Mainframes and containers represent two distinct yet impactful elements in today’s modern computing architecture. Mainframes are powerful, centralized computing systems known for their reliability, scalability, and ability to handle massive workloads. While containers, on the other hand, have emerged as a lightweight and flexible solution for deploying, scaling, and managing cloud native applications across various environments.
These two technologies complement each other enabling enterprise businesses ease of adapting a hybrid, highly scalable approach to their architectures, particularly in regulated industries such as finance, healthcare, and government where the use of public cloud-based Kubernetes infrastructure might not be the preferred approach.
In this blog we describe how Aqua protects containerized applications running on IBM Z-Series LinuxOne infrastructure, providing robust full lifecycle, dev to production security that can be managed uniformly across both private and public clouds. The enduring partnership between Aqua Security and IBM has spanned various divisions of IBM including, not limited to, IBM Consulting, IBM Power Systems. This robust alliance takes an exciting leap forward with the extension of support to IBM Z-Series mainframes
Applying the agility of containers the IBM Z-series mainframe
For many in the mainframe world the utilization of containerized architectures helps to solve the business challenges around agility and speed in developing new applications. The IBM Z-Series is a mainframe architecture that combines integrity, throughput, reliability while providing DevOps the modern access and capability of using containers to provide agility and speed of building applications in these environments.
The Z-series is used by many of the most highly regulated enterprise businesses to help them take advantage of agile modern applications and DevOps practices. Allowing for the building (or rebuilding) of containerizing applications for many of the world’s largest financial institutions who rely on the powerful IBM Z series for running their applications on premises.
Challenges arise though around securing such hybrid architectures, as traditional means of security for mainframe architectures do not identify vulnerabilities in images and hosts, or misconfigurations of the container and orchestration layer.
While the IBM Z-Series provides its clients the ability to maintain robust performance and enable faster development, paired with significant security for encryption, there is still a need to protect applications at the container workload and OS level, providing the ability to detect, prevent, and react to threats.
Building applications in the cloud is different, security should be too. Recognizing the different challenges with securing ephemeral containers and orchestration layers, IBM turned to Aqua as the only solution robust enough to deliver enterprise security for the mainframe at scale.
Challenges of securing containers on mainframe
Container security requires a different approach compared to security in traditional environments. This is something Aqua is keenly aware of as container security has been our focus for over 8 years. Containerized environments, typically orchestrated by systems like Kubernetes, have a fundamentally different architecture compared to traditional VM-based infrastructures. While organizations leverage OpenShift for management and scaling their enterprise container deployments on premises, it lacks the ability to enforce any type of vulnerability or risk policy of images during development or runtime.
Applying security is so difficult because of the transitory use, often being created and dismantled in response to demand. This rapid change in the environment can be challenging for traditional security tools to keep up with, as they are designed for more static environments.
It is the complexity and dynamic nature of a containerized environment that requires container security to be fully automated. An important step to automating security and embedding it into all stages of the software development lifecycle (SDLC) is to implement security controls as part of the continuous delivery lifecycle used to build and release containerized applications.
Aqua’s solution spans the entire SDLC, securing the build pipeline, images, host machines, container runtimes (such as Docker or containerd), container platforms and orchestrators (such as Kubernetes), and application layers.
Simplifying security with better risk intelligence
Risk intelligence is a decisive part of container security, making this the most important tactic for many security and DevOps teams dealing with containerized workflows. Images are often open source, so continuously validating each image for changes in health, vulnerabilities, and licensing is essential. Equally as important are the container and orchestrator configurations, which create easy targets if deployed misconfigured to production.
The Aqua platform is RedHat certified for both vulnerability scanning and OpenShift container security. It is unique in that one scanner can be used to uncover all risk without the disparities of results from different scanners, creating a flood of vulnerability false positives that bog down both development and security. Combined with threat research from Nautilus, teams are armed with deeper risk analysis than what is available through scanning alone. This comprehensive view before deployment is then run through intelligent policies within Aqua that automate the acceptance or denial of a container image into production.
Aqua governance policies are the secret to scaling and come out of the box ready to tackle HIPAA, PCII, and more. But as every development process is unique, Aqua policies are too and can be customized according to:
- The workload: VM images, container images, serverless functions
- The risk: Vulnerabilities, embedded secrets, open source license issues, misconfigurations, secrets, malware
- Role based access: Type of permission provisioned
- Scanning interval and phase of lifecycle: on commit or at deployment in the Registry or CI/CD pipeline
Preventing container risk before production
Aqua’s comprehensive stance on container security integrates both preventive measures and risk detection of open source risk in containerized environments. Aqua can be deployed natively on RedHat OpenShift for both LinuxOne and Windows containers. Providing governance over the image before and after deployment that is in line with customizable security controls.
This continuous intelligence of risk before and after deployment enhances security’s ability to “find the needle in the needle stack” and enables a risk-based strategy for prevention, detection, and remediation.
Tailored for the ephemeral nature of containers, Aqua automates pre-deployment scanning, offering an optimized method to monitor for any file changes. It utilizes a single scanner to identify vulnerabilities in the image and configurations of the container and orchestrator before deployment. This encompasses meticulous scanning of multiple layers within the container, whether in the registry or the CI/CD pipeline, ensuring a proactive security approach well before reaching the production stage.
Below is a view of how a container on Linux/s390x is assessed for risk and analyzed for risk. The risk findings are then leveraged within Aqua policies for acceptance into production or relayed back to development for action.
Image 1: Linux/s390x is assessed for risk and analyzed for risk
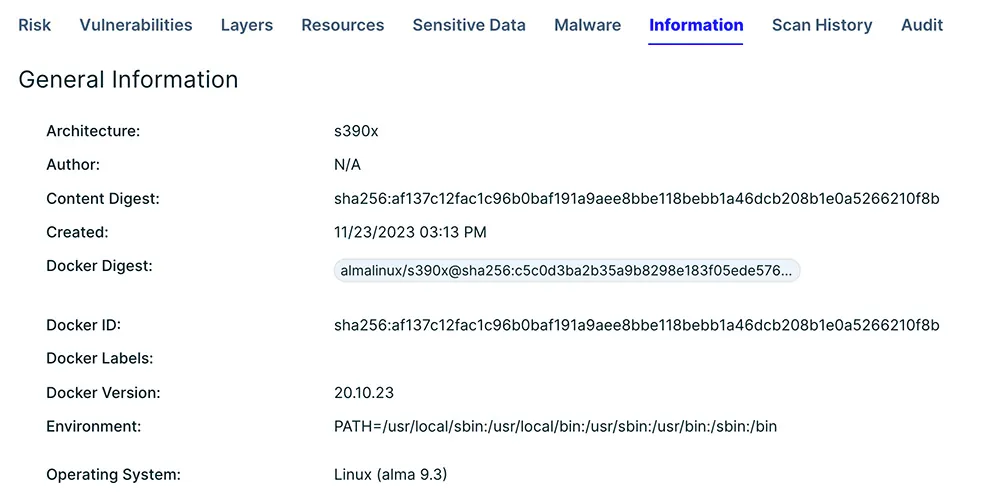
Image 2: Findings leveraged within Aqua policies for acceptance into production
Runtime support in Kubernetes environments
A key principle of zero-day prevention is the concept of immutability. Immutability means that a container won’t be modified during its life: no updates, no patches, no configuration changes. If a change does happen, it is considered drift. It is reasonable to assume with drift comes the risk of attack.
Throughout this blog we have spoken about the challenge around securing container environments stemming from their complexity and the lack of real-time visibility into what is going on inside containers pre-deployment. But what about after, what happens when the application is running? Some of the most prolific attacks, including Log4j vulnerability, Spring4Shell, have shown that detecting threats at runtime is critical in thwarting zero-day attacks. This is why Aqua will deliver key runtime capabilities such as drift prevention and malware detection.
How drift prevention works within Aqua
Drift prevention is used to prevent exposure and attacks at runtime by following security best practices of immutability to ensure containers aren’t modified after deployment in production. It prohibits any changes to the image after it is instantiated into a container and blocks everything that wasn’t part of the original image – without killing a container itself. Thus, protecting workloads against zero-day attacks by detecting and blocking known and unknown malware, zero-day exploits, and internal threats that can’t be caught early in the application life cycle.
Here is a quick example of how drift prevention works within the Aqua platform. Below is an image of the incident screen, it shows all the runtime findings in the environment, whether behavioral or based off a runtime policy to control drift in the running of the application.
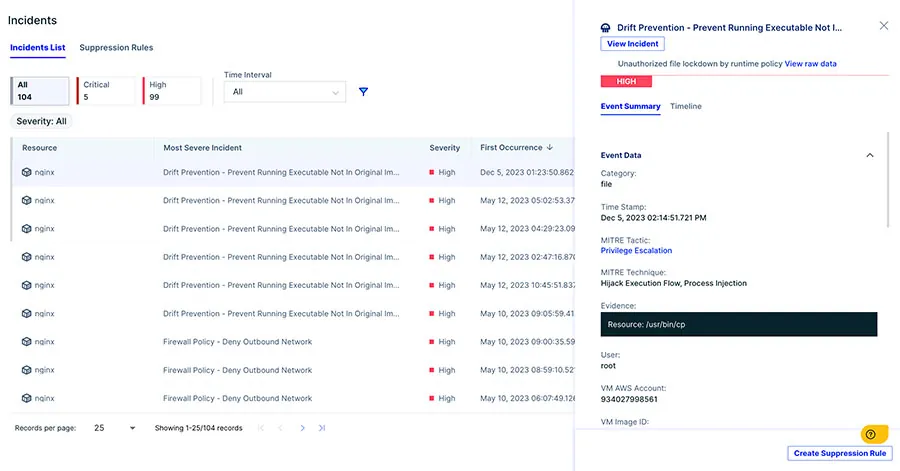
Image 3: Incident Screen showing all the runtime findings in the environment
This next image shows the timeline of events leading up to the drift event. The user can see that a privilege change was executed and access to the container gained, triggering the alert and containment.
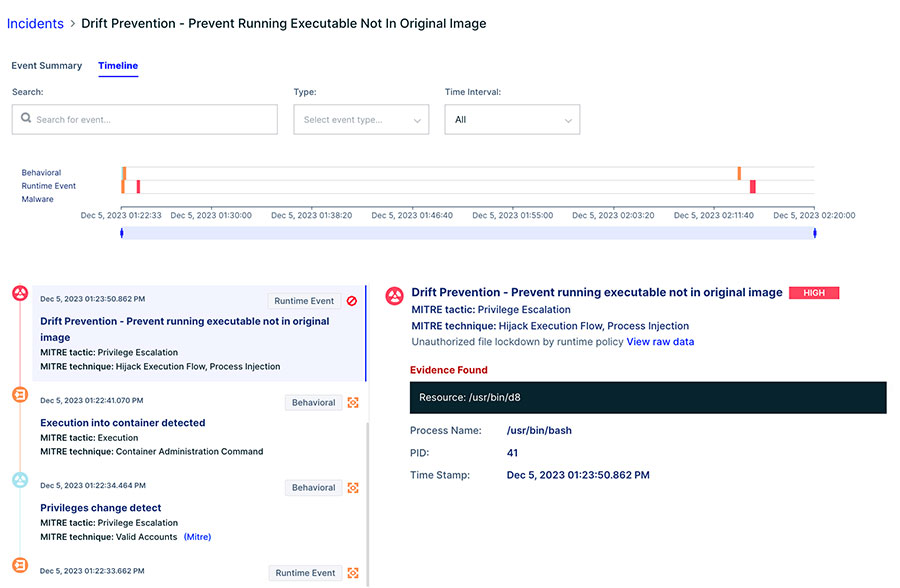
Image 4: Timeline of a drift event, showing the dropping a new executable and trying to execute it
Protecting against malware in runtime
Malware is always a prominent threat. Aqua ensures ongoing vigilance with malware scanning of VMs and Kubernetes hosts. This process happens automatically and is defined as part of the Host Assurance Policy. Detected malware results in alerts and the marking of the VM as non-compliant, ensuring immediate attention and action.
The following screenshot shows that malware is detected and displayed for each VM in the Workloads > VMs page.
Image 5: Malware is detected and displayed for each VM in the Workloads > VMs page
Protecting environments, no matter where they run
The Aqua Platform unifies cloud security and vulnerability management across complex environments so that these highly regulated industries can minimize the application attack surface and stop attacks by creating a single source of truth, enabling seamless collaboration across teams, and giving everyone the context to prioritize and fix what’s most important.
Many banks rely on Aqua to secure containerized environments. This dedication not only confirms our commitment to strengthen security across application modernization initiatives, but also confirms the value of our integrated partnership with IBM. It highlights our expertise and experience providing cloud-native security for regulated industries and the technical integration ensures resilience for organizations embracing container technologies.
The infrastructure surrounding containers is complex on many levels Aqua’s integrated platform offers full lifecycle container security protection, to reduce risk and prove compliance of containerized applications, harden Kubernetes clusters, mitigate attacks and protect containers across all platforms and formats. Named as an Outperformer and Leader in innovation by the GigaOm Radar for Container Security it is this quote from the report that sums up Aqua’s commitment, “The Aqua Platform’s implementation is well done. Most customers will find the product zeroes in on all the right things to lock down the container environment. If it is a likely need in the average enterprise’s container security or compliance strategy, Aqua supports it.”
To visit www.aquasec.com/demo to learn more.

