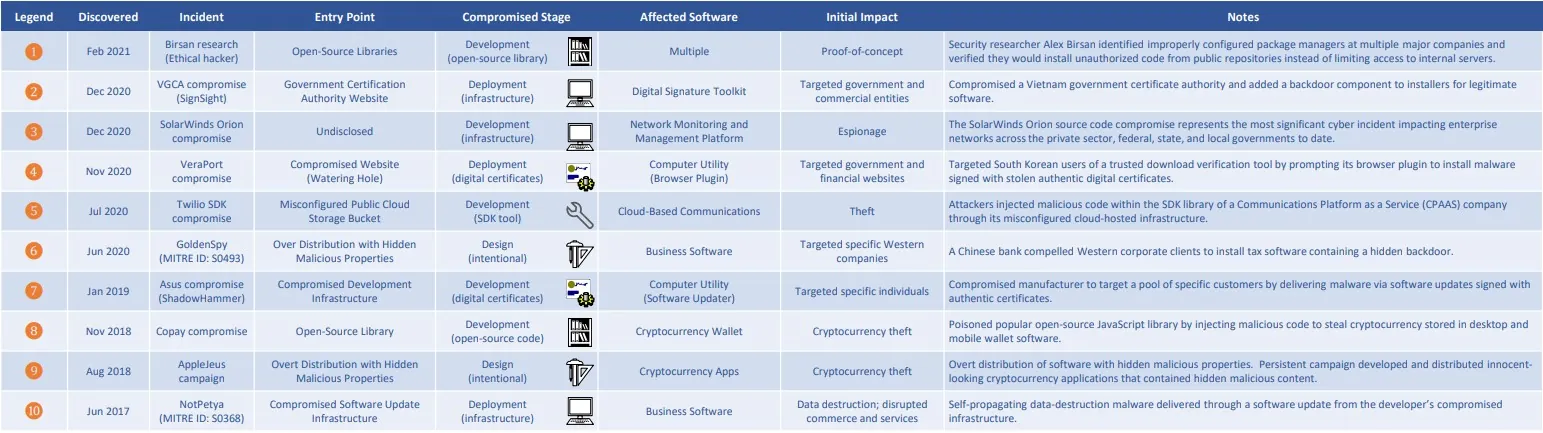
Source: NCSC
5 Types of Software Supply Chain Attacks
1. CI/CD Pipeline Breach
Attackers are looking for ways to infiltrate the CI/CD pipeline used by organizations to deliver software. With the CI/CD pipeline being the central nervous system of the entire software development process, any change made here has ripple effects on production applications, and customer applications as well.
2. CI/CD Tool Misconfigurations
As software practices are becoming modernized, configuration as code is a best practice. This involves codifying configuration of aspects such as infrastructure and policies that govern software processes. This configuration is stored in the form of YAML files. Often control over these configuration files are not properly secured, leaving attack vectors and vulnerabilities open to attackers. In the wrong hands, these configuration files can be badly misused.
3. Compromised Software Building Tools
There are numerous tools that make up a modern software supply chain, and the list is only growing by the day. These tools range from open source software to commercial tools. These tools play different roles including creating builds, quality testing, and deploying code to production. It is important to secure these tools and ensure that they don’t become a vector for a threat actor to inject malicious code into the pipeline.
4. Dependency Confusion Attack
Package managers are a vital part of working with any programming language like Node.js or Python. Downloading packages from these platforms has risks as anyone can upload a package to them. In recent times, attackers have found a way to trick developers into downloading malicious packages by targeting misspellings of the most commonly downloaded packages. This type of attack is called dependency confusion. Since developers mostly type in package names in a command line interface, typos are common.
A security researcher was able to use this method of ‘typo squatting’ to propagate infected packages to organizations like Apple and Microsoft.
5. Source Code Threats
Insecure code and compromised source control systems are among the most common source code threats. Human error and lack of secure coding practices can introduce vulnerabilities to the source code. Additionally, insecure development workstations can introduce insecure or malicious code.
You can mitigate insecure code threats by implementing policies in developer workstations, scanning code and APIs regularly during and after development, and establishing secure code practices. However, you should also ensure that developers cannot push insecure or malicious code into source repositories by including human reviews for source code changes.
6 Ways to Defend Against Supply Chain Attacks
Despite the challenges, you can mitigate security risks by following these practices to manage your software supply chain.
1. Use Checklists to Control Processes
Implementing checklists is an effective method to control software development and deployment processes. These checklists can serve as guidelines for security best practices at every stage of the software supply chain, ensuring that critical security steps are not overlooked.
For example, before code is merged into a main branch, a checklist can require a review of the code for known vulnerabilities, adherence to secure coding standards, and completion of all tests. Similarly, deployment checklists can include steps for verifying the security configurations of environments, ensuring encryption of sensitive data, and validating that all external dependencies are up to date and secure.
2. Reduce the Attack Surface
Reducing the attack surface of the software supply chain involves minimizing the number of potential points where an attacker can try to insert malicious code or exploit vulnerabilities. This can be achieved by minimizing the use of third-party components and libraries to only those that are absolutely necessary, regularly updating them to their latest secure versions, and removing unused or outdated components.
Organizations should also enforce access controls and limit privileges for both users and automated processes, ensuring that they have only the permissions necessary to perform their tasks. Reducing the number of people who have access to critical parts of the supply chain further diminishes the risk of insider threats or accidental leaks.
3. Scan Every Step of the Supply Chain
Scanning every step of the software supply chain is crucial for identifying vulnerabilities early. This involves using automated tools to scan for vulnerabilities in third-party libraries and dependencies, as well as static and dynamic analysis tools to find security flaws within the codebase itself.
Continuous integration (CI) environments should be configured to automatically run these scans on every code commit, allowing for immediate feedback and remediation. Additionally, scanning container images and infrastructure as code (IaC) templates for misconfigurations and vulnerabilities ensures that the entire application stack, from code to infrastructure, is secure.
4. Ensure Partner Applications and Integrations are Secure
In today’s interconnected ecosystem, applications often rely on integrations with third-party services and APIs. It’s vital to ensure that these partners adhere to security standards that are as stringent as your own. Conduct thorough security assessments of partner applications before integration, and regularly review these integrations for new vulnerabilities.
Use secure communication protocols and ensure that access to third-party services is closely monitored and controlled. Establishing clear contractual agreements that define security requirements and responsibilities can also help in managing the security of third-party integrations.
5. Leverage Security and Penetration Testing
Security and penetration testing are important tools in identifying and mitigating potential vulnerabilities before attackers can exploit them. Regularly scheduled penetration tests conducted by external experts can provide an outsider’s perspective on the security of your software supply chain, uncovering weaknesses that internal teams might overlook.
Simulating real-world attack scenarios allows organizations to understand how an attacker might breach their systems and to strengthen their defenses accordingly. Additionally, adopting a bug bounty program can encourage ethical hackers to safely report vulnerabilities, further enhancing security.
6. Use Dependency Graphs
Dependency graphs are a visual representation of the dependencies within a project, highlighting how different components and libraries are interconnected. Utilizing dependency graphs can help identify outdated or vulnerable dependencies that need to be updated or replaced. They also enable a better understanding of the potential impact of a vulnerability in one component on the rest of the system.
Tools that generate and analyze dependency graphs can automate the detection of vulnerabilities, making it easier to maintain a secure software supply chain. By continuously monitoring and updating the dependencies based on insights from dependency graphs, organizations can proactively prevent security breaches.
How Aqua Protects Against Software Supply Chain Attacks
Aqua software supply chain security solution scans every step of the CI/CD pipeline looking for vulnerabilities, and reports on any anomalies. With readymade integration for the top CI/CD tools like GitHub, GitLab, Jenkins, and more, Aqua has you covered no matter which CI/CD tooling you use.
Aqua covers the supply chain end-to-end and consolidates all this monitoring data in a single place and delivers alerts on them in real-time. This is a powerful and actionable way to fight security threats to your software supply chain. Leverage Aqua and bring deep visibility and greater security to your software supply chain.
