In April, MITRE published the ATT&CK matrix for Containers covering adversarial techniques that target container technologies. At Aqua, we were proud to support this effort by sharing our knowledge and helping refine and extend the matrix. As for the risks in Kubernetes, Microsoft created a framework for Azure-based environments (AKS), but what about vanilla K8s? We incorporated techniques that Aqua researchers have observed in real-world attacks and developed our own dedicated threat matrix for Kubernetes, mapped to the MITRE ATT&CK Framework.
This holistic tool can help security teams better understand the various tactics and techniques used by attackers to exploit K8s-based environments as well as provide a foundation for developing more effective defense practices against them.
Evolving Threat Landscape
As Kubernetes adoption grows, the attack surface significantly expands, allowing bad actors to find and exploit vulnerabilities in cloud native stack. The complexity of Kubernetes and the lack of proper security controls make the attacks targeting Kubernetes clusters and containers hosted in them a real risk for organizations. Last year, Aqua’s team Nautilus uncovered a market-first container image built to attack Kubernetes clusters.
With the threat landscape evolving fast, it’s critical to understand security risks and key attack vectors in Kubernetes.
Mapping Threats in Kubernetes
The MITRE ATT&CK® framework is a detailed knowledge base of tactics and techniques attackers use to infiltrate an environment and carry out an attack. The following table provides a guide for SecOps and InfoSec professionals to the critical elements of securing a K8s environment aligned with the MITRE ATT&CK categories. This framework helps organizations understand the attack surface of their environments and ensure they have the right detection and mitigation strategies in place to address these risks.
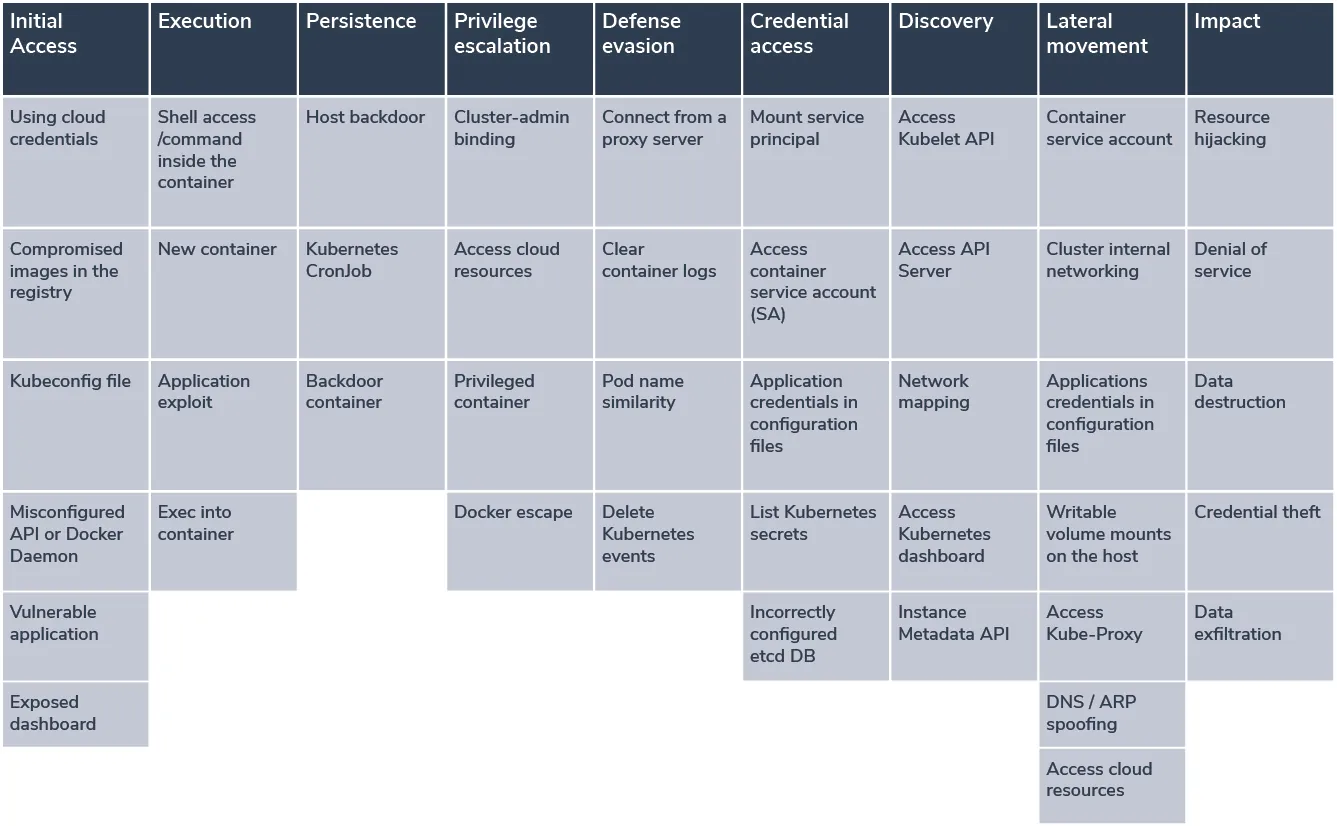
This matrix describes tactics and techniques adversaries use to target Kubernetes environments. They can be leveraged to achieve different goals – get access to credentials and sensitive information, mine cryptocurrency, or advance the attack in other ways.
Let’s look in more detail at some common techniques:
Initial Access
Compromising a kubeconfig file. It’s a popular attack vector in Kubernetes as this file contains the location data and credentials of the clusters. If malicious actors can gain access to this file via a compromised client, they can get access to the whole cluster.
Defense Evasion
Pod Name Similarity. This is a sophisticated technique where an attacker leverages how Kubernetes names system pods and creates a malicious pod with a similar name, using a random suffix to hide it within the cluster. Then this pod is used to execute malicious code or get access to additional resources.
Credential Access
List Kubernetes Secrets. These resources are specific to Kubernetes and store credentials that can be accessed via their API. An attacker can exploit misconfigurations and weaknesses in the cluster to access the Kubernetes API server and retrieve valuable information from the Secrets objects.
Lateral Movement
- Cluster Internal Networking.
By default, there are no network restrictions between pods in a Kubernetes cluster. In case attackers get access to a single pod that can communicate with other running pods or applications, they can move laterally within your cluster. - Writable volume mounts on the host.
This technique exploits the way that containers work, the hostPath volume mounts a file or directory to the container, which allows an attacker to achieve persistence on the host.
Conclusion
As new threats come to light every month, Aqua’s team Nautilus conducts threat research entirely focused on the cloud native stack, uncovering new vulnerabilities, threats, and attacks that target containers, Kubernetes, serverless functions, and public cloud infrastructure. This helps us constantly develop new security methods and tools to efficiently address the ever-expanding threat landscape of cloud native technologies.
With a more holistic overview of the Kubernetes threat matrix, dedicated to the whole cloud native stack, organizations can gain a comprehensive understanding of adversary tactics and techniques, develop robust defense strategies and, ultimately, improve the security posture of their Kubernetes applications.

