A new vulnerability in the Apache Commons Text library indicates that attackers can perform remote code execution (RCE). The media rushed to create hype around this vulnerability, comparing it to the infamous zero-day vulnerability Log4Shell, which emerged late last year and was broadly exploited by attackers. However, it’s too soon to say whether this new vulnerability has the same vast impact on production environments and if attackers can as easily exploit it. So far, we haven’t seen in our honeypots any indications that this vulnerability is actively being used in the wild.
What is Text4Shell (CVE-2022-42889)?
Apache Commons Text is a library focused on algorithms working on strings. On October 13, 2022, a new vulnerability, CVE-2022-42889, was published, which can lead to remote code execution (RCE).
Alvaro Muñoz, a security researcher who initially reported this vulnerability, found that the library’s (or specifically the StringSubstitutor class) default interpolators may lead to unsafe script evaluation and can result in code execution when processing malicious input. In short, using the library with its default configurations together with the right malicious input can lead to unwanted malicious code execution.
Further details were provided in the Apache mailing lists:
“Apache Commons Text performs variable interpolation, allowing properties to be dynamically evaluated and expanded. The standard format for interpolation is “${prefix:name}”, where “prefix” is used to locate an instance of org.apache.commons.text.lookup.StringLookup that performs the interpolation. Starting with version 1.5 and continuing through 1.9, the set of default Lookup instances included interpolators that could result in arbitrary code execution or contact with remote servers. These lookups are: – “script” – execute expressions using the JVM script execution engine (javax.script) – “dns” – resolve dns records – “url” – load values from urls, including from remote servers Applications using the interpolation defaults in the affected versions may be vulnerable to remote code execution or unintentional contact with remote servers if untrusted configuration values are used.”
Below is a snippet that appeared in Muñoz’s report:
![]()
According to NIST, this vulnerability affects Apache Commons Text versions 1.5 through 1.9.
Thus far, this vulnerability strongly resembles Log4Shell, a critical vulnerability that got a lot of attention after a proof of concept (PoC) was released in the wild in December 2021. Both vulnerabilities are in open source projects that are broadly used by different applications. Some media are calling CVE-2022-42889 a “new Log4Shell vulnerability”, saying that it’s even more dangerous than the previous one.
However, this new vulnerability is still being analyzed by NIST, the details about the severity and scope in the wild are still unclear and might change. Thus, it’s too soon to jump to conclusions that this is “the new Log4Shell”. Furthermore, research by Rapid7 provides more details on the issue that might slightly reduce the severity of this CVE. According to the research, the vulnerability only worked on some JDK versions (1.8.0_341, 9.0.4, 10.0.2. 11.0.16.1, 12.0.2, 13.0.2, 14.0.2) while failed on other JDK versions (15.0.2, 16.0.2, 17.0.4.1, 18.0.2.1, 19).
Mitigation recommendations
If you’re using any vulnerable version of Apache Commons Text (1.5-19), upgrade the library to the patched version (1.10) as soon as possible.
To detect this vulnerability in your environment, you can connect your repository to the Aqua Cloud Native Security Platform, which automatically maps your dependencies and identifies all vulnerable dependencies your projects use.
You can also identify and block all the workloads that have CVE-2022-42889 and even prevent their execution using assurance policies. Also, if you include the Aqua Scanner as part of your CI/CD pipeline, it will automatically identify and block any new builds that have the Text4Shell vulnerability, shifting security left.
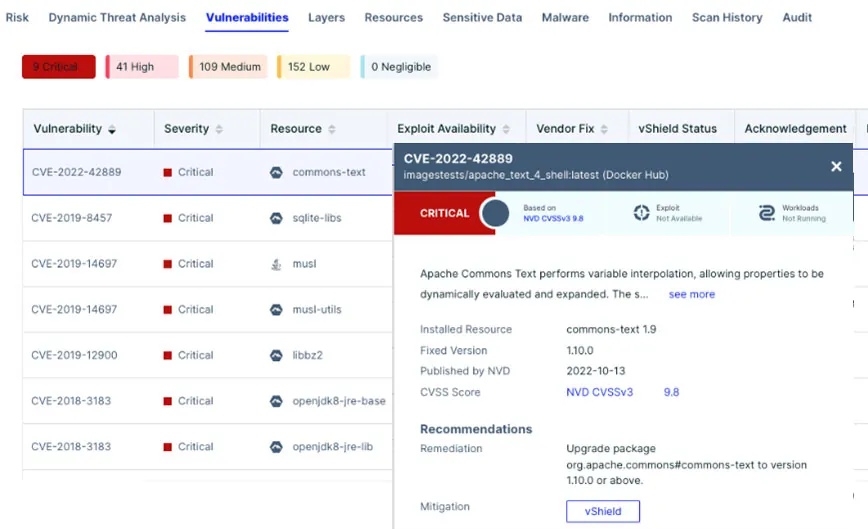
Aqua detects CVE-2022-42889 aka Text4Shell

