There are many benefits to implementing CI/CD platforms, such as enabling fast and frequent release cycles of software and applications, but with great speed comes great responsibility. It is crucial to add security controls around container image creation and deployment to ensure that your applications are properly secure before they are deployed.
Scanning of Docker images during the CI stage provides a quick and short feedback loop on security as images are built. You want to discover unsecured images well before you deploy them, and enable developers to fix them quickly, rather than wait until issues are found in production. You should also avoid unsecured images in your testing/staging environments, as they could also be targets for attack. Aqua’s image scanning and image assurance can be implemented in a number of CI/CD tools, including the Codefresh CI/CD platform.
Codefresh describe themselves as the first CI/CD platform built for Kubernetes. Codefresh pipelines contain steps that include the building, testing, pushing, scanning, and deployment of images. Their platform enables an integration with Aqua, which can be automated as one of the steps in their pipeline.
Codefresh has a plugin architecture called freshSTEPS, which now has a dedicated Aqua step to automate image scanning. This step conducts image scanning to find known vulnerabilities, malware, embedded secrets, configuration issues, and open source licensing issues in your image build.
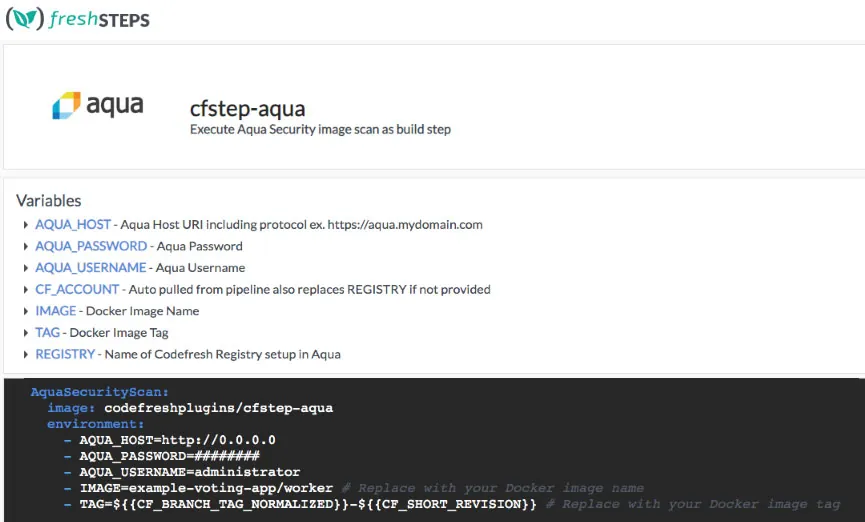
As you can see below, the Aqua Security scan is added as a step in the build process:
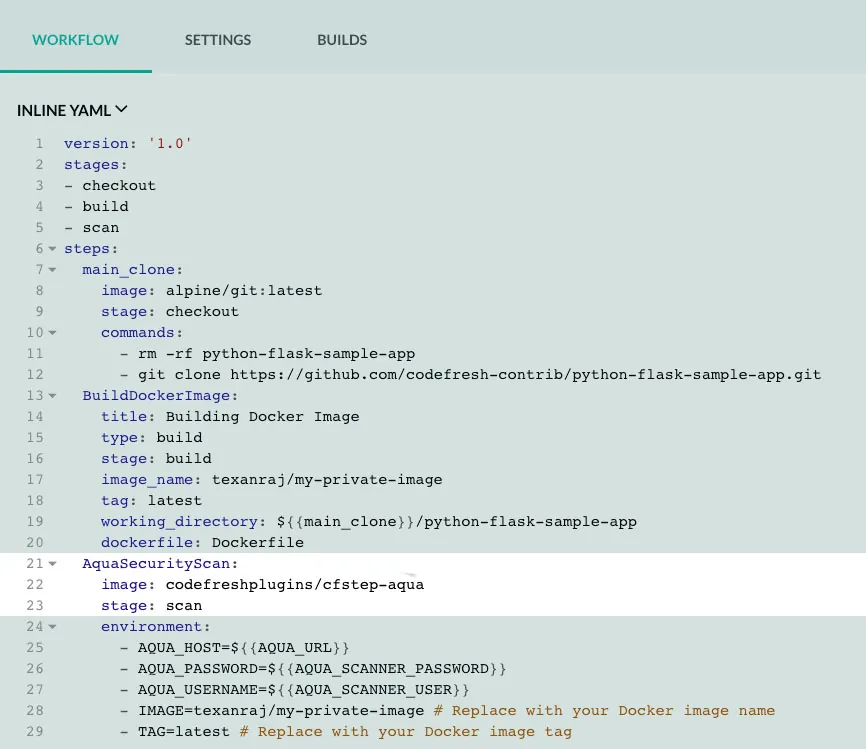
Image Security Policies in Action
Aqua provides flexible policies to set your appetite for risk in various applications and environments. For example, you can differentiate between customer-facing and internal apps, or between PCI and non-PCI apps. Various aspects can be set and determine whether an image will pass or fail your criteria, and also what actions will be taken in case of a non-compliant image – such as failing the CI build, blocking its deployment, or both.
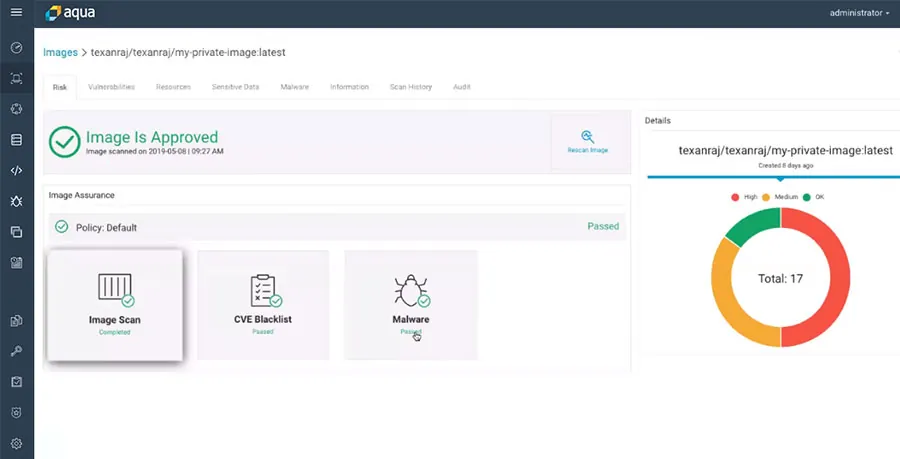
If the image was scanned and no issues were found that violate the policies (in the case below, malware and blacklisted CVEs, as well as the completion of the scanning itself), the Aqua Console will show it was approved.
If an image was deemed non-compliant (in this case due to a severe vulnerability that was found), it will appear as a non-compliant image in the Aqua Console. Clicking on the Vulnerabilities tab will provide additional CVE information as well as possible remediation steps.
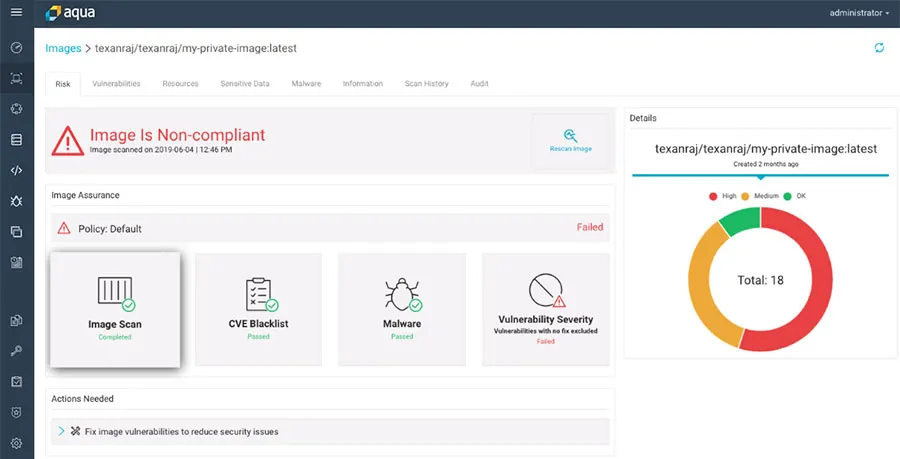
More importantly, in the Codefresh UI the developer will also notified that the build failed. Security teams can set the policy to only alert on security issues found during build, but in this case the policy was set to fail the build. This allows security teams to ensure that no serious issues make it even into a staging environment, while providing feedback to developers right within their CI environment, shortening that time-to-fix loop.
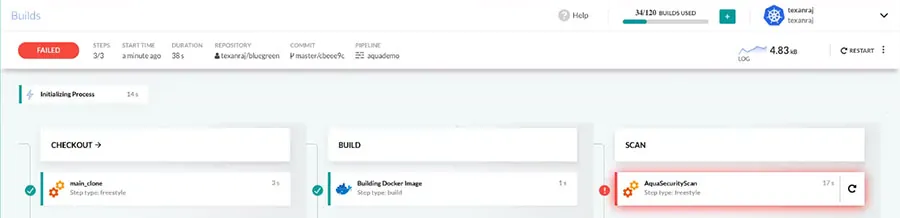
In the case of non-compliant images, even those that are set to pass builds, Aqua can later block their use or deployment across Kubernetes clusters and hosts, so there are multiple security check-points within the CI/CD process.
Summing it Up
Codefresh’s platform provides a unique way of implementing CI/CD for Kubernetes and Docker by using steps. By integrating the Aqua security platform as one of the build steps, Codefresh’s CI/CD benefits are augmented by providing the user with protection against security threats and vulnerabilities often found in this space.
Join us for this webinar with Aqua and Codefresh for a live demonstration of the image scanning in the CI/CD pipeline.

