Full Lifecycle Container Security
Protect container-based cloud native applications from development to production, using the industry’s most advanced container security solution.
Learn MoreAqua scans CI builds and images
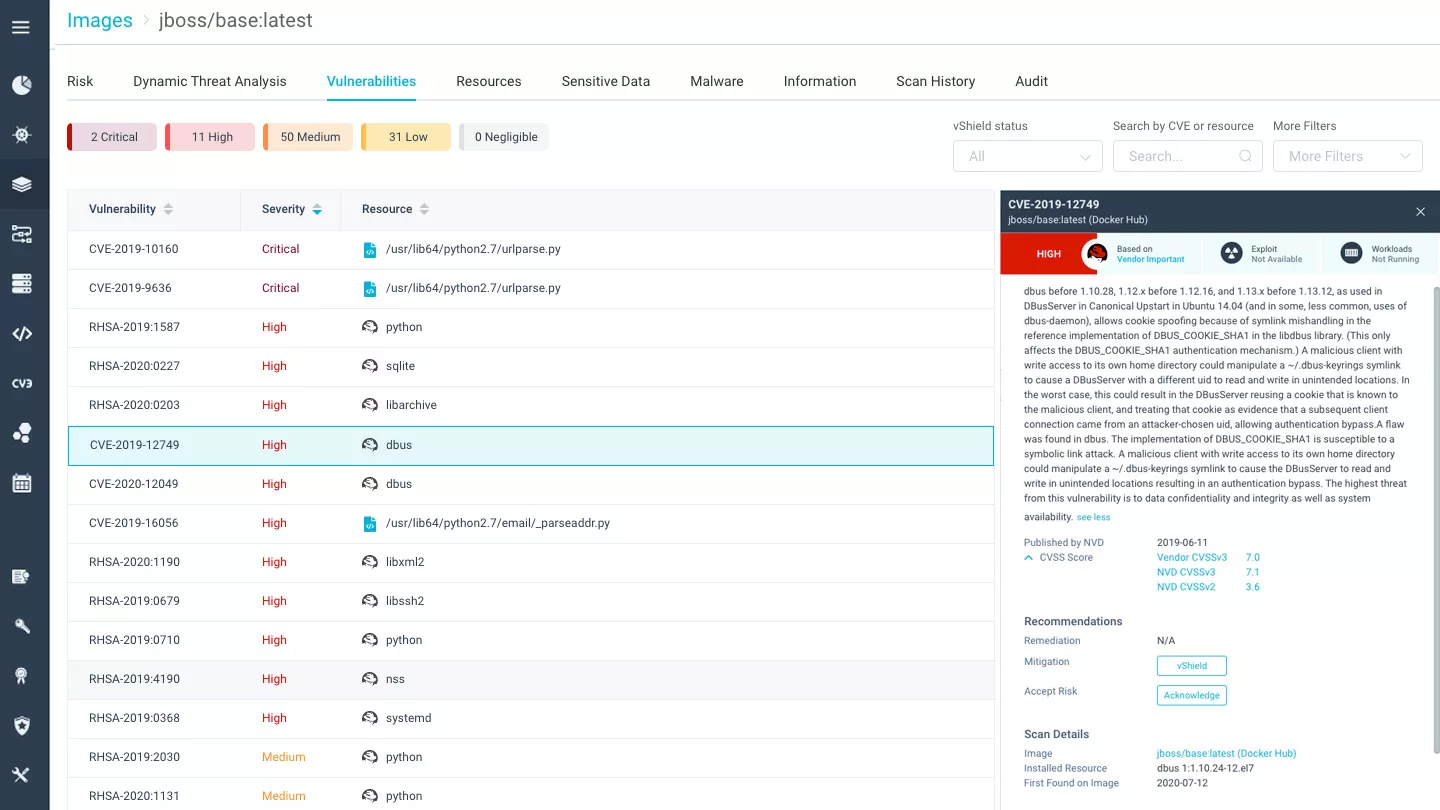
Aqua scans container images based on a constantly updated stream of aggregate sources of vulnerability data (CVEs, vendor advisories, and proprietary research), which ensures up-to-date, broad coverage while minimizing false positives. Additionally, find malware, embedded secrets, OSS licenses, and configuration issues in your images to further reduce the attack surface.
Dynamic Container Analysis
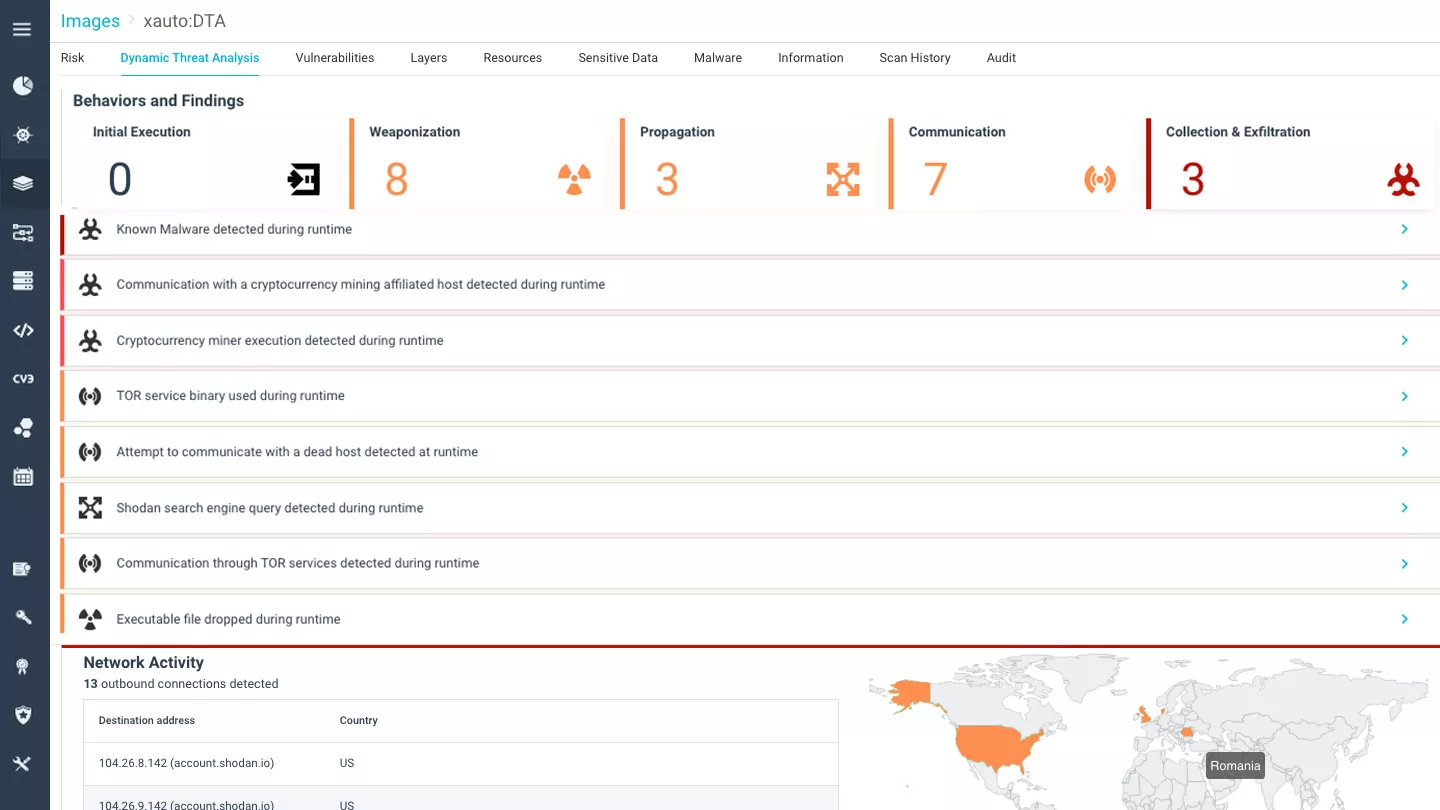
Discover sophisticated malware hidden in open source packages and 3rd party images, preventing attacks on your container-based applications, including credential theft, cryptocurrency mining, and data exfiltration. Aqua DTA analyzes container images at runtime, in a secure sandboxed environment, examining and tracing behavioral anomalies to uncover advanced malware that cannot be detected by static scanners.
Flexible Image Assurance
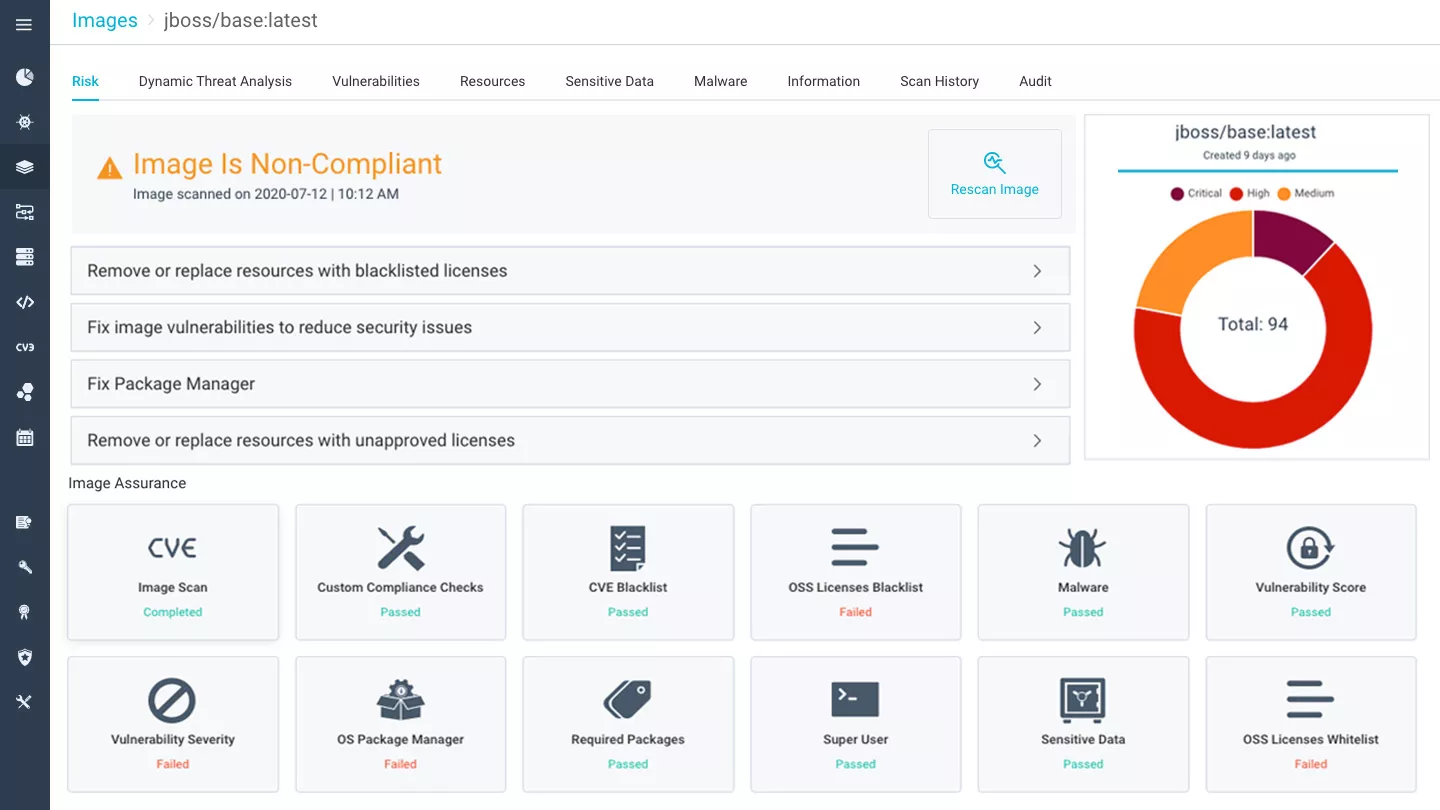
Aqua uses the results of both static and dynamic scanning to create flexible image assurance policies that determine which images would be allowed to progress through your pipeline and run in your clusters or hosts. Assurance policies are based on any combination of vulnerability score or severity, malware severity, the presence of sensitive data, use of root privileges or super-user permissions, and more.
Risk Explorer
Aqua Risk Explorer is a Kubernetes-native visualization and prioritization tool that show in real-time the risk factors within a Kubernetes cluster, namespace, deployment, node, and application. Use Risk Explorer to quickly get to the high-risk areas, be they vulnerable images, pods, or hosts, or suspicious network connections.

Vulnerability Shield (vShield)
Aqua vShield is a unique compensating control for unfixable vulnerabilities (or those that are difficult to remediate quickly). It acts as a virtual patch to prevent the exploitation of a specific vulnerability and provides visibility into such exploitation attempts. In organizations that are faced with large numbers of vulnerabilities, Aqua vShield helps to mitigate risk and to prioritize remediation efficiently.
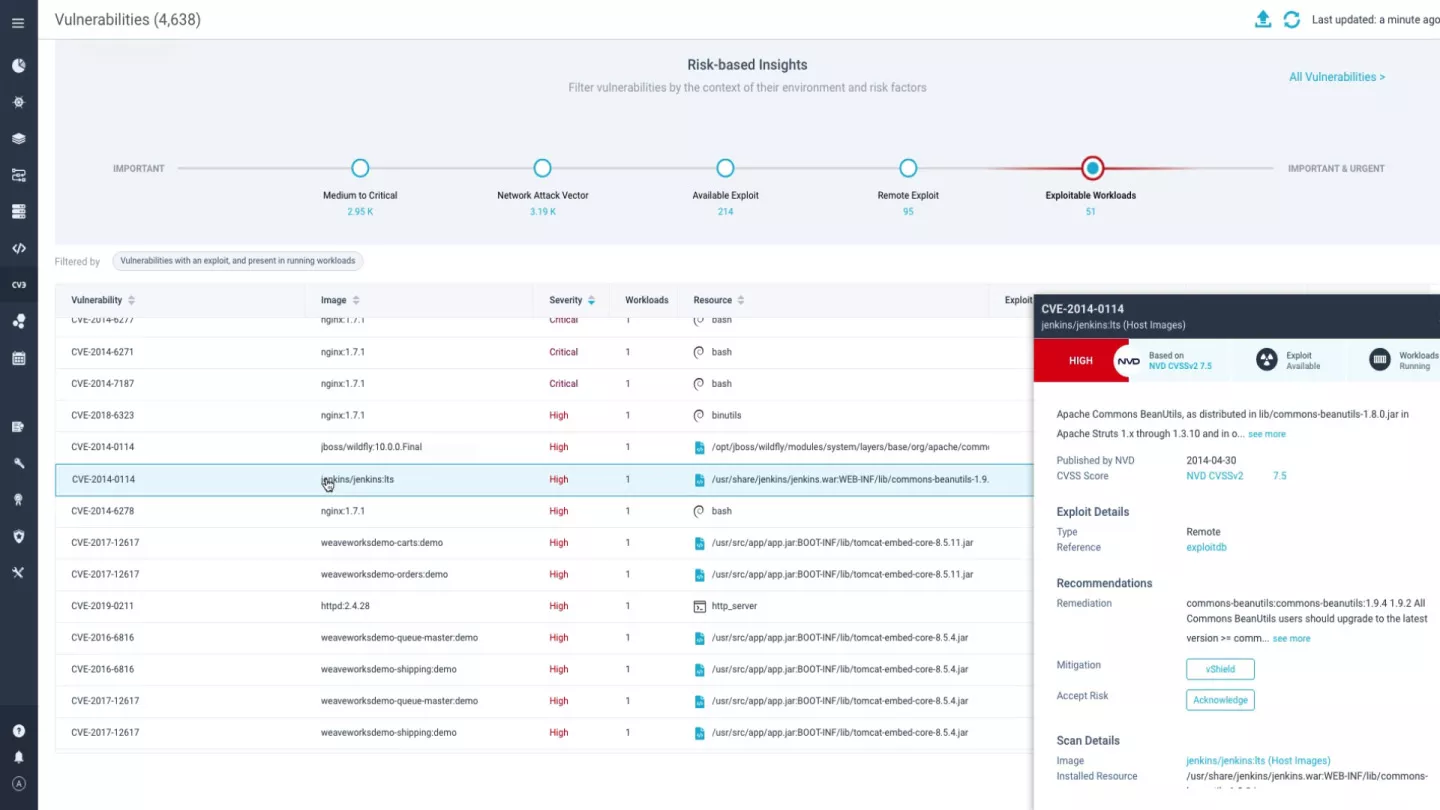
Drift Prevention and Runtime Policies
Based on an image’s digital signature, Aqua enforces the immutability of containers by preventing changes to a running container vis-à-vis its originating image. This easy-to-use feature can prevent a large array of attack vectors, including zero-day attacks. Additional runtime controls allow to detect and stop suspicious behaviors such as port scanning, connecting to IP address with bad reputation, and Fork Bomb denial of service attacks.
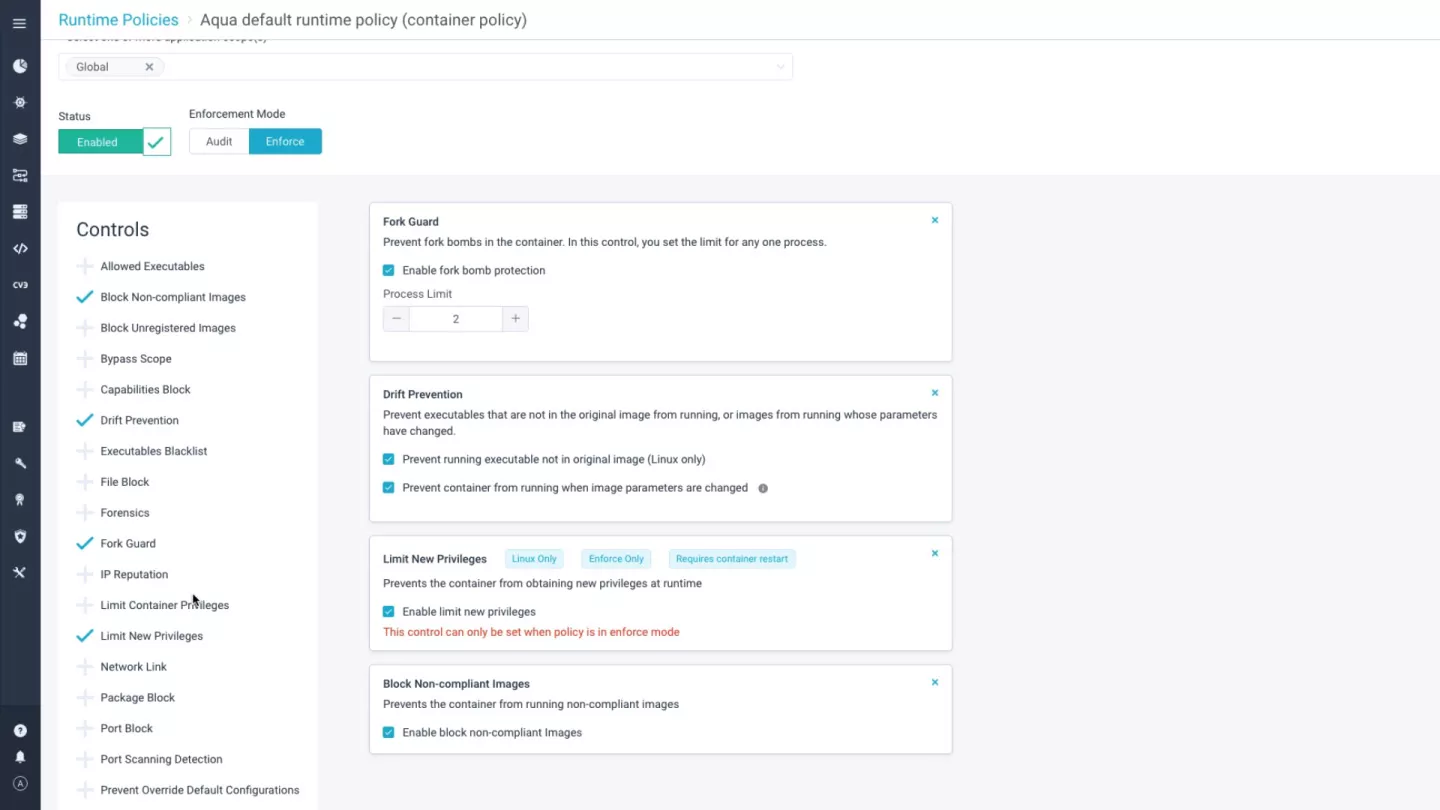
Behavioral Profiles
Aqua’s behavioral profiling uses advanced machine learning techniques to analyze a container’s behavior, creating a model that allows only observed behaviors and capabilities to be accessed. This includes file access, network access, volume mounts, and syscall usage. Reducing the container’s attack surface provides another layer of defense against attacks and privilege escalation attempts.
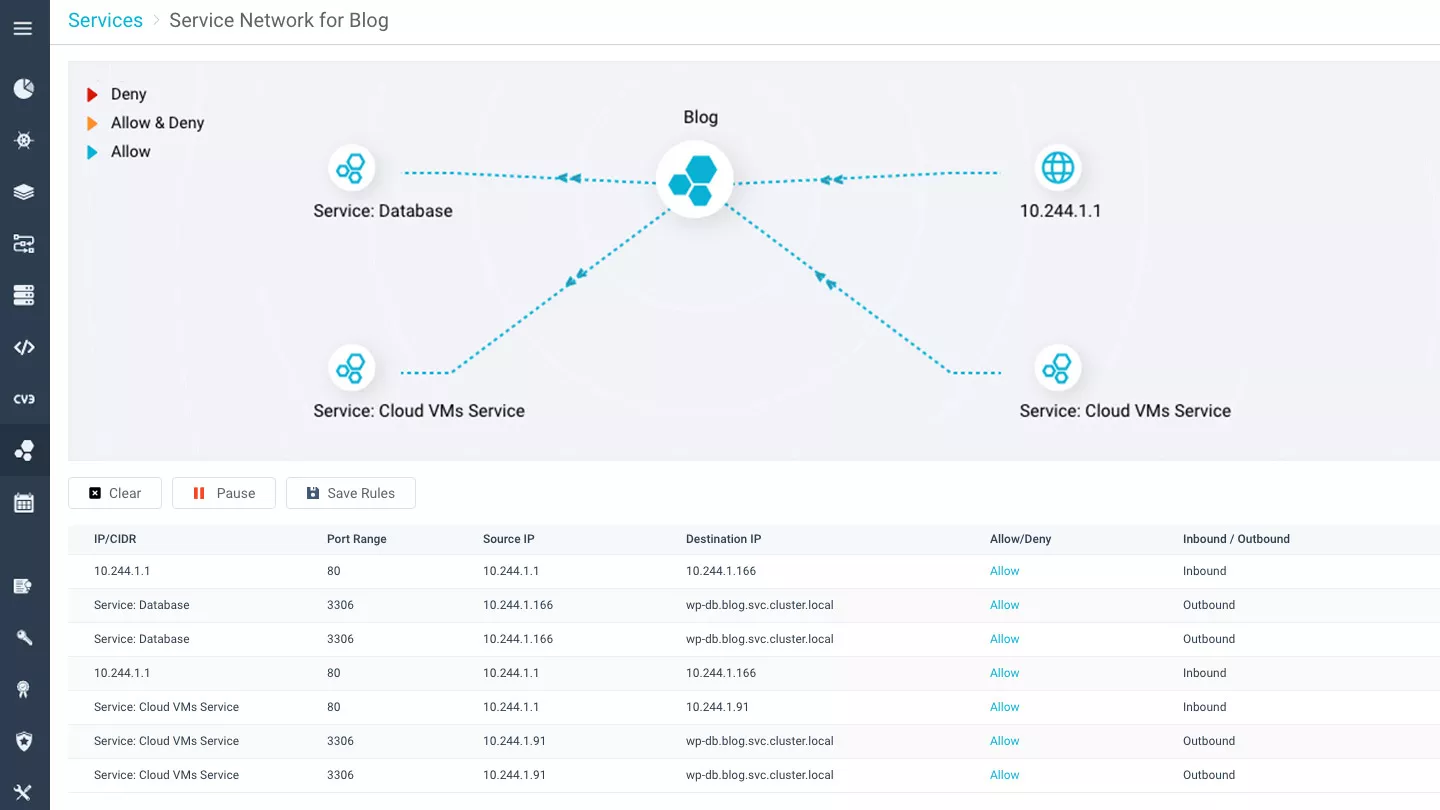
Workloads Firewall
Aqua limits the “blast radius” of attacks by limiting container networking to defined nano-segments based on application identity and context. Automatically discover network connections and get suggested contextual firewall rules that allow legitimate connections based on service identity, URLs or IPs. Block or alert on unauthorized network activity. The Aqua workloads firewall works seamlessly with K8s network plugins such as Weave and Flannel, and with service meshes such as Istio.
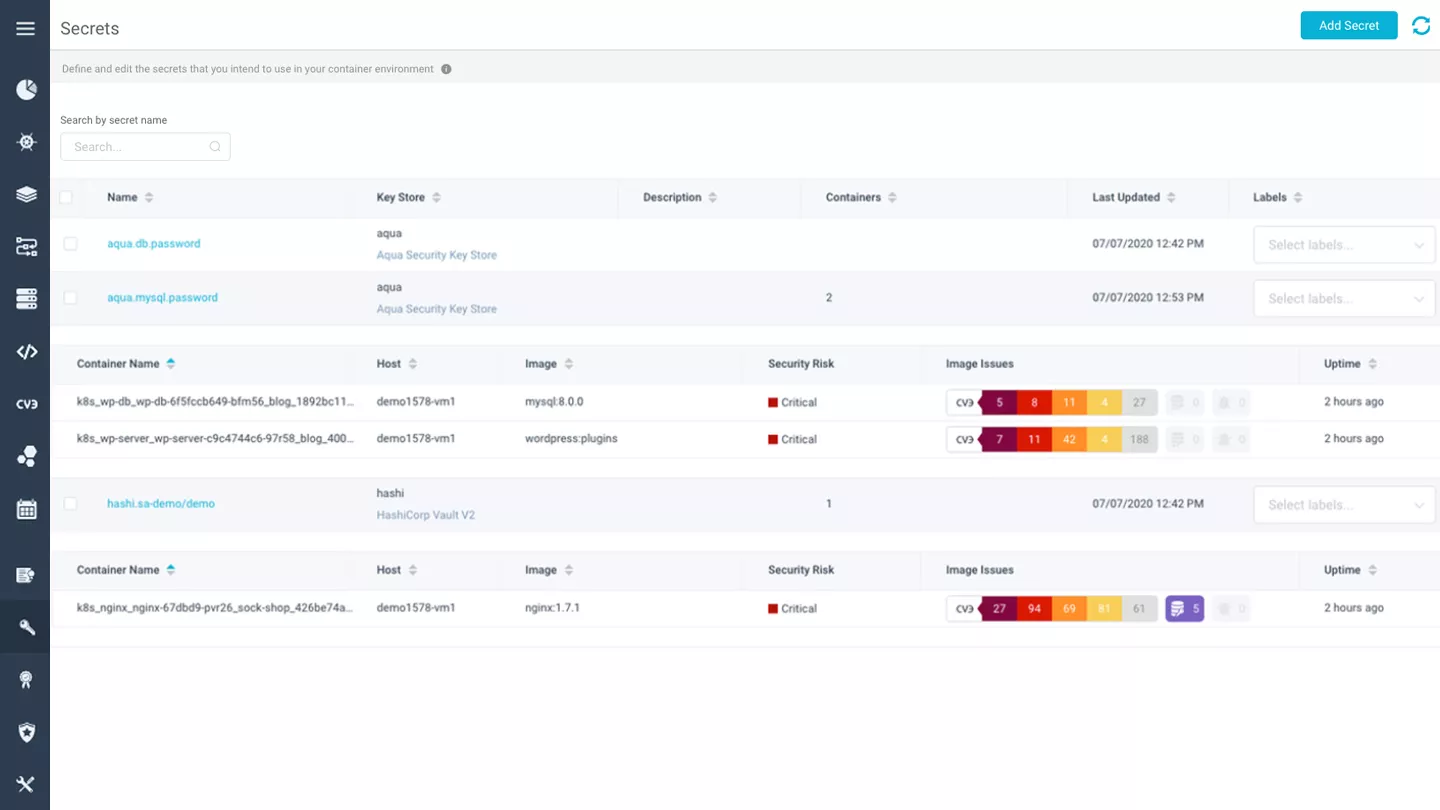
Secrets Injection
Aqua securely delivers secrets to containers at runtime, encrypted in transit and at rest, loading them in memory with no persistence on disk, where they are only visible to the container that needs them. Integrate with your existing enterprise vault, such as HashiCorp, CyberArk, AWS KMS or Azure Vault, and transparently update, revoke, and rotate secrets with no need to restart containers. We also give you visibility into which secrets are being used, and in which running containers.
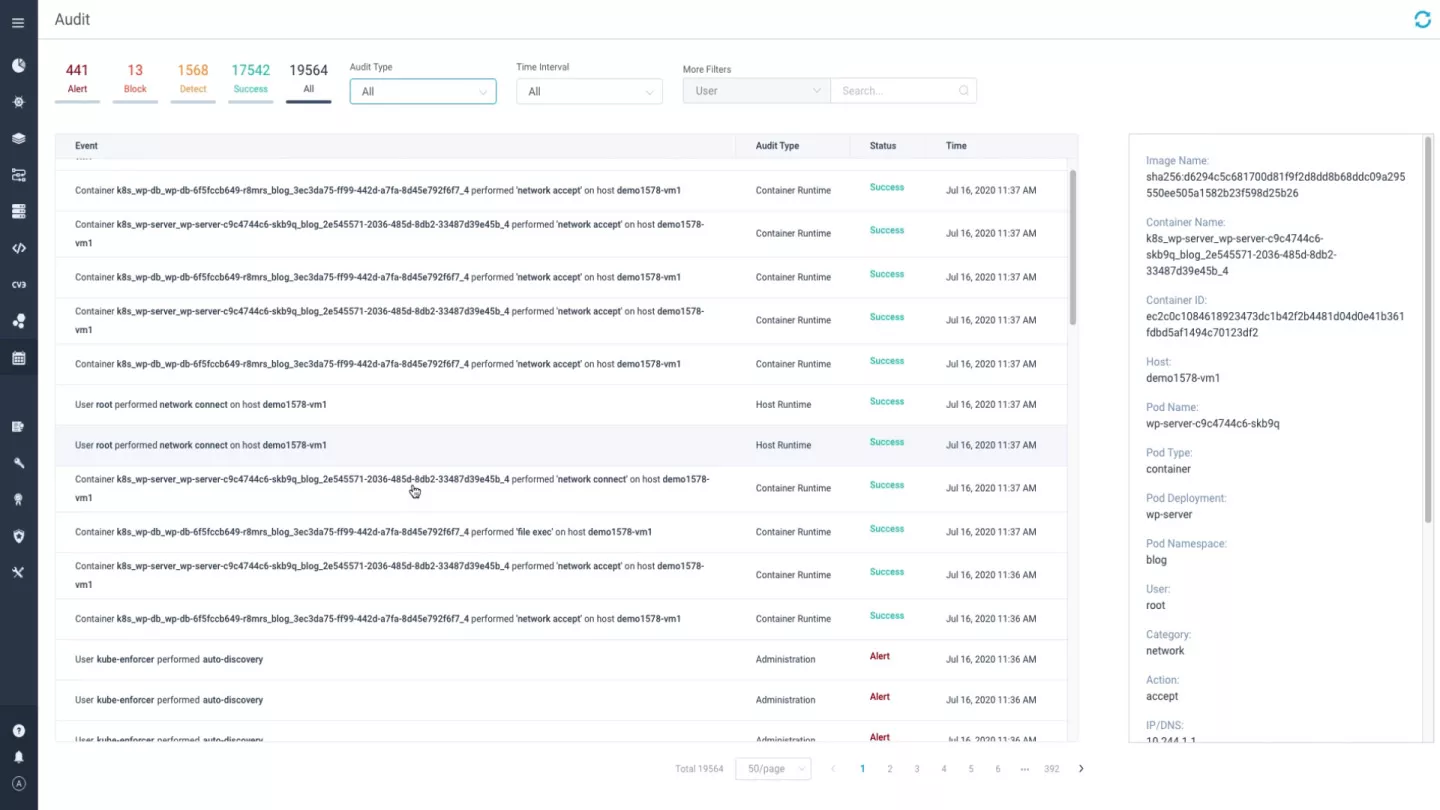
Auditing and Forensics
Aqua collects granular real-time data on images, containers, orchestrators, and hosts, providing data streams that are logged as events and can be sent via one of our many integrations into your SIEM, analytics or monitoring tools. When security policies are violated, Aqua collects all relevant metadata including user context, Kubernetes context (namespace, node, pod), image and registry context – to pinpoint the location and origin of the violation.