Two high-severity CVEs in the SaltStack platform were published last week by researchers at F-Secure. These vulnerabilities can enable remote code execution (RCE), which lets attackers remotely execute commands on the Salt leader node. This results in a full compromise of the host and can expose sensitive information within the cloud environment. To address this, Aqua CSPM has been updated with new plugins that check AWS, Azure, and GCP environments for these new vulnerabilities.
You can now find the details in the National Vulnerability Database. Both vulnerabilities are rated as high severity.
- CVE-2020-11651 …the salt-master process ClearFuncs class does not properly validate method calls. This allows a remote user to access some methods without authentication. These methods can be used to retrieve user tokens from the salt master and/or run arbitrary commands on salt minions.
- CVE-2020-11652 …the salt-master process ClearFuncs class allows access to some methods that improperly sanitize paths. These methods allow arbitrary directory access to authenticated users.
Salt has since published updates that patch these vulnerabilities. However, over the last few days, there has been a steady increase in the number of companies reporting unpatched, compromised SaltStack instances.
Preventing Exploits of These CVEs
While we recommend that the updates be installed immediately, cloud admins should also take this opportunity to ensure their Salt environments are not exposed publicly, which is a key enabling component of this attack vector. Automatically scanning the configuration of these specific services across clouds is exactly what Aqua CSPM is about.
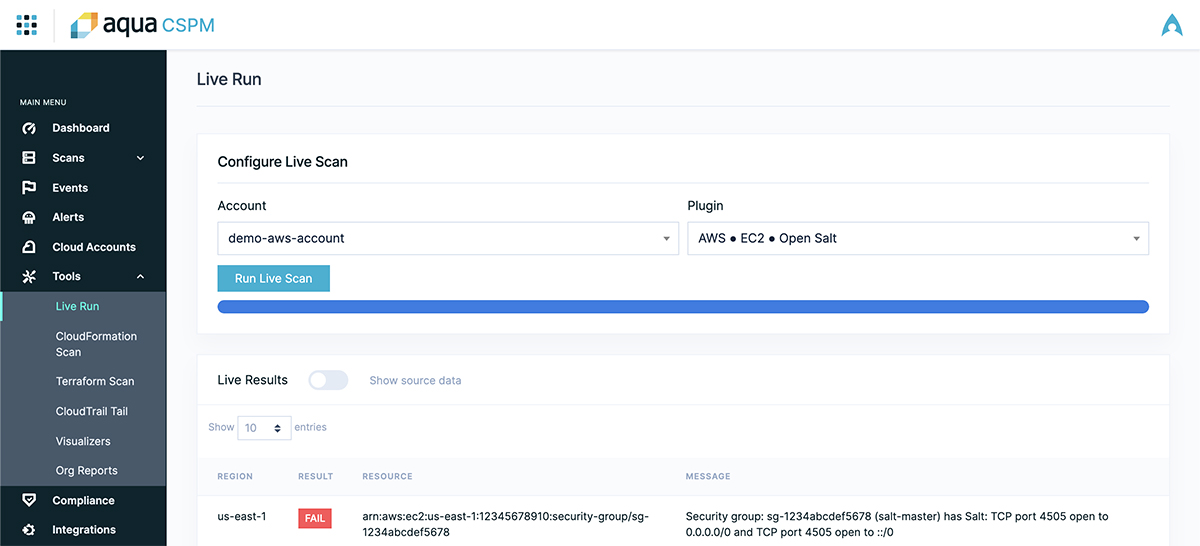
Mitigation with Aqua CSPM
We released three new plugins for Aqua CSPM to help address these issues, which are being enabled immediately for our customers. These plugins detect the exposure of ports 4505 and 4506 to the public internet (0.0.0.0/0) via instance security group rules. These nodes should have their security groups updated to only allow traffic from known IP addresses belonging to the Salt minions and required administrative endpoints.
- AWS EC2 Open Salt
- Azure Network Security Groups Open Salt
- Google VPC Network Open Salt
One Aqua CSPM customer has already used this capability to scan their environment and found no fewer than 20 exposed instances. These plugins are also available via CloudSploit, our open source CSPM auditing tool.
Although the importance of detecting cloud-based risks and quickly remediating them has become very apparent, this latest issue still serves as a solid reminder. Ensuring the security of your public cloud IaaS and detecting configuration issues across any cloud is more important than ever. But adding to that is the significance of getting detailed, actionable direction and enabling users to quickly fix and re-evaluate issues as they come up – something that is served well by the extensible, plugin-based architecture of Aqua CSPM, across multiple cloud services.