The cloud native threat landscape is evolving fast, with 50% of vulnerable targets getting attacked within only one hour. While adversaries are constantly advancing their techniques to craft more sophisticated and targeted attacks, organizations are leaving themselves exposed. Aqua’s 2021 Cloud Native Threat Report analyzes attacks observed in the wild and identifies major trends in the threat landscape for container supply chain and infrastructure. What insights can we learn from the findings?
Attacks targeting cloud native are on the rise
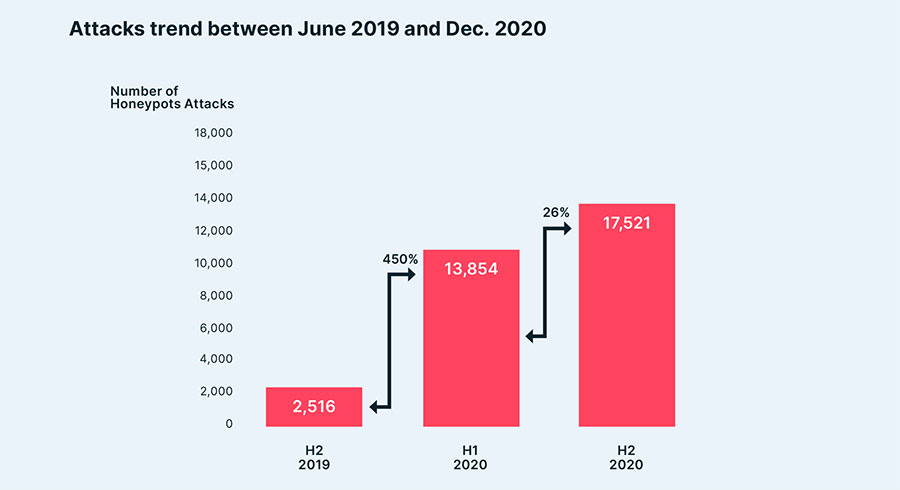
The volume of attacks against container environments continues to increase, indicating that organized and well-funded teams are behind them. Over a six-month period, Aqua’s research team Nautilus uncovered 17,358 attacks on honeypots, representing a 26% increase from only six months previously.
Security of CI/CD pipelines requires more attention
As adversaries keep searching for new ways to attack cloud native environments, supply chain and CI/CD pipelines have become a common attack vector, which wasn’t the case in the past. We identified a massive attack against GitHub, Docker Hub, Travis CI, and Circle CI that managed to execute crypto miners during the auto-build of an image process.
Why is exploiting the auto-build process so appealing to cybercriminals? Attacking the components of the supply chain allows the threat actors to infect more organizations at once and achieve wide dissemination of malicious code. Moreover, the adoption of security tools designed to protect the build process within CI/CD pipeline is still fairly limited in most organizations, and hiding an attack during a CI build would, most likely, succeed.
Even the slightest misconfiguration can expose you to an attack
Threat actors are adapting their techniques much faster and are quick to find vulnerable targets: 50% of new misconfigured Docker APIs are attacked by botnets within only 56 minutes of being set up. This once again highlights how important it is to detect and remediate cloud misconfigurations in a timely manner or prevent them from occurring before deployment.
Attacks are getting increasingly sophisticated
Attackers have amplified their use of evasion and obfuscation techniques in order to avoid detection and increase the chances of a successful attack with a bigger impact. To achieve their goals, they are packing the payloads, running malware straight from memory, and using rootkits.
Adversaries pursue more sinister goals with their attacks
Crypto-currency mining is still the most common objective of attacks, with more than 90% of the malicious images executing resource hijacking. However, new goals are emerging as well. We saw many attacks hiding more sinister objectives, such as backdoors, malware deployments, and credential theft. For example, more than 40% of attacks we analyzed involved creating backdoors on the host.
This way, attackers are looking to maximize their gain from each attack, using crypto-mining as the potential short-term gain. But their longer-term goal is gaining a backdoor to the environment and achieving additional access to the victims’ environments and networks.
For complete findings, explore the Cloud Native Threat Report: Attacks in the Wild on Container Infrastructure.
Protect Your Container Supply Chain and Infrastructure from Attacks
Understanding the ever-expanding threat landscape in cloud native environments is the first step of building an efficient security strategy to protect these environments. As new sophisticated attacks emerge, it’s becoming more important than ever for organizations to embrace holistic security that is applied across an entire application lifecycle.

