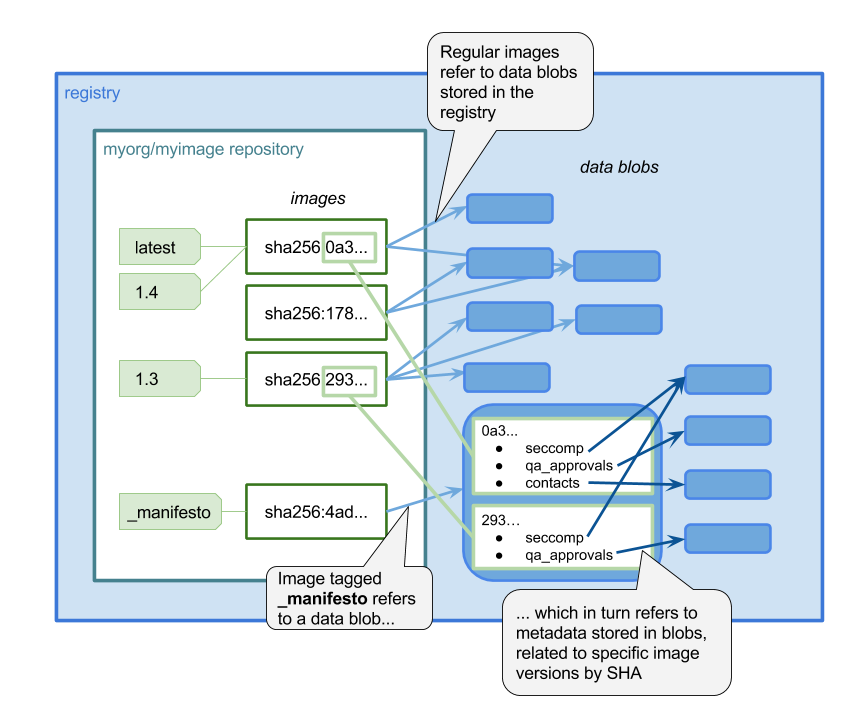
Here at Aqua Security, we recently released an open source project to help container users manage the metadata associated with their container images. It’s called Manifesto, and it stores free-form metadata in the registry, alongside the images themselves.
The Need for Post-Build Metadata
I’ve been interested in container metadata for a while, working on MicroBadger and the label-schema standard. These projects addressed metadata that you can add to an image at build time through labels, but they don’t really help with the information about an image that you can update post-build — perhaps throughout its lifetime.
Just a few use cases for metadata that needs to be updated after an image is built include:
- Keeping track of test results and approval status for an image as it passes through a set of “gates” before deployment
- Saving the Seccomp / AppArmor or other security profile that you want this image to run under
- Storing the latest vulnerability scan report for the image.
In all these cases (and many more) it’s possible to store the information somewhere else, but it’s a headache to tie it back to the image it relates to. The Manifesto project aims to remove that pain and make it seamless to store and retrieve data for your images.
A Command Line Tool
With Manifesto, we’ve built a prototype command line interface (CLI) that lets users add, list and get arbitrary metadata for a specific image.
Metadata for Automation
The demo above shows retrieving the seccomp profile for a particular image and storing it in a file. This could then easily be passed into the command to deploy a container — for example in Docker:
$ manifesto get myorg/myimage:v1.1 seccomp > seccomp.json
$ docker run --security-opt seccomp=seccomp.json myorg/myimage:v1.1
More generally, the CLI could be used in many automation scripts — for example, storing test results and those all-important vulnerability scans for an image as part of a CI/CD pipeline.
Leveraging Notary for Data Security
It’s important that the metadata is kept secure and intact — you don’t want a bad actor being able to mess with your vulnerability reports to mask an exploit, or tampering with your security profiles. The Docker team have done an excellent job of ensuring the provenance of images through Notary, and with Manifesto, we’re aiming to leverage Notary for image metadata as well as the images themselves. In fact, there’s a Moby project proposal for standardized vulnerability reports that discusses using an approach along these same lines.
The Future of Manifesto
We’re aiming to take Manifesto forward from its current prototype stage to being a robust, secure and useful tool. Our friends at Puppet have already implemented Manifesto into their project Lumogon, a tool for inspecting container-based applications. We’ve had some helpful feedback, and, dear reader, we welcome your ideas, comments, PRs, and GitHub stars!

