Advanced Code-to-Cloud Vulnerability Management
Leverage deep runtime context to reduce vulnerability noise, focus on what matters, and fix issues fast
Too many vulnerabilities? Let's Talk.Find and fix vulnerabilities early
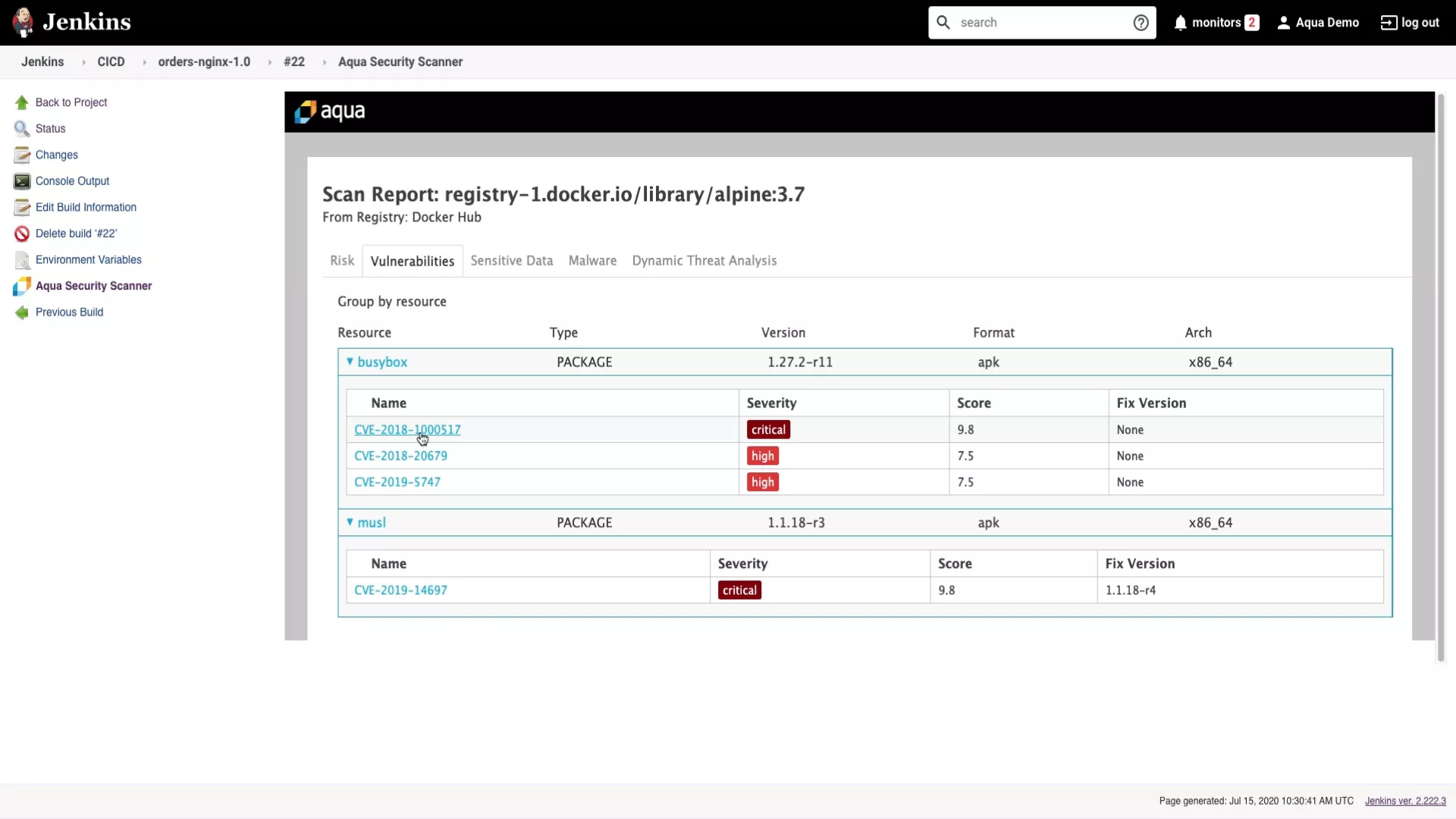
Prevent known vulnerabilities from reaching production by finding and fixing them early in the application lifecycle and setting up assurance policies to ship clean code. Continuously uncover vulnerabilities in your code, container images, third-party components, open source packages and dependencies using the most accurate, universal Aqua Trivy scanner, enabling developers to address identified issues during the build stage.
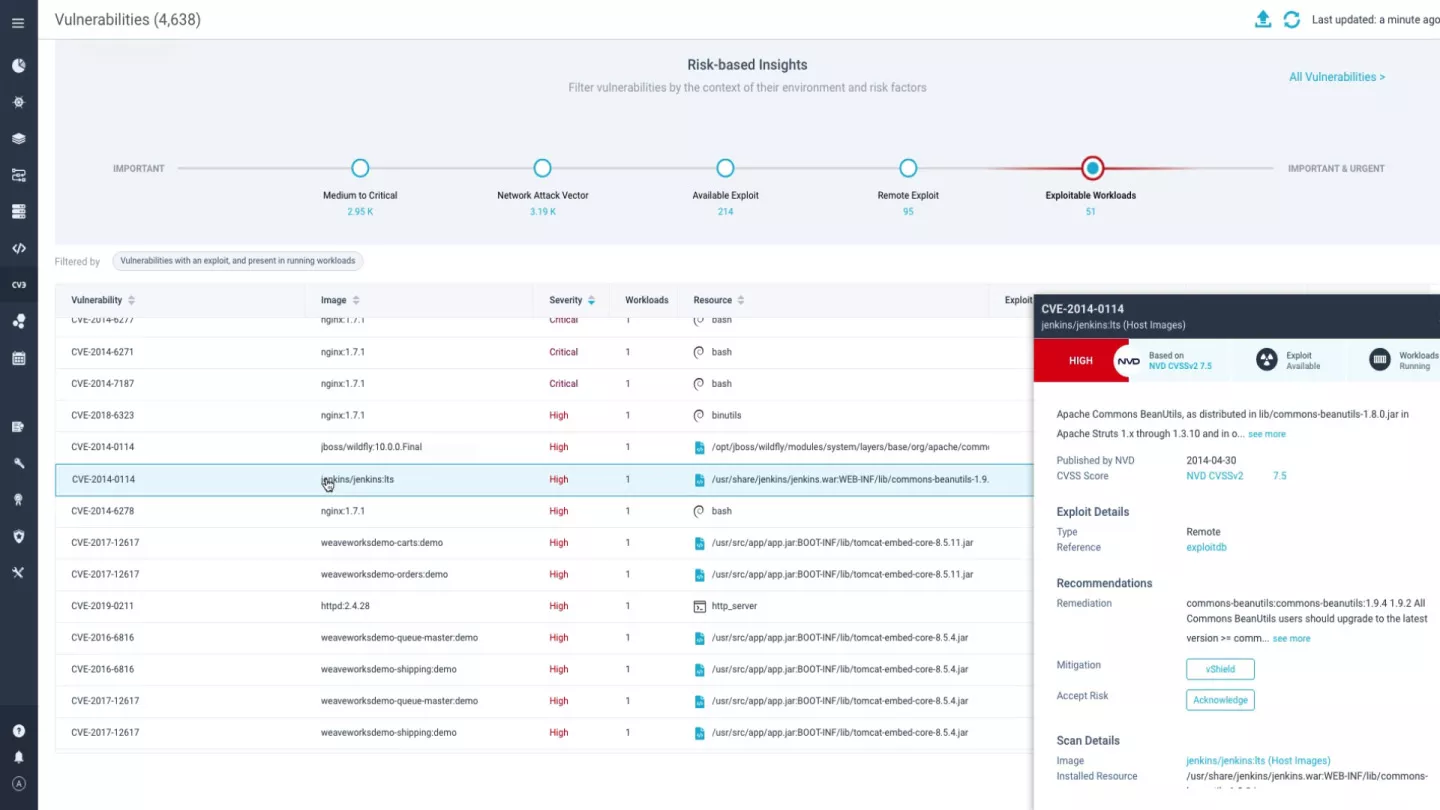
Rigorously prioritize issues
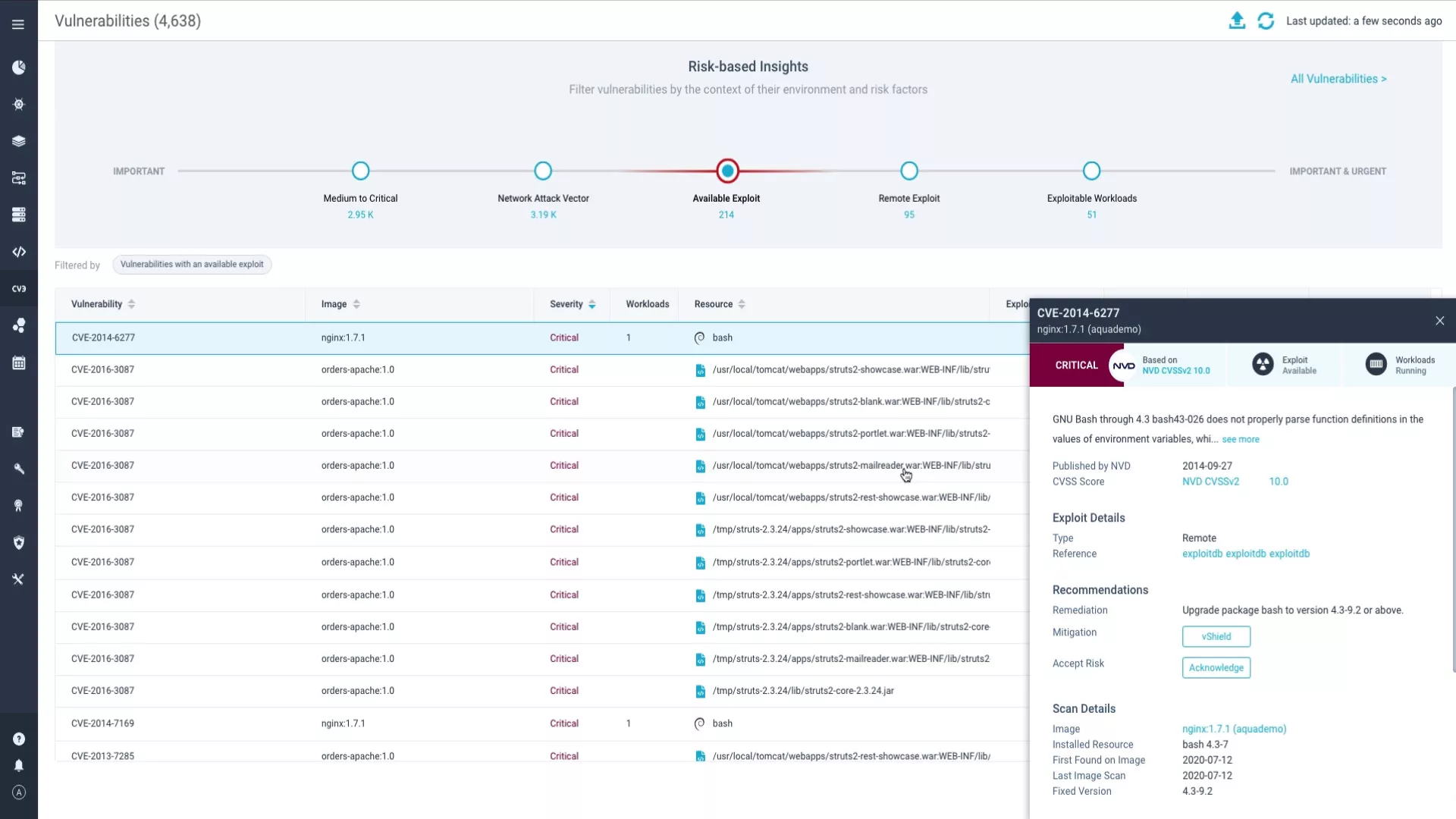
Filter thousands of vulnerabilities by leveraging both code and runtime context to determine top priority issues that pose greatest risk and require action. Assess and quickly understand the impact of new vulnerabilities on your environment with rich contextual insights, such as reachability, EPSS, actively running packages, available exploits, and more to focus only on the vulnerabilities that can be exploited.
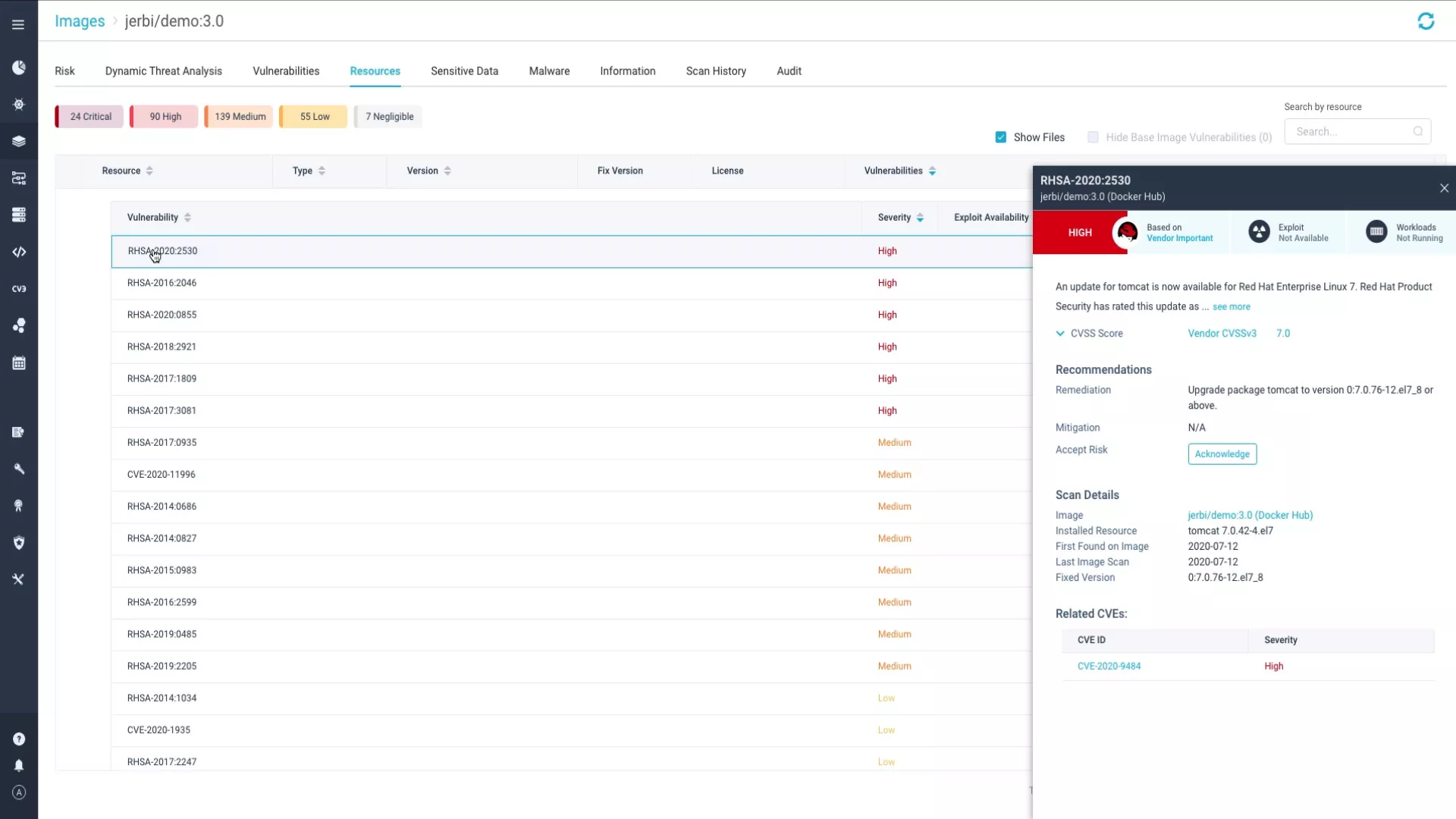
Remediate without hassle
Easily trace vulnerabilities from code to cloud, pinpointing the exact line of code where they originated from. Empower developers to fix issues fast in their own workflow by giving them the full context of where the code gets run and automatically generating a pull request to the responsible owner. Use response policies and AI-guided remediation advice to deploy a patch and resolve issues swiftly.
Shield in runtime
Prevent exploitation attempts and mitigate vulnerabilities without a fix by applying compensating controls such as vShield (virtual patch). Enhance protection against exploiting vulnerabilities by enforcing granular runtime policies to detect and alert on zero-day attacks, drift, cryptocurrency mining, malware, and other threats in real time.
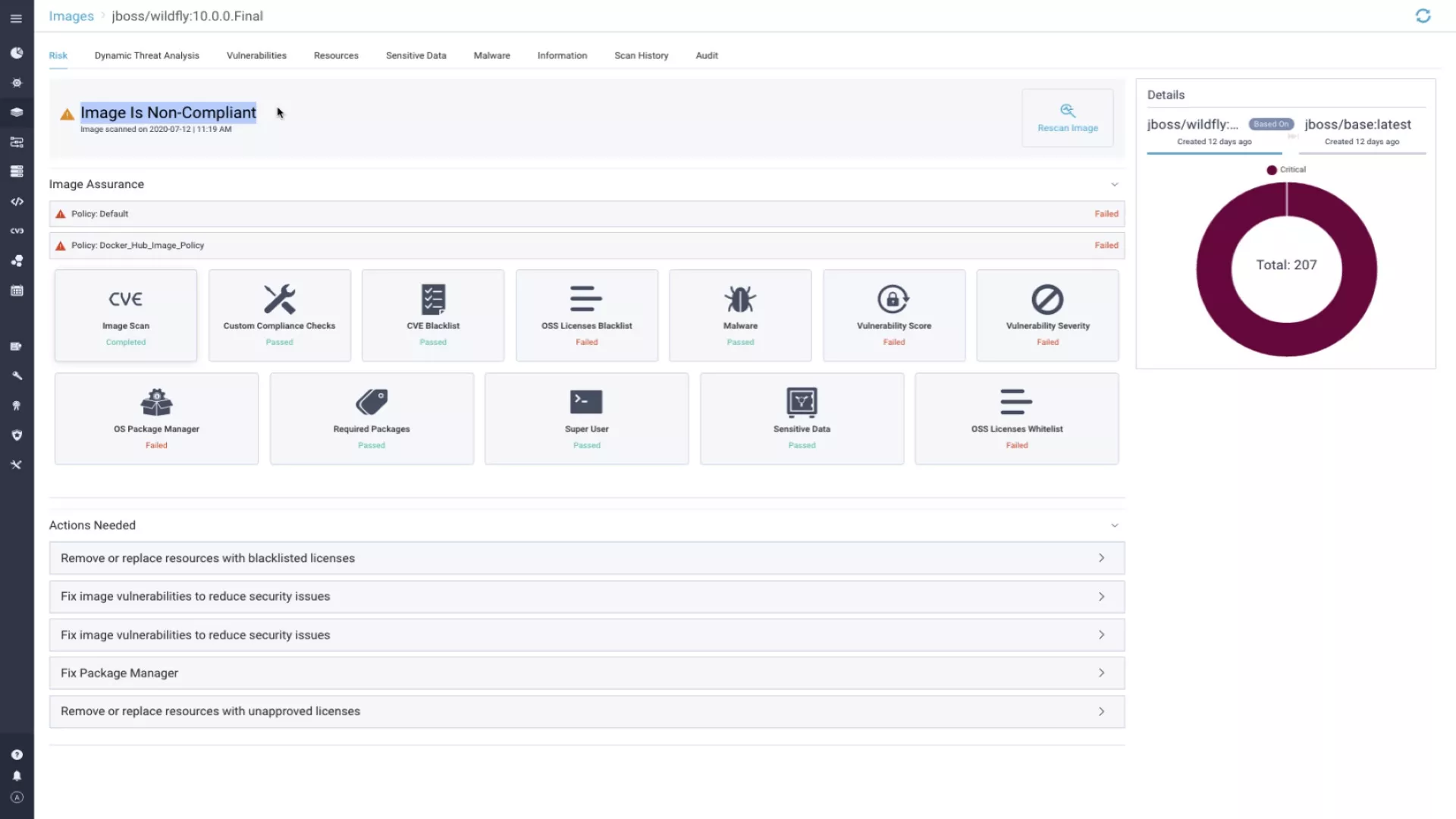
Manage vulnerability posture with ease
Continuously manage, assess, and report on vulnerabilities at scale and throughout the entire application lifecycle, from development to production, across your multi-cloud environment, driving better decisions and ensuring that critical issues are addressed on time. Track key metrics over time, such as the average age of vulnerabilities and MTTR, or export vulnerability findings into internal systems for further analysis.