Container images are a growing path for external code to enter an organization. Docker has simplified image workflow in order to encourage adoption by developers, so anyone can pull and run images that were built and pushed to Docker Hub, often by unknown individuals. This is being exploited by malicious actors to embed sophisticated malware in innocent-looking images.
Application dependencies within container images are often based on open source packages that can be exploited by a dishonest contributor, who’s gained a sufficient level of trust and was able to push malicious code into an open-source project. While mature projects such as the official Linux distributions have well-defined review processes, smaller projects lack the resources to effectively review code from trusted contributors and have weak governance.
Currently, there’s no practical method to verify what a container image will do when activated, short of actually running it, which is very risky without properly isolating it from the internal network. Organizations are putting themselves at risk by blindly running container images from public sources inside their environments.
This risk isn’t theoretical. Aqua’s cyber research team has uncovered and blogged about escalating attempts to hide malware inside container images, in a way that evades static malware scanning and only comes to life when the container is instantiated – often using several stages.
Introducing Aqua Security’s Dynamic Threat Analysis—The Industry’s First Container Security Sandbox
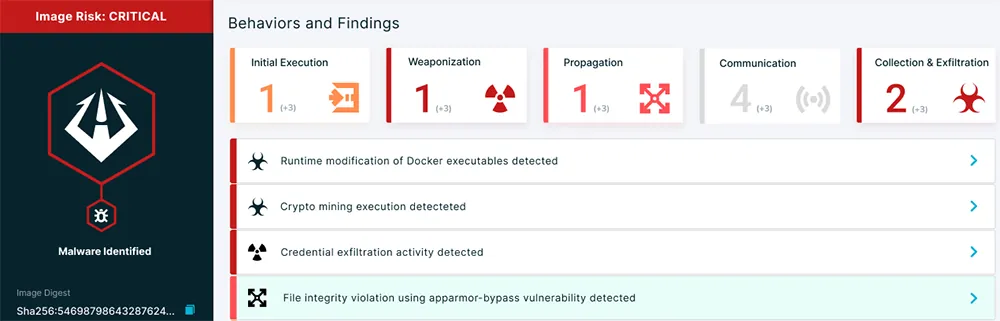
Aqua Security’s Dynamic Threat Analysis (DTA) dynamically assesses the risks that container images pose before they are run as containers in a live environment. Aqua DTA runs container images in a safe and isolated sandbox environment, and monitors behavioral patterns and Indicators of Compromise (IoCs) such as malicious behavior and network activity, in order to detect container escapes, malware, cryptocurrency miners, code injection backdoors and additional threats.
Once an image scan is initiated from either a registry or a CI/CD pipeline, Aqua DTA runs and analyzes the image for several minutes and displays the analysis results, determining the potential risk level that the image presents if allowed to run in an open, networked environment.
When Should Aqua DTA be Used?
In addition to static scanning of images for malware, vulnerabilities, and other issues, we recommend using Aqua DTA to address the following use cases:
- Approve public images and their open source packages – scan and whitelist public container images and their open source packages as part of the security controls in your software development life cycle (SDLC)
- Approve ISVs’ third-party images – scan third-party images from independent software vendors (ISV) before introducing them into the organization. Since the provenance of 3rd party images is often hard to prove, such images might represent unknown risks
- Pre-production security gate – scan release candidate images before being promoted to production from your release CI/CD pipelines or registry, as an extra precaution, especially as pertains to sensitive or critical applications
- Analysis and research – scan specific images to quickly analyze and understand their runtime behavior, for example to understand resource usage anomalies or after a suspected incident as a measure of forensics
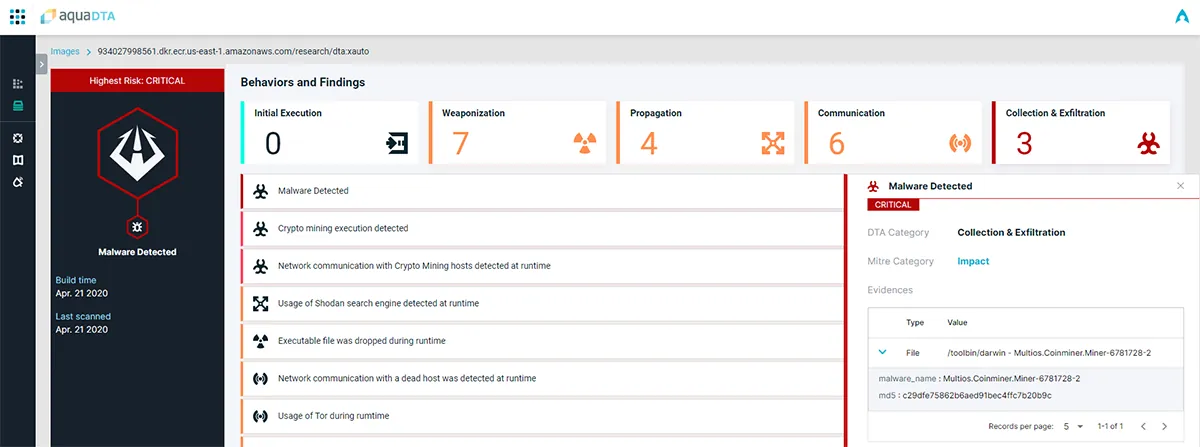
Example #1— Real Life Image Poisoning from Docker-Hub
Recently, our cyber research team has identified a malicious container image on the Docker Hub registry called jzulu/xauto. That container image was removed from Docker Hub promptly after being reported.
Scanning the image with Aqua DTA revealed solid proof of malicious behavior during runtime that provided insight into the exact mechanisms employed by malicious actors:
- A script in the container dropped a binary file into the container disk storage
- The file was base64 encoded and would not have been detected by static anti-malware scans
- The decoded binary file was recognized by a known malware detection engine
- Network traffic showed attempts to communicate with known cryptocurrency miner hosts
- TOR communication attempts and Shodan search engine tools were used during runtime
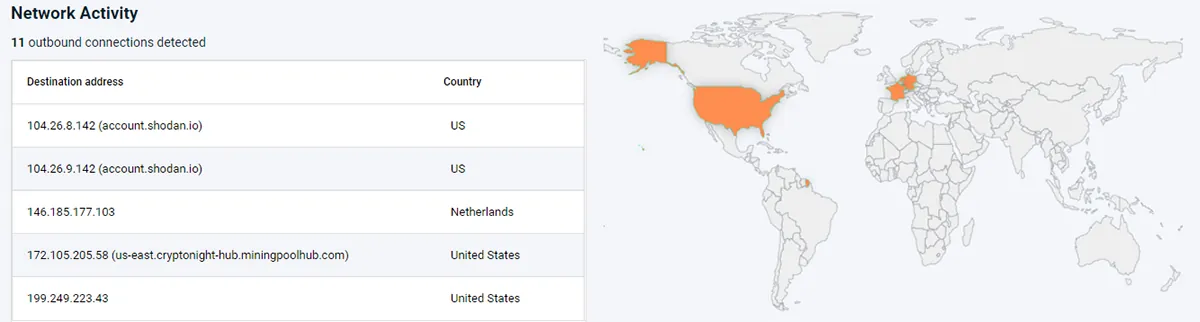
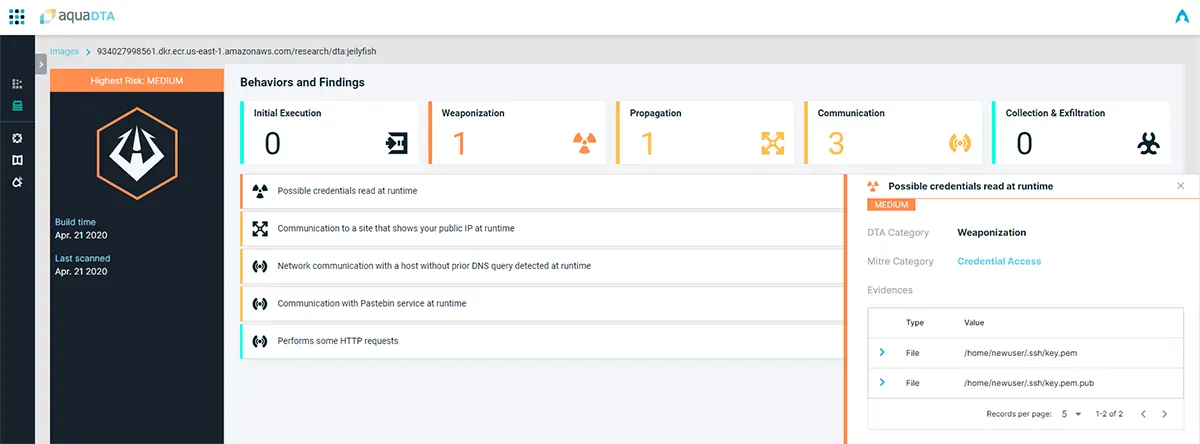
Example #2 – Malicious OSS Packages: The python “Jellyfish”
A few months ago, two malicious python packages that leveraged a type of squatting attack to steal SSH and PGP keys were discovered, after being available for download for a year. Our cyber research team ran a container that included the jellyfish package and then scanned it with Aqua DTA. It successfully identified the image as malicious with the following behaviors:
- Credential read on runtime
- Communication to host based on IP address, without DNS lookup
- Credentials read during runtime and communication with hosts without DNS lookup
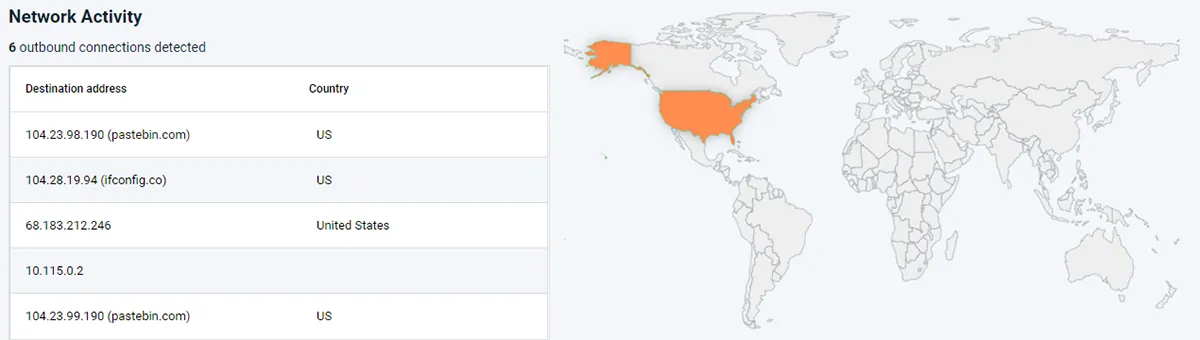
The Known is Not Enough
The software supply chain for containers, with its extensive use of open source packages and images from different sources, makes it challenging to know and control the exact payload of each container image. The increasingly sophisticated attacks we have witnessed require addressing this risk, which static malware scanners cannot address. Aqua Dynamic Threat Analysis assesses the hidden risks from container images before they run in production environments. It complements image vulnerability and static malware scanning, reducing the risk of attacks on containerized applications and providing additional controls to secure the software supply chain, in a highly automated fashion.
Aqua DTA is offered as an extension to Aqua Security’s Cloud Native Security Platform (CSP) to scan images from various CI tools and container registries, and is available in preview in Aqua CSPM.