Overly permissive defaults associated with roles and K8s subjects, such as service accounts, add risks to the attack surface of Kubernetes. And attempting to manually understand these risks and enforce least privilege rights in a Kubernetes environment is time-consuming and prone to human error. With the introduction of Kubernetes Security Posture Management (KSPM), we’ve now included best practices and controls to effectively monitor, assess, and remediate permissions for roles and subjects.
Organizations often face the decision of how to balance their teams’ access needs and operational efficiency with security needs, but they often do it just one Kubernetes cluster at a time. This is due to the complex, contextual nature of such permissions, as well as a lack of knowledge among DevOps and security teams as to the correct implementation of RBAC policies, which requires a lot of manual work. Consequently, in larger environments with growing numbers of Kubernetes subjects (either human or not) as well as roles, things can quickly spiral out of control.
To resolve this challenge, Aqua KSPM includes brand new controls. In addition to ranking the risk, these controls present and recommend remediation based on best practices.
Assessing RBAC risk in your Kubernetes environment
Our new Aqua Kubernetes Roles & Subjects Assessment feature starts by continuously monitoring and collecting Kubernetes RBAC data within your Kubernetes environment, including configuration and usage/activity, to build an accurate situational model of how roles and subjects are defined and being used.
This model provides you with unprecedented visibility into your RBAC posture within Kubernetes clusters. With this new risk modeling and assessment control embedded in the Aqua Console, customers gain a clear view of their Kubernetes environment, highlighting the most pressing issues that require immediate attention, such as:
- Security risks stemming from overprovisioned permissions
- Violation of industry benchmarks and standards
- Subjects (e.g., service accounts) with risky access
- Risky workload access settings
- Unsafe cluster access settings
Once identified, we provide users with an overview of the security posture of their Kubernetes settings. The goal is to assist Kubernetes admins in identifying the problem accurately, as well as the specific setting or role definition from which it stems. Any change in identity and access policies must be carefully analyzed to avoid service disruption, so the model includes using data to support your decision-making processes.
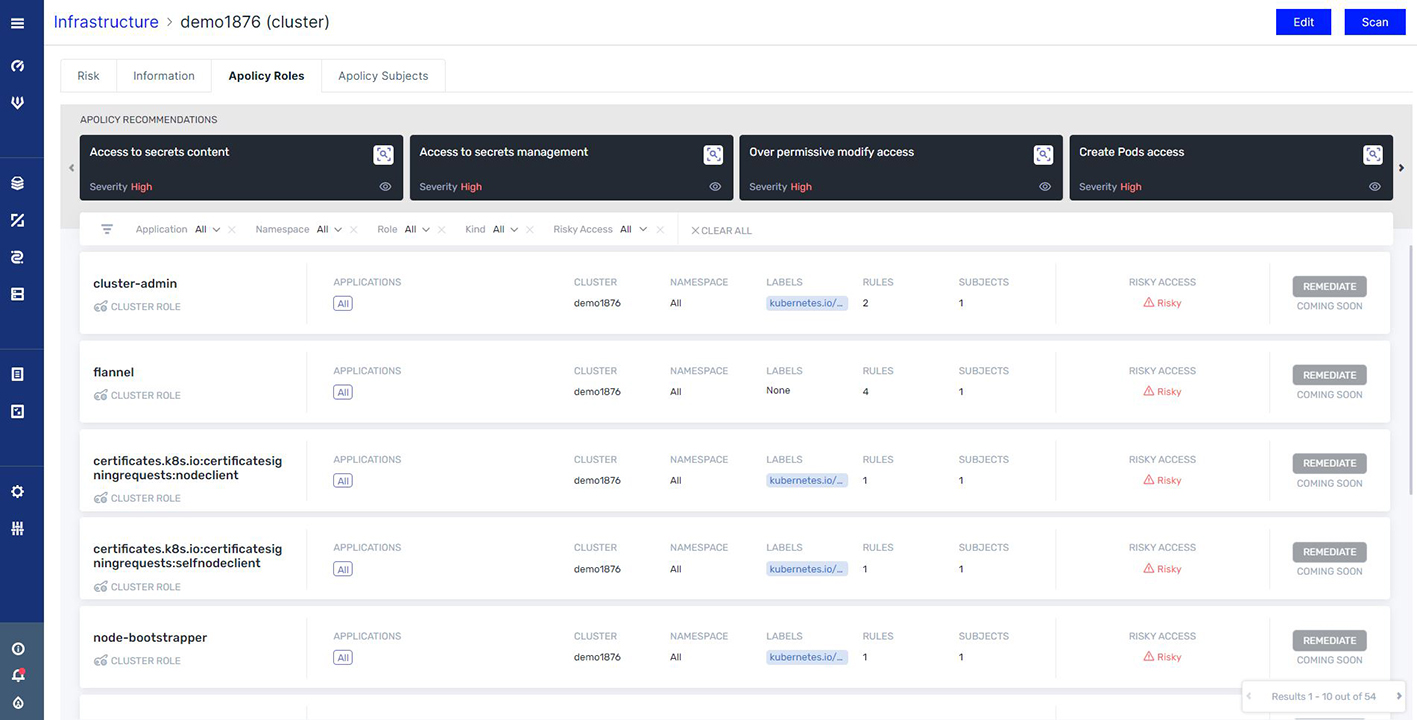
Better, faster remediation
We also provide a flexible framework to assign different policies to different applications while maintaining the ability to reuse policy building-blocks across applications and clusters. It includes out-of-the-box policies and knowledge base, including common regulatory compliance requirements and industry standards. Using this, organizations can quickly assign ready-made policies to their applications and, if needed, customize these policies to their needs.
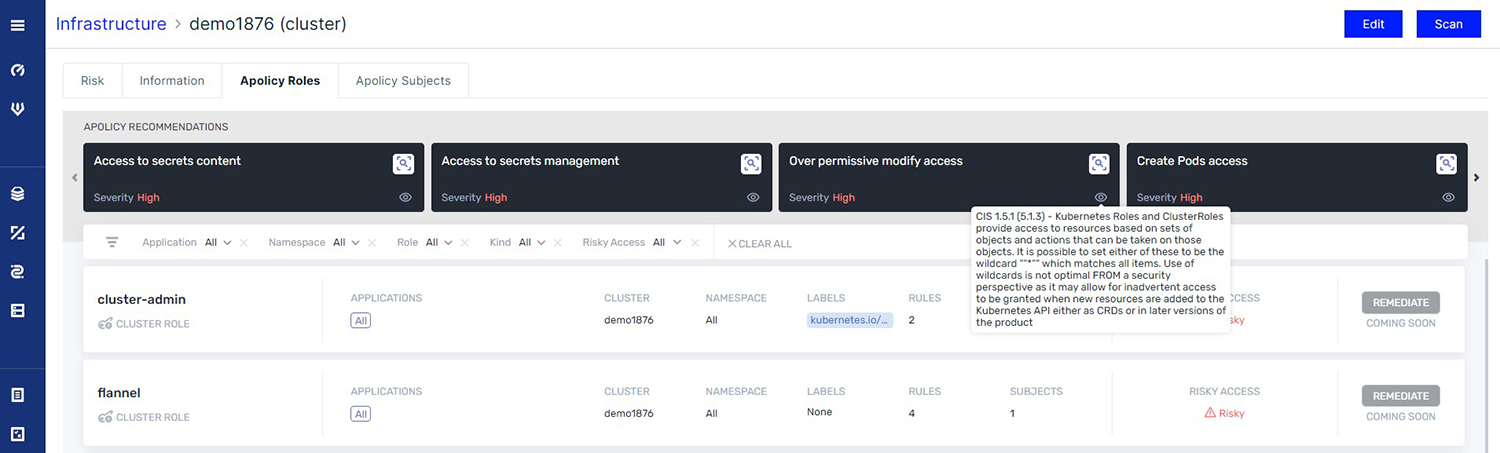
This flexible model provides the ability to reuse technical controls and promote collaboration between DevOps, security, and compliance teams. Additionally, we leverage the controls, written in Rego (built on the Open Policy Agent) and portable across your cloud native environment, to assess the permissions and privileges of users and subjects in your Kubernetes cluster. This way, you can quickly resolve identity and access issues, including complex multi-step scenarios that would otherwise take hours or days to investigate and fix manually. You can filter to a specific set of users and processes and expose any security risks lurking in your Kubernetes cluster.
Kubernetes least privilege access in action
When viewing all the roles that your Kubernetes cluster holds, it’s easy to become overwhelmed by the vast number of roles needing to be checked (54 in our example).
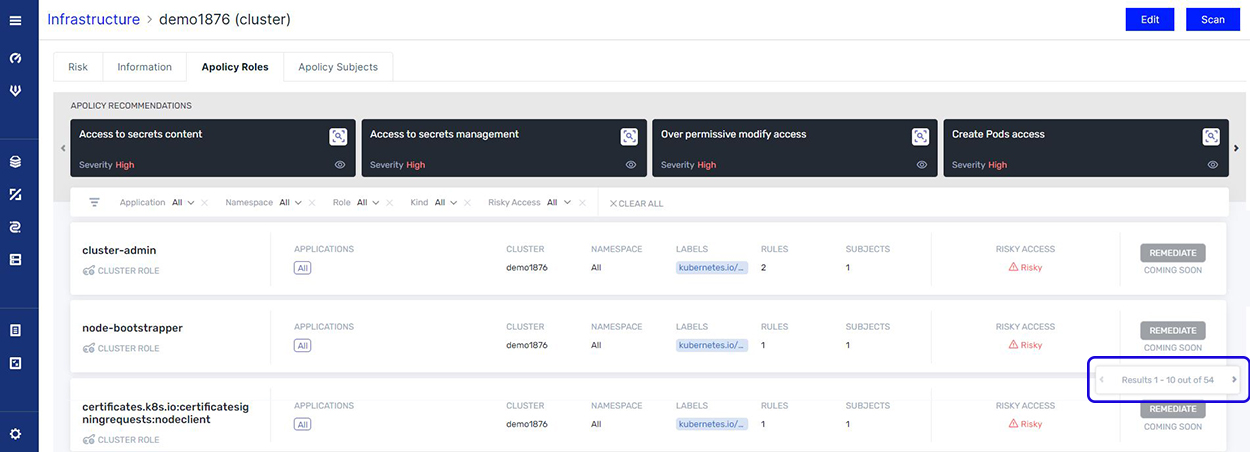
If you had to analyze each role to expose risky objects, it would be a very time-consuming job. However, by directing your attention to just the roles identified as having overly-permissive access, we can prioritize the list down to just six roles.
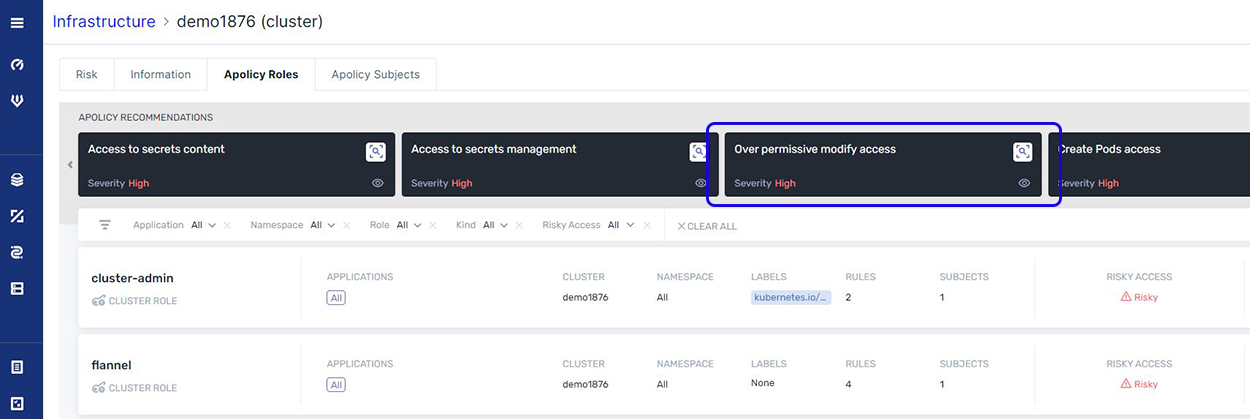
We can then drill down to get more details on the resources associated with those roles, and any violation related to specific compliance regulations.
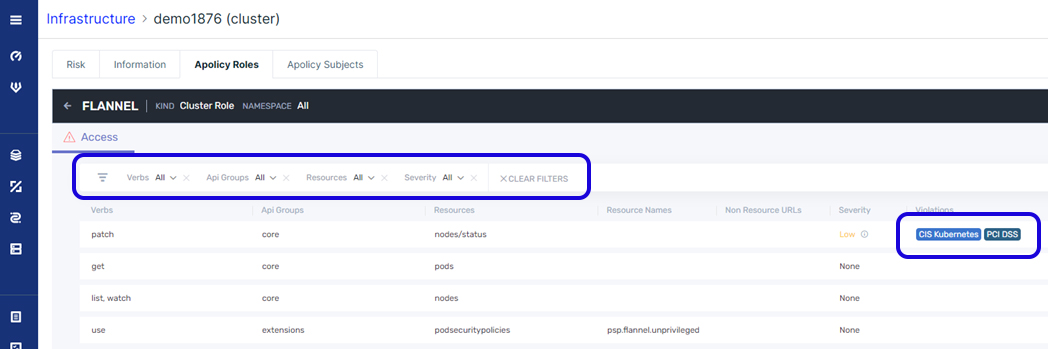
A new level of visibility and governance
The identity and access facets of Kubernetes are a critical part of its security and compliance. Using our Kubernetes Roles & Subjects Assessment helps organizations to ensure least-privilege access in their K8s environment while maintaining the right level of privileges for every user.
DevOps teams can automate risk management and compliance with policy-driven automation that replaces manually chasing a seemingly endless supply of poorly configured access controls, helping you prioritize remediation in your environment. You can quickly examine the permissions of roles and subjects (e.g., service accounts, access to resources in Kubernetes) to assess risk against best practices. And you can review what remediation steps are needed to reduce the risk and align with compliance regulations directly from the Aqua console.
Organizations can now easily secure their Kubernetes cluster configurations to better understand and reduce the attack surface, apply least-privilege access and best practices, avoid human errors, identify, and remediate risks, and prove compliance with industry regulations.
Learn more about Aqua KSPM (Kubernetes Security Posture Management)

