Aqua Security’s open source project Trivy now includes scanning of AWS CloudFormation templates to help developers better identify and remediate security issues within infrastructure as code (IaC) templates. Building on the technology and rule sets behind our popular open source project tfsec, Trivy now allows developers to evaluate AWS CloudFormation code, either locally or within their pipeline, for configuration issues and violations of best-practice policies.
Infrastructure as code (IaC) increasingly serves as a cornerstone of DevOps. Tools such as AWS CloudFormation, HashiCorp Terraform, Azure Resource Manager, and Red Hat Ansible enable developers to automate infrastructure provisioning and ensure deployment consistency. As IaC adoption has grown, however, so too have the security risks: without the right guardrails and guidance in place, IaC tools can often effectively automate and scale the wrong configurations.
Incorporating scanning for container and artifact vulnerabilities as well as misconfigurations via IaC security checks and rulesets with Trivy is representative of our broader strategy for helping teams to shift further left with the open source tool. Over time, we plan to add support for more file types, and make it easier for teams to maintain a global approach to identifying misconfigurations and potential runtime security issues across file types and IaC toolsets.
How Trivy IaC scanning works
Running manually on a developer’s machine or automatically in CI pipelines, Trivy scans both YAML and JSON AWS CloudFormation files (in addition to any other IaC files it may find) and provides rich information about any security issues that it finds, including analysis of AWS CloudFormation intrinsic functions. AWS CloudFormation intrinsic functions are used to incorporate dynamically generated values in templates that are fetched in runtime.
With developer-friendly output based on fully documented checks, Trivy helps teams detect and remediate policy fails as quickly and efficiently as possible.
Developers can include Trivy scanning in their CI/CD tools, including GitLab CI, Travis, Jenkins, CircleCI, GitHub Actions, and Bitbucket Pipes builds.
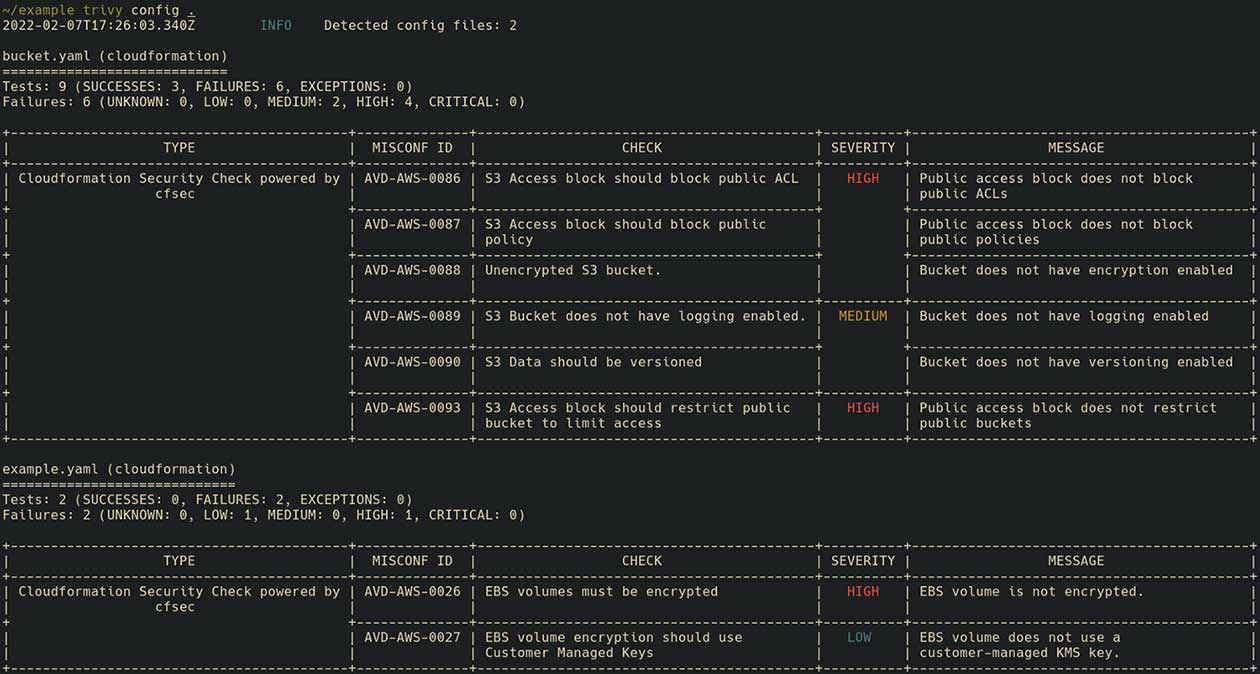
Sample scan input for an AWS S3 bucket and Amazon EBS volume files
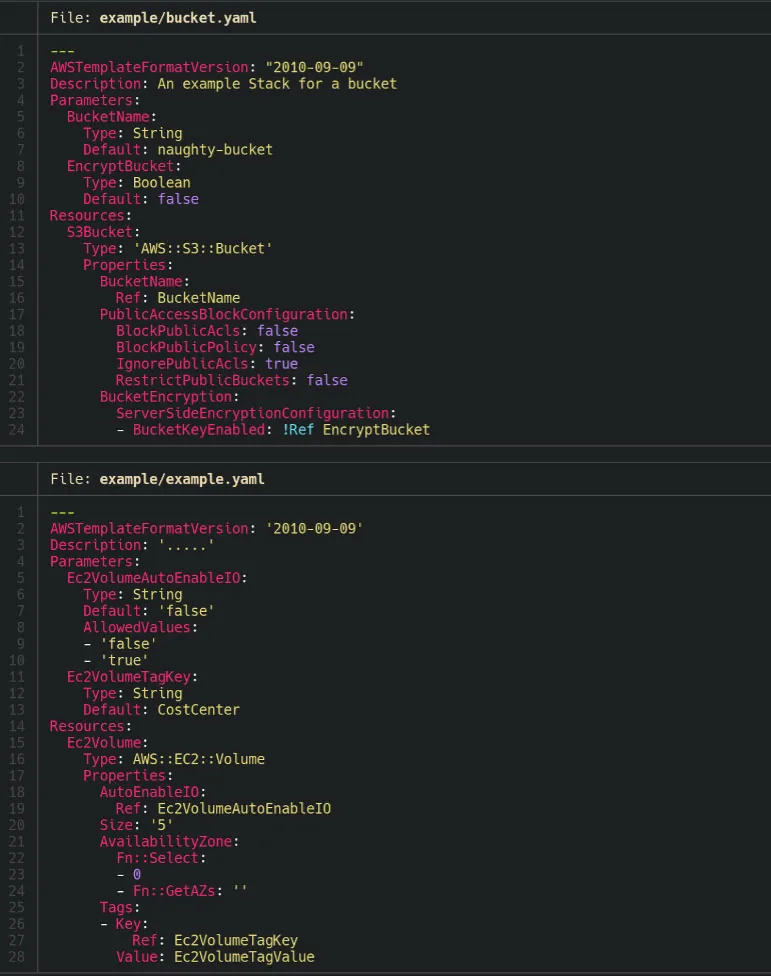
Sample scan output and findings for AWS S3 bucket and Amazon EBS volume CloudFormation files
Ensuring accurate interpretation of IaC all the way to runtime
IaC security tools can seem straightforward at first blush. They involve parsing a template to assess whether configurations meet policies and security best practices. Based on the results, the tools can show users where additional hardening may be required to enhance the security of their environments, and how to avoid common misconfigurations that attacks can exploit.
Static analysis using string matches can serve as a starting point for identifying configuration issues in IaC files. However, iterating string matches across the file will identify issues specific to individual configuration settings — but not potential issues in deployment state once the code has been executed.
Key to understanding of the deployment state is evaluating the entire stack and dynamic functions specified by the template for runtime. Extending the work done by the tfsec team to simulate how resources are deployed to identify security issues in dependencies or environment variables in Terraform, Trivy’s AWS CloudFormation scanning also evaluates intrinsic functions.
AWS CloudFormation templates utilize intrinsic functions to assign values to properties that are not available until runtime and define conditions for stack resources. Intrinsic functions can be used in resource properties, outputs, metadata attributes, and to update policy attributes. Without the use of intrinsic functions, developers are confined to authoring basic resource stacks within templates. However, scans based on string matches only stop short of assessing the potential security and risk outcomes of executing intrinsic functions – and for maintaining an effective feedback loop to avoid future misconfiguration risk.
Evaluating these functions as part of the processing allows Trivy to build an accurate view of the CloudFormation templates’ intent, providing a richer view of the full stack and eventual deployment state.
As teams progress in their DevSecOps maturity, they can move beyond reducing the attack surface through IaC scanning for identifying individual configuration issues to understanding how risks introduced through IaC code can result in runtime security issues. With these level of insights into the file structure and the impact of intrinsic functions on deployment state, DevSecOps teams can better identify the conditions that lead to misconfigurations and collaborate effectively on mitigating risk.
Try scanning AWS CloudFormation code with Trivy
The rationale for IaC security is obvious. It’s always less resource-intensive to prevent mistakes at the outset than to resolve the consequences of the mistake in production. The challenge is to identify what the mistakes are, without detracting from the rationale for the adoption of IaC: speed, automation, consistency, and often cost.
With the community behind tfsec having already paved the way in terms of usability and speed for scanning and remediation, now AWS CloudFormation users can take advantage of Trivy and contribute to the project.