Holistic Kubernetes Security for the Enterprise
Tame the complexity of Kubernetes security with KSPM (Kubernetes Security Posture Management) and advanced Kubernetes runtime protection. Leverage Kubernetes-native capabilities to attain policy-driven, full lifecycle protection and compliance for your K8s applications.
See Kubernetes Security in ActionVisualize and Prioritize Risks in your Cluster
Interact with a dynamic map of your running K8s clusters that highlights and rates Kubernetes security risks. Get real-time visibility into namespaces, deployments, nodes (hosts), containers and the images they came from, as well as network connections between and within namespaces.

Control Workload Admission Using K8s Attributes
Shift-left workload security and gain a clear perspective of your workload’s security posture. Powered by Open Policy Agent (OPA), new Kubernetes Assurance Policies allow you to apply dozens of out-of-the-box rules or add custom rules using Rego expressions.
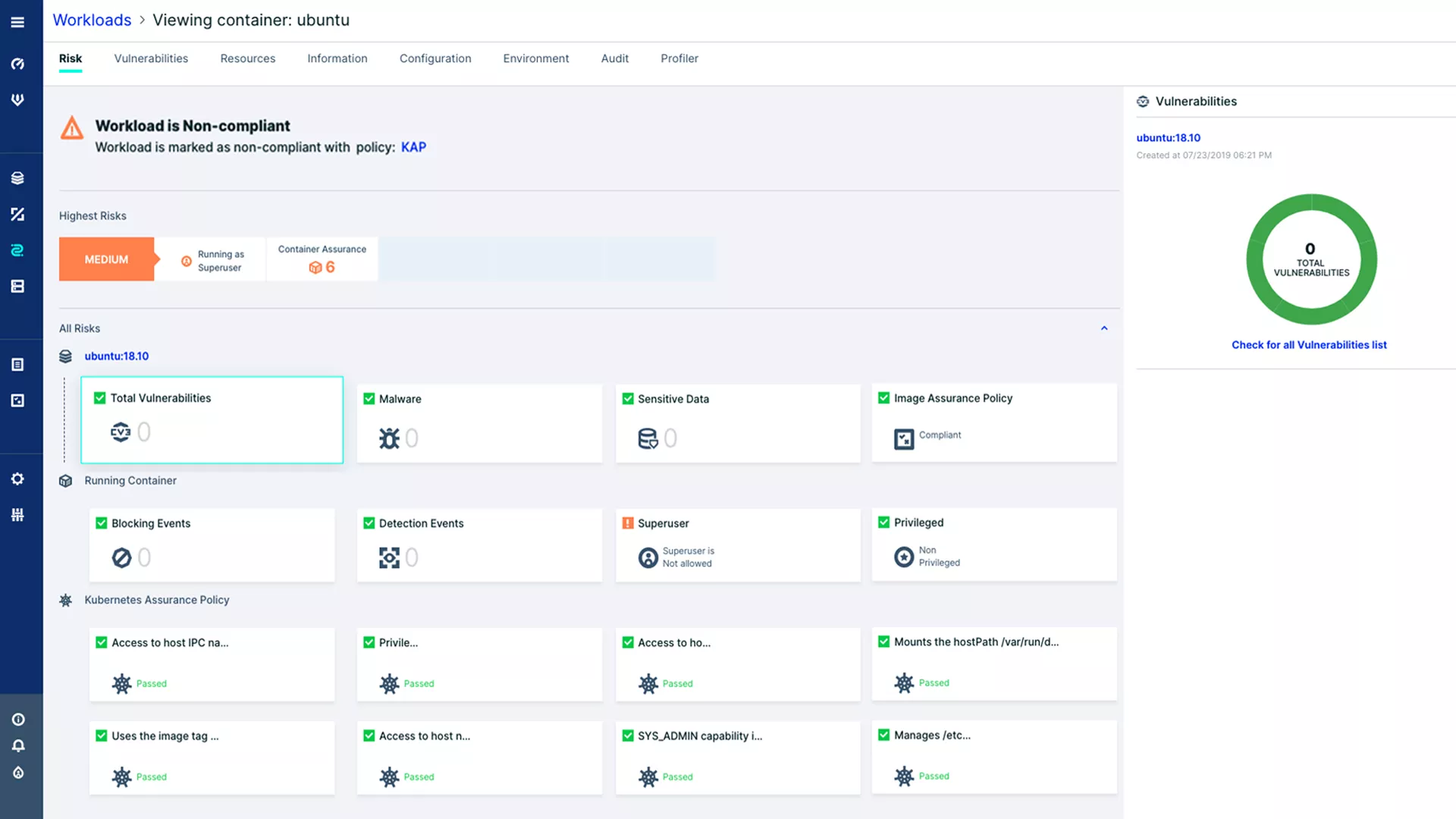
Determine the Compliance of Kubernetes Workloads
Gain control over the security posture of your Kubernetes workloads based on both image contents and configuration, as well as Pod attributes. Works in conjunction with Aqua’s Image Assurance Policies to prevent the deployment of unsafe and non-compliant workloads.
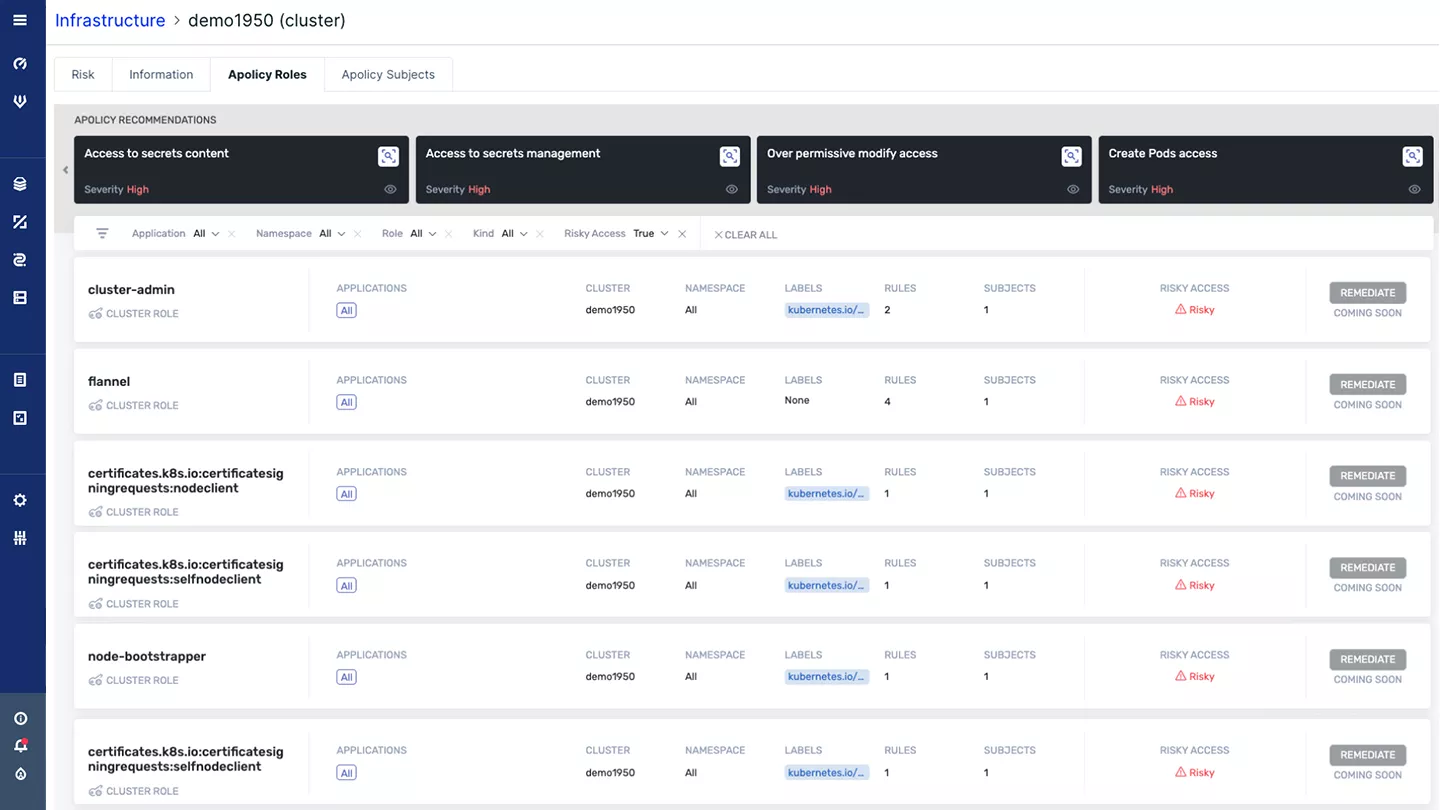
Achieve Least Privilege Access in Kubernetes
Assess the permissions and privileges of users and subjects in K8s against research-based best practices and get remediation advice to minimize exposure. Continuously reduce the risk of over-provisioned roles and service account privileges, diminishing the need for Kubernetes security expertise.
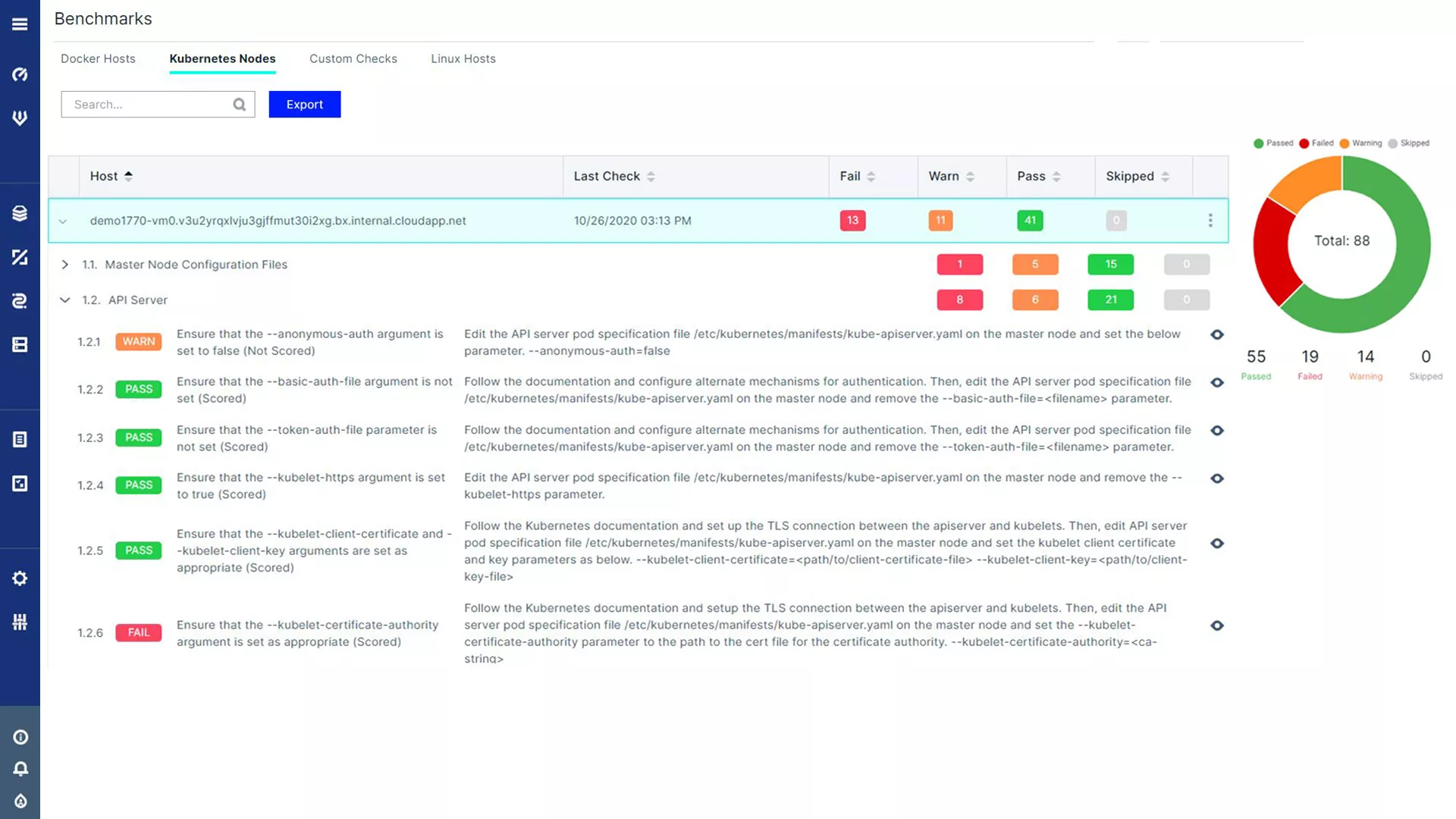
CIS Kubernetes Benchmark Checks
Automate compliance checks of your Kubernetes environment according to the CIS Kubernetes Benchmark with more than 100 individual checks, daily scans, and a detailed report of the findings. Leverages Aqua’s widely-used open source Kube-Bench tool.
Kubernetes Cluster Penetration Testing
Run automated pen-testing of Kubernetes clusters, identifying weaknesses against real-world attack vectors. Complement configuration checks and best practices by defending against attacks in the wild. Leverages Aqua’s industry leading open source Kube-Hunter tool.

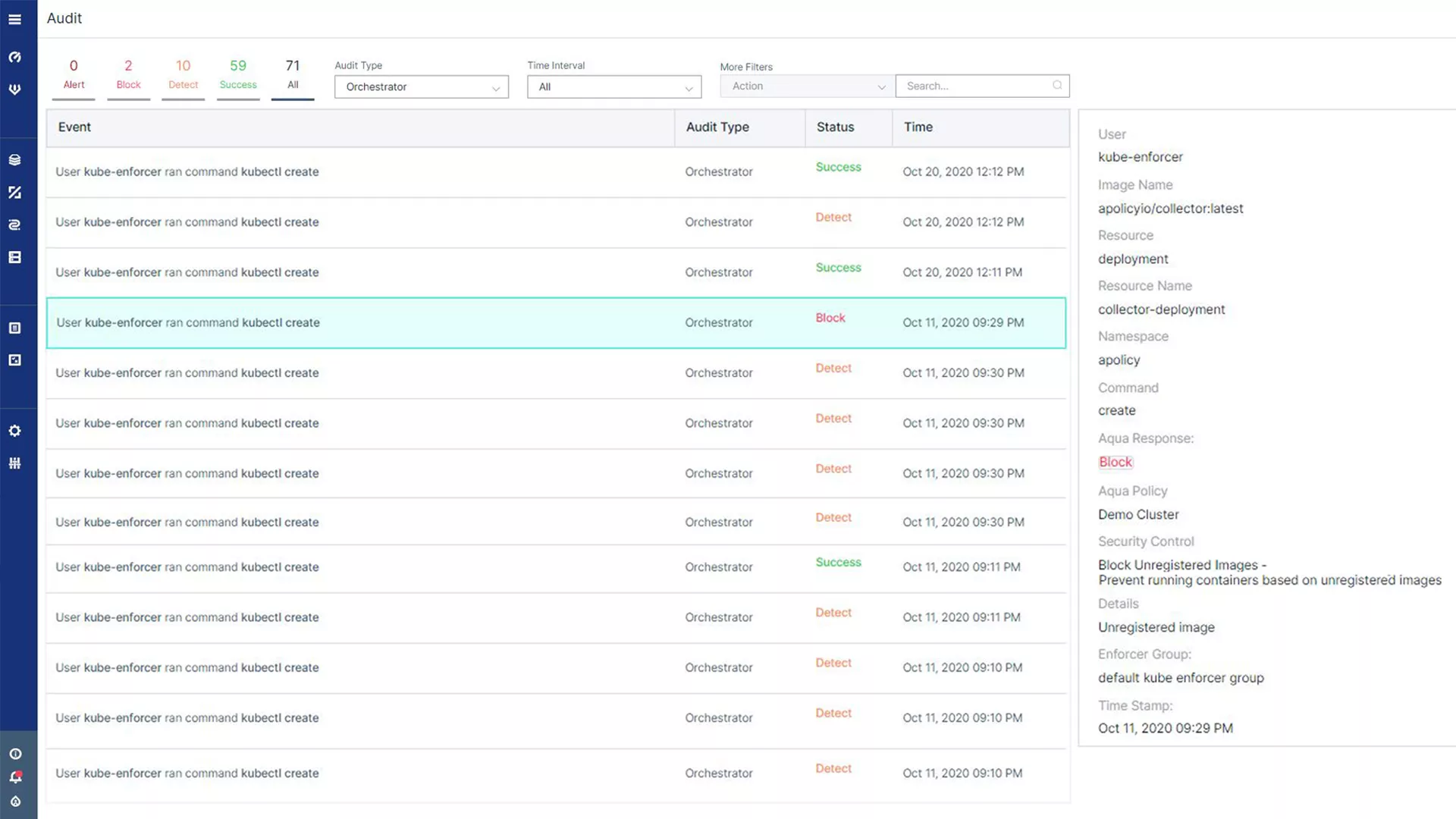
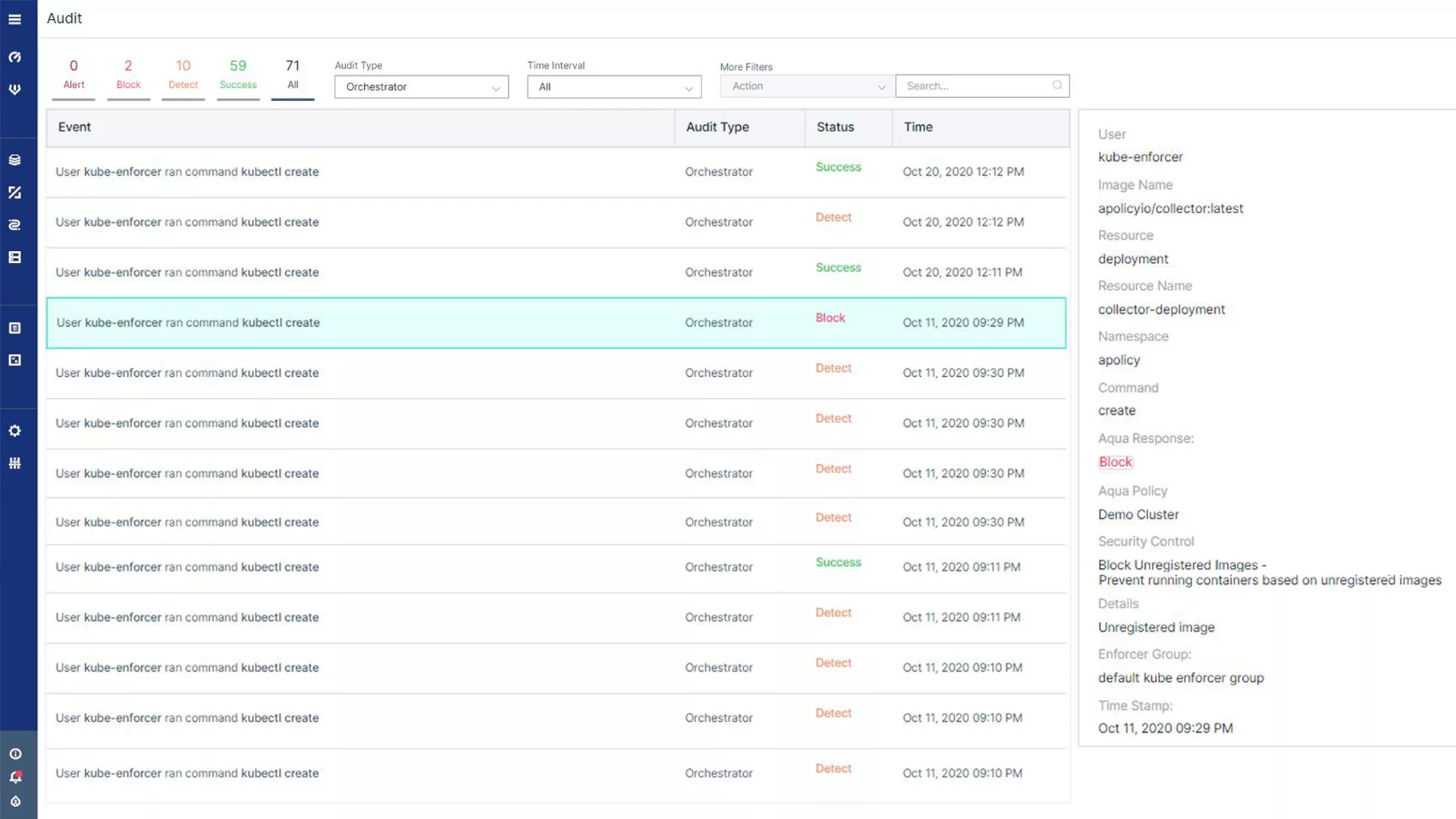
Kubernetes Context for Audit Events
Achieve visibility into Kubernetes security events to facilitate compliance, forensics, and incident response. Event logging includes diverse Kubernetes-specific information, such as pod name, type, deployment, and namespace data, user access, and container start/stop.
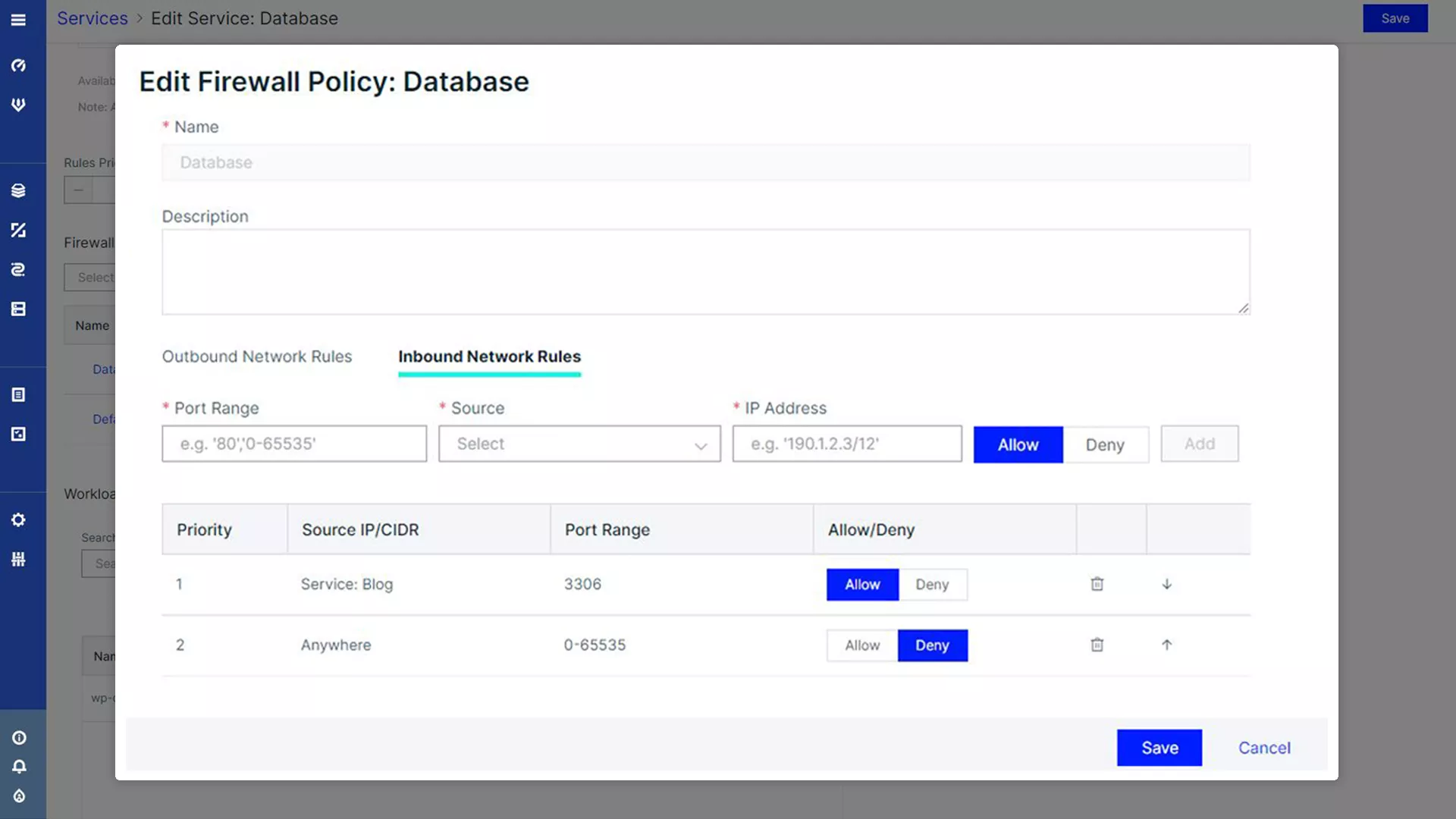
Identity-based Segmentation
Enforce container-level network rules with Aqua’s identity-based firewall, within and across clusters. Use it seamlessly with K8s network plug-ins, including Weave, Calico, Flannel, and Contiv. Visualize network connections, automatically map connections, and create rules based on Kubernetes namespaces, clusters, and deployments.