Dynamic Threat Analysis
The critical security sandbox layer for containers that weeds out advanced malware designed to activate in production. Advanced malware detection for every entry point from code to cloud.
Expose Hidden Malware in CI Builds and Registries
Aqua DTA scans designated images directly from your registries and CI pipelines, preventing malicious images from being deployed in production environments, and “shifting left” incident response.
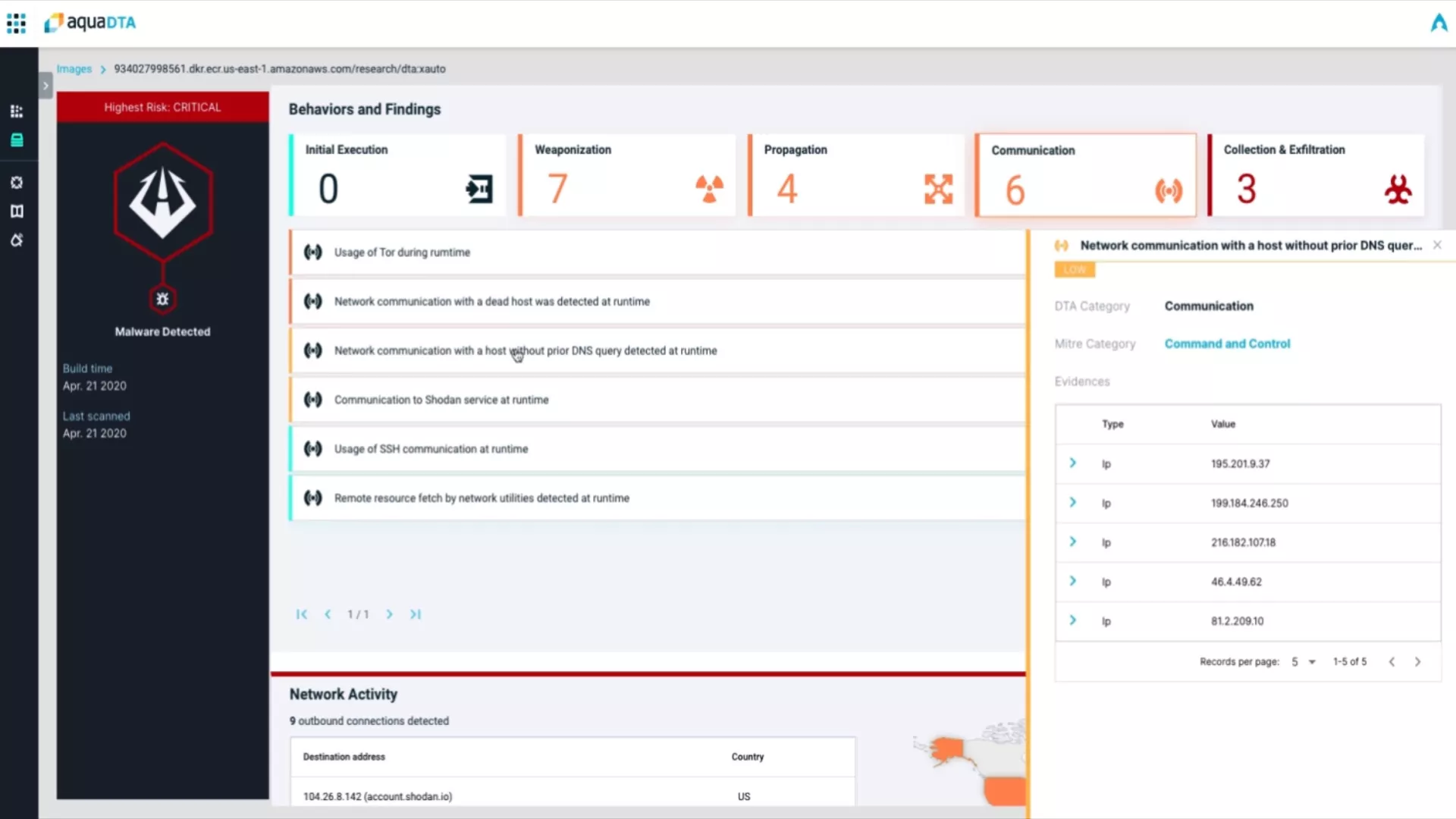
Get Detailed, Actionable Data on Anomalous Container Behavior
Detects clear indicators of compromise (IoCs) such as container escapes, reverse shell backdoors, malware, cryptocurrency miners, and code injection backdoors, and provides full tracing of all activities.
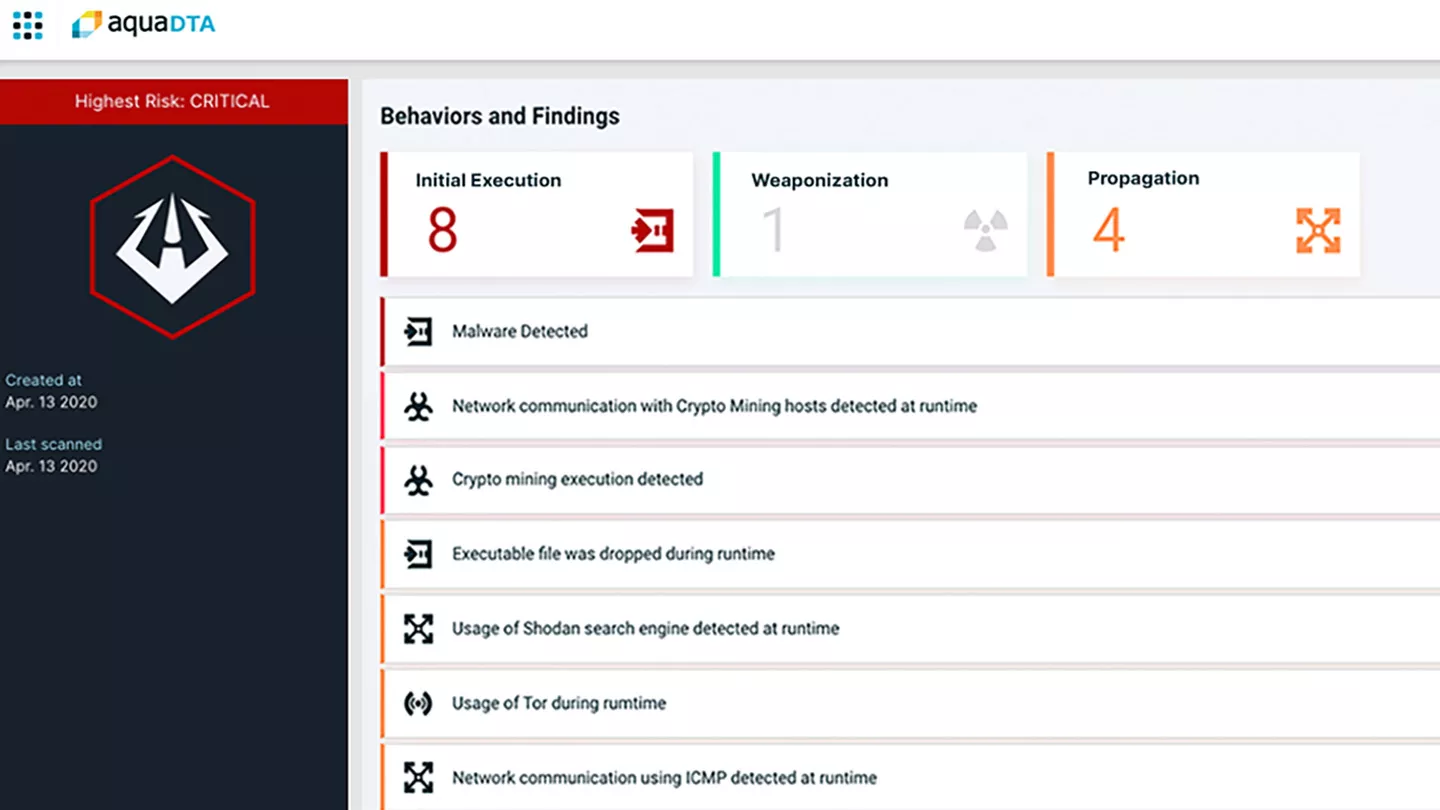
Understand Attacks Before They Happen
Aqua DTA classifies detected behaviors into categories of the MITRE ATT@CK framework, enabling SecOps and forensics teams to see the entire kill chain and understand and bolster weaknesses in their security infrastructure.

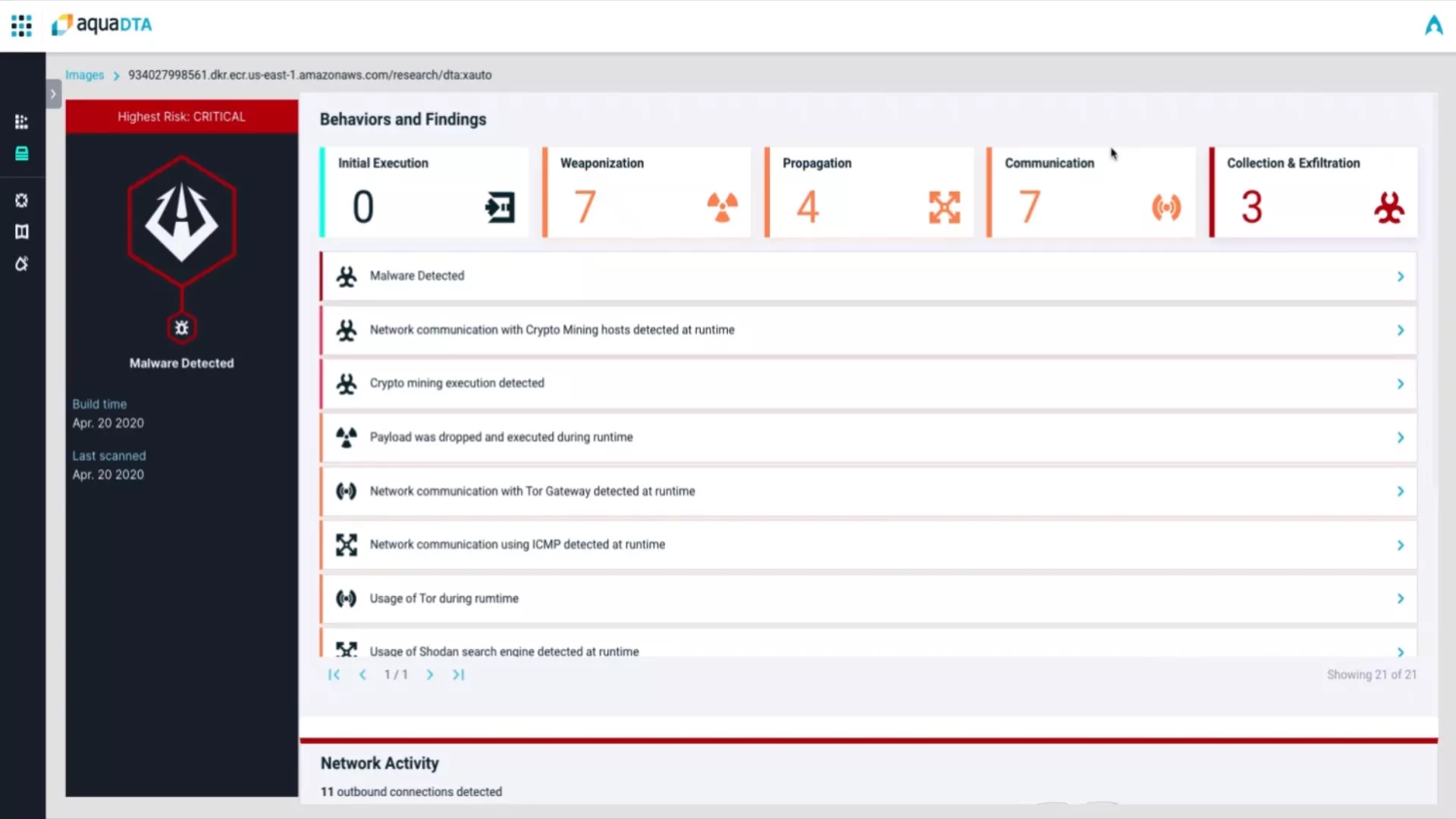
Map Suspicious Network Activity
Tracks and displays on a map all communications between the container and external destinations, including file downloads, C&C servers, and data exfiltration destinations.