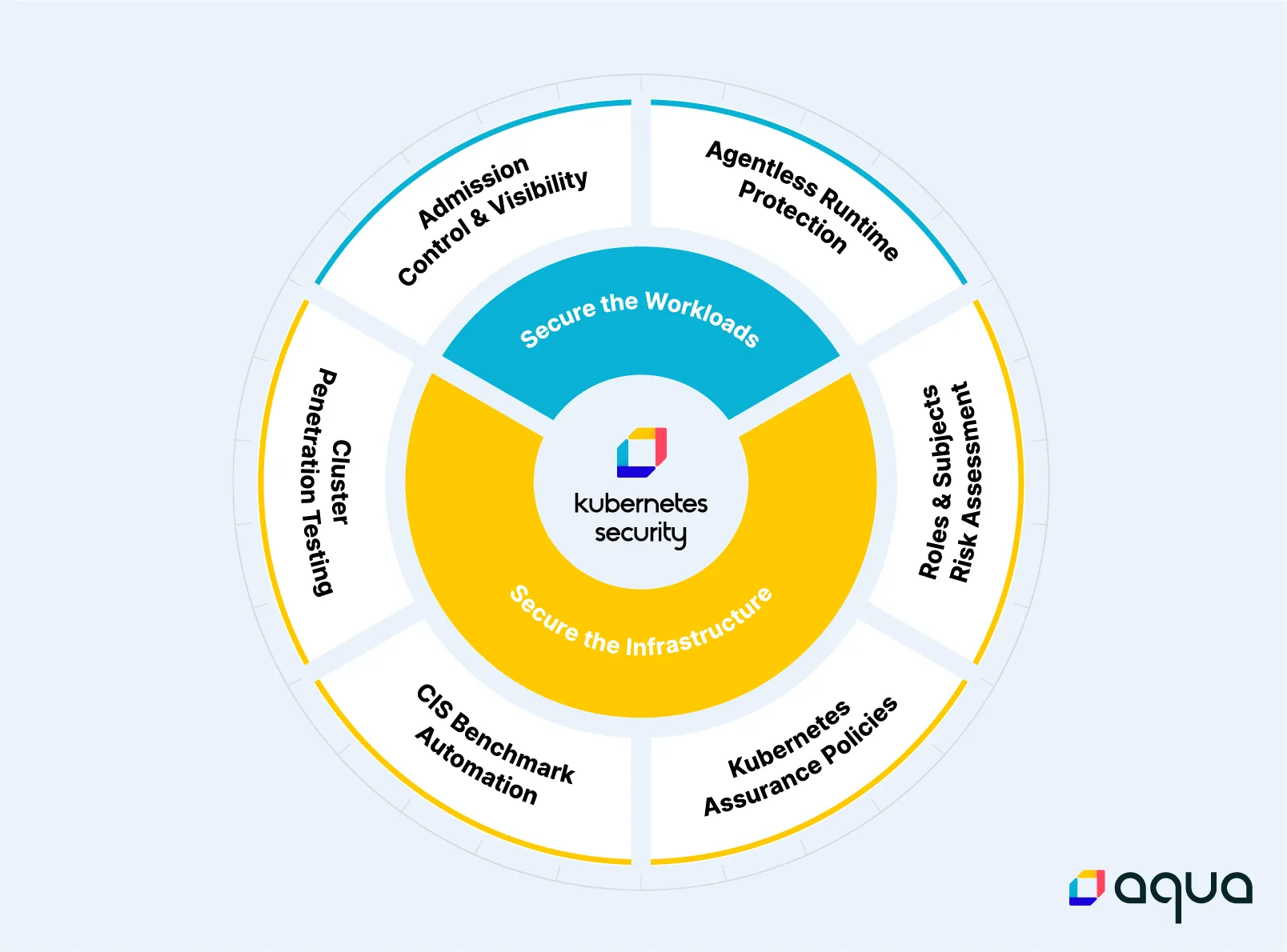
Although Kubernetes has certainly matured into a well-adopted container orchestrator platform, it remains complex to manage and secure. Coupling this with a growing attack surface and bad actors trying to exploit it, organizations must implement a comprehensive approach to securing their K8s applications. Aqua aims to tame the complexity of securing K8s-based applications by leveraging K8s-native controls such as Admission Controllers and equipping pods with a sidecar.
Leveraging Kubernetes-native controls and helping organizations implement security as close to the application as possible bridges the gap between security and DevOps teams. To make this a reality, we introduced Kubernetes Security Posture Management (KSPM) – a suite of new capabilities that help you assess the security posture of your Kubernetes infrastructure. Posture management should be part of any Kubernetes security program, and runtime controls should be used to complement it. After you’ve made sure that your cluster is configured correctly and control which images get admitted into your cluster, it’s time to think about runtime protection for running workloads in your clusters — in order to detect and prevent suspicious behavior and potential breaches.
Kubernetes Admission Controllers
Before we delve into Kubernetes-native runtime protection, we need to understand a critical enabling mechanism built into the Kubernetes API, namely admission controllers, and specifically the ability to manage them via webhooks. Admission Controllers are designed to help K8s admins implement secure-by-default deployments. They can serve many purposes, from resource control to provisioning, as well as security aspects such as intercepting requests to the Kubernetes API server before an object persists.
Admission controllers help you define and customize what can run on your cluster and can be used via “validating” or “mutating” webhooks, or both. The difference between the two types is that a mutating webhook can modify objects sent to the API server to enforce custom defaults, while a validating admission webhook can reject requests to implement custom policies. So, while validating webhooks can only be used to admit or deny objects in K8s (like deployed Pods), mutating webhooks can be used to change their configuration.
Leveraging Kubernetes-native Security
Since the emergence of Kubernetes as the industry’s “go-to” container orchestration system, Aqua’s container runtime protection has worked seamlessly within Kubernetes while leveraging some of its native features as well as using controls that operate out-of-band with Kubernetes (which has its advantages). But as Kubernetes becomes more widely deployed in production and the attack surface expands, organizations need more robust runtime protection controls to deal with their increasingly complex environments while avoiding the complexity that might entail.
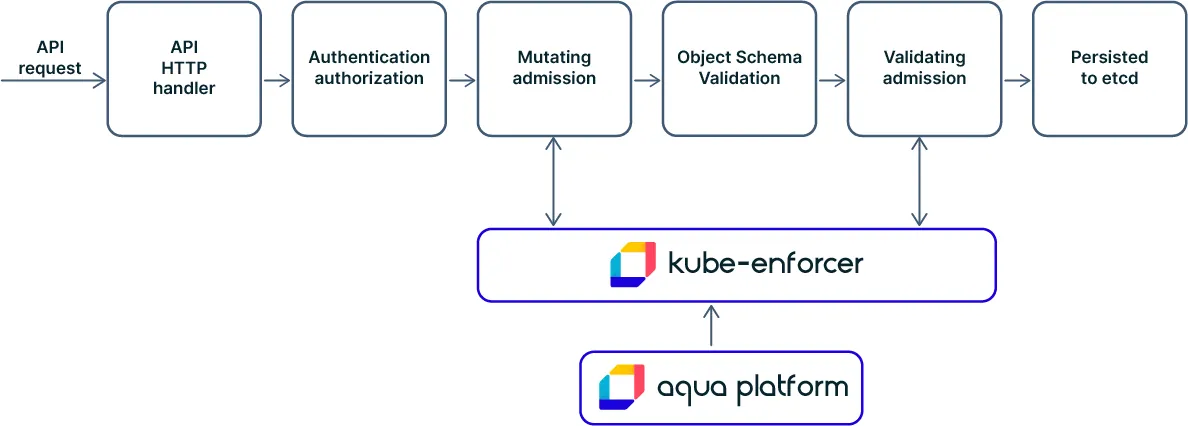
Today, the most common way to secure K8s workloads in runtime is by deploying a privileged container (such as Aqua Enforcer) on the host/node. However, to some organizations, this presents a security impediment or an operational constraint. So Aqua is introducing an industry-first alternative way of enforcing runtime policies on Kubernetes workloads. Instead of deploying Enforcers on all nodes as privileged containers, you can now deploy an enhanced Aqua Kube Enforcer that implements both validating and mutating Kubernetes admission controllers via webhooks. Then, in a very similar fashion to how Envoy (a popular high-performance proxy) gets deployed, the mutating webhook injects our new, K8s-optimized Pod Enforcer as a non-privileged sidecar container into the pod as it’s being deployed. This enables Aqua’s runtime controls to be enforced on the containers running within the pod while also accepting dynamic policy changes.
Aqua Kubernetes Runtime Protection
With the new model, you can easily automate the Kubernetes deployment without any privileges on the node’s host OS while still providing dynamic runtime controls, such as container drift prevention, behavioral controls, and network controls. Aqua’s Kubernetes Runtime Protection helps organizations implement security as default and boost security governance in your Kubernetes cluster. You can easily enforce security without requiring host privileges across the entire Kubernetes architecture: host components, internal configuration, management API, and workload pods.
Admission Controllers and Visibility
Kube Enforcer is registered as a “validating” Admission Controller with the Kubernetes API Server, providing the DevOps team full visibility into the Kubernetes cluster, discover hosts, namespaces, and running containers, and control the deployment of pods in the cluster according to the SecOps policy. Kube Enforcer provides cluster-wide image validation and visibility via Risk Explorer and automatically registers discovered images of running containers.
Agentless Protection, Smooth Deployment
Aqua’s new Kubernetes runtime protection module eliminates the friction required to deploy runtime controls while supporting K8s capabilities such as automation, flexibility, and scale. It uses Kubernetes itself to deploy security controls into pods, so DevOps teams will not be required to change anything in their deployment practices.
Achieving Holistic Kubernetes Security
With the combination of Dynamic Admissions Control with a pod sidecar, Aqua provides an organization with a “front door” security offering for Kubernetes that addresses all potential workload threat options. DevOps can set fine-grain authorization policies for pod creation and deployments. Aqua Kubernetes Runtime Protection ensures the isolation of Kubernetes worker nodes and the control plane, and between the pod and the node. You gain better granularity to instrument workloads, regardless of the node, which supports large environments that optimize hardware.
With Aqua’s Kubernetes Security, your DevOps teams easily secure Kubernetes infrastructure configuration and can work more effectively with security teams to implement security policies throughout the pipeline.
Aqua’s Kubernetes Security Posture Management (KSPM) plus the new agentless K8s runtime protection empower organizations to defend K8s-based applications against multiple threats while giving them the freedom to choose the right runtime protection deployment model for their needs.

