Protecting Cloud VMs and Instances
Automate VM security in private, public & hybrid cloud environments. Ensure compliance with PCI-DSS, HIPAA and other requirements, detect configuration issues quickly, and protect VM-based workloads in runtime.
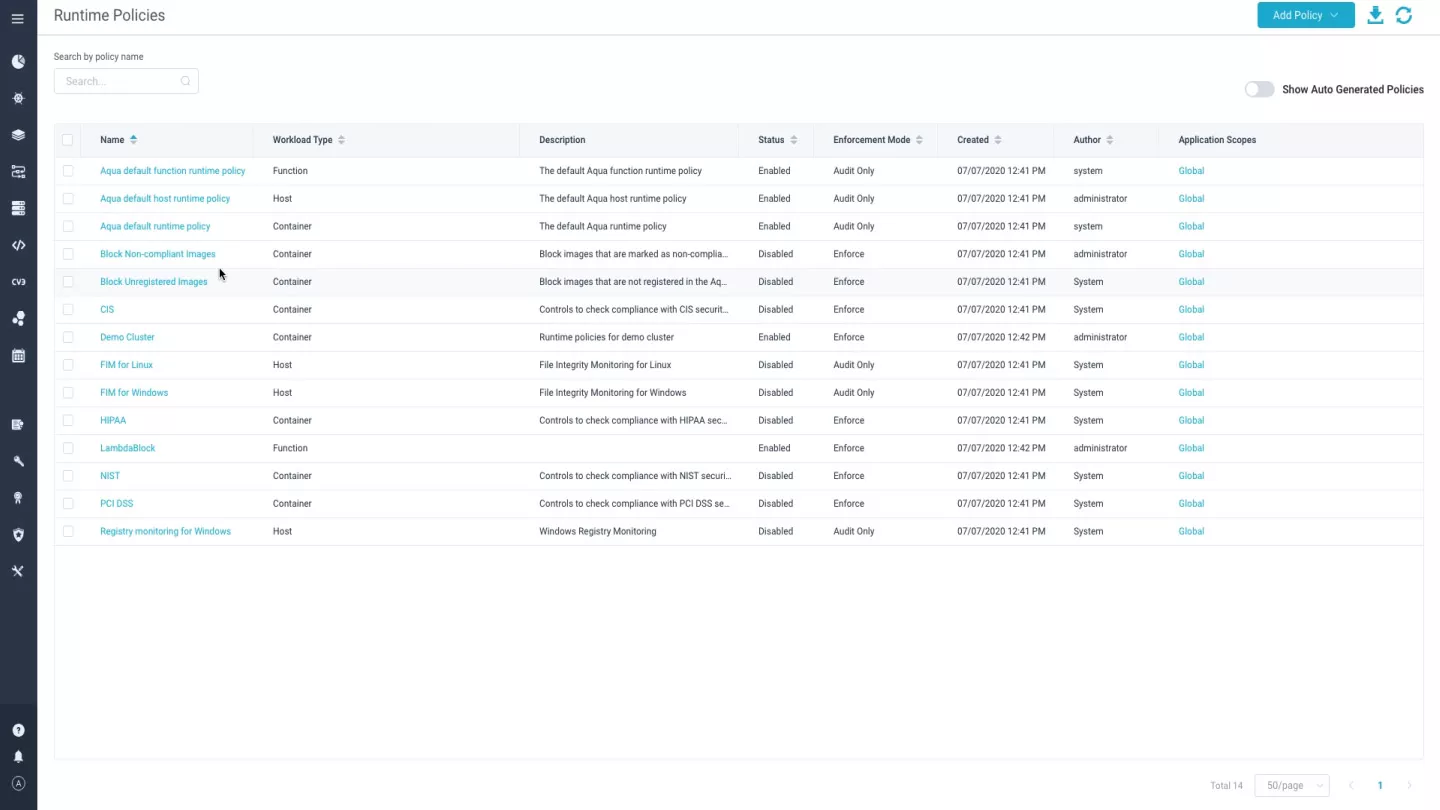
Vulnerability scanning
Scan cloud VMs for known vulnerabilities and malware, check OS configuration against the CIS Benchmark for Linux, ensuring that the security posture of your cloud VMs is aligned with compliance policy and free from malware
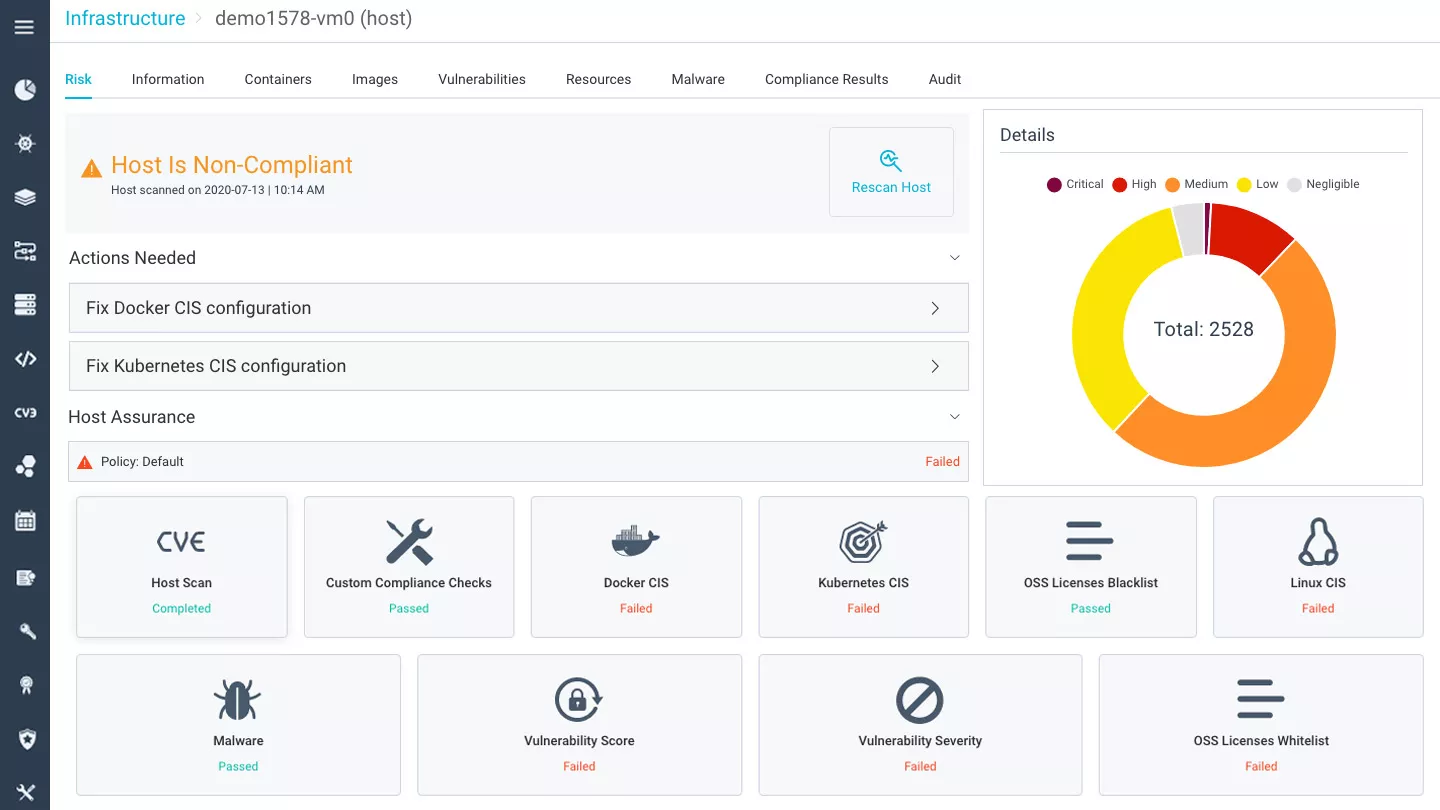
Host assurance
Get alerts on system and application configuration violations, define a compliance baseline for VMs by using built-in and custom configuration checks, review remediation steps for aligning non-compliant VMs.
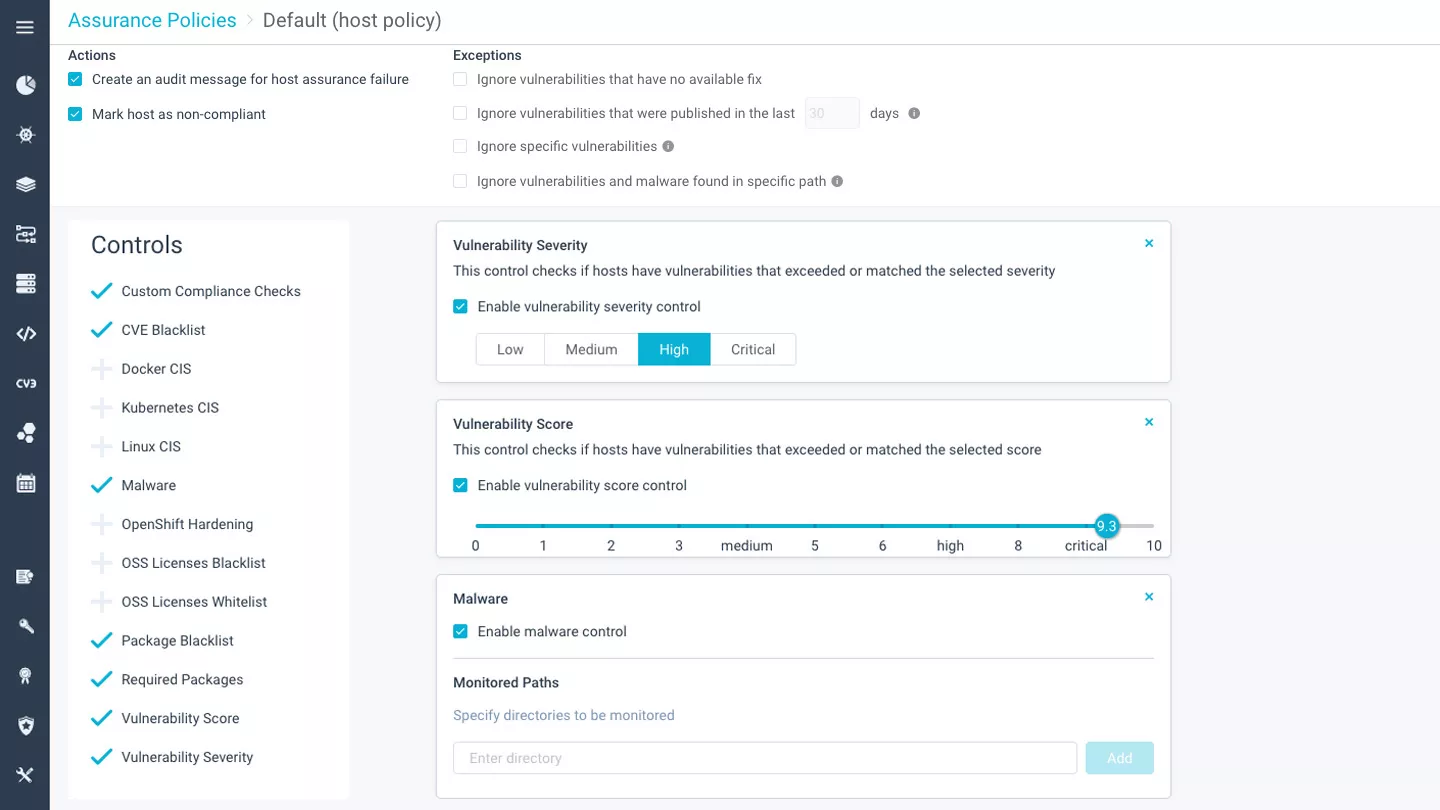
File integrity monitoring
Prevent access to the host by specified users and/or groups of users, monitor files and directories for read, write, and modify operations, track user access, attempted logins, and full command arguments.
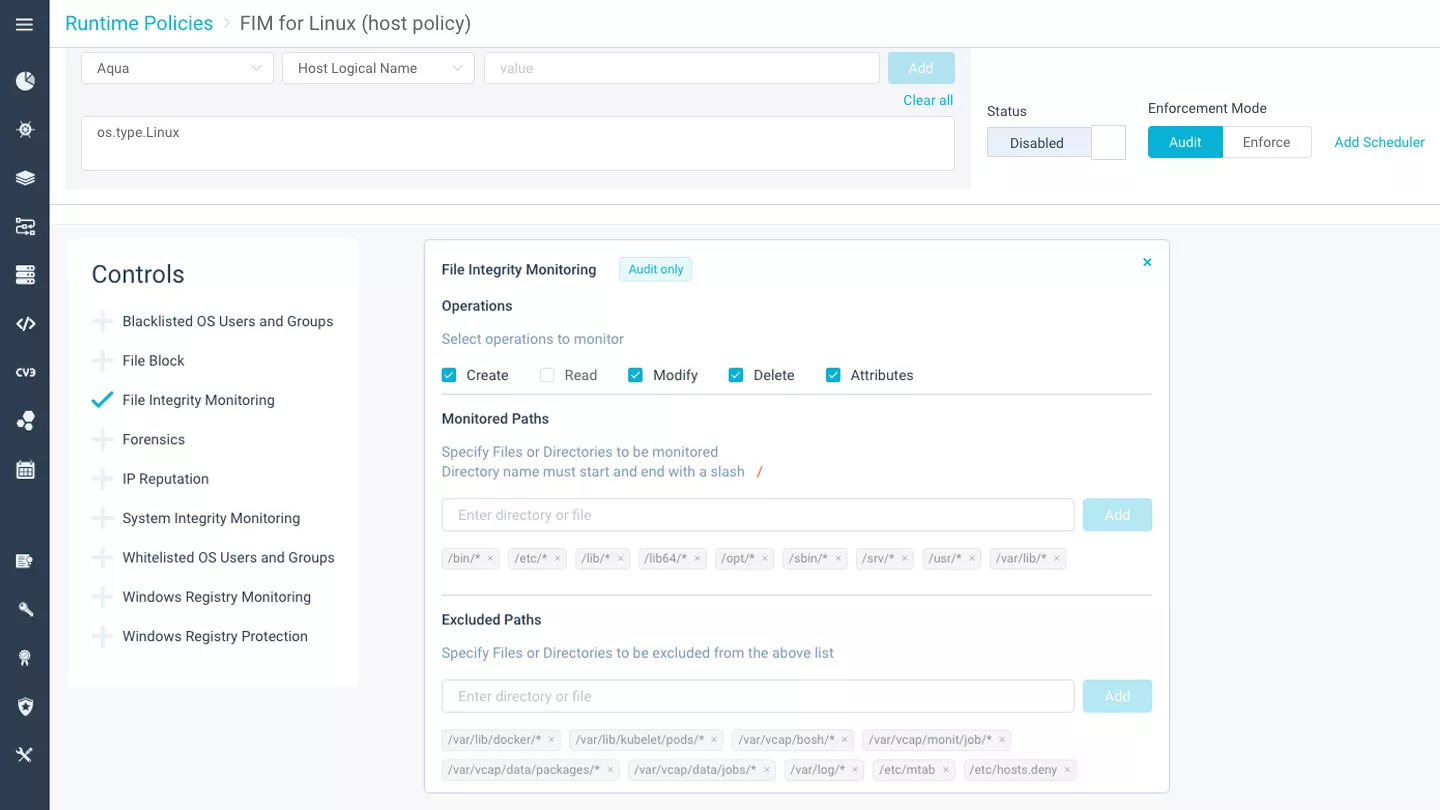
Windows registry monitoring & protection
Monitor and enforce changes in Windows registry, secure selected operations on Windows registry keywords, values, and/or path attributes, audit specific processes and Windows users.
Workload segmentation
Gain full visibility into cloud VMs that run on a single/hybrid cloud, automatically enforce network firewall rules based on VM services, along with IP addresses and domain names (DNS) and cloud attributes.
Forensic Analysis
View a single system of truth and avoid questions around evidence tampering and sequencing across disparate tools while reconstructing the sequence of events, track suspicious or malicious activity across a stack of virtual machines, containers, Kubernetes clusters, pods, etc., to form a holistic view of wide-scale, multi-vector attacks.