Published sources of vulnerabilities in cloud native environments are an important resource, but the information is often spread out across a variety of platforms. Since 80% of cloud native software is based on open source, this makes getting the most relevant and up-to-date vulnerability information a real challenge. Our new Aqua Vulnerability Database (AVD) consolidates these splintered sources into a single, easily accessible view. And as most public and hybrid cloud deployments run on Kubernetes, users will appreciate that AVD merges information for open source vulnerabilities with Kubernetes best practices and hardening, and best practices for cloud account configurations.
In addition to consolidating information from disparate sources such as NVD, vendor security advisories, and various articles and forums, AVD also breaks down outdated information barriers. All too often, knowledge is siloed amongst security experts, or even within security teams, but AVD provides a simpler way for security professionals, developers, and operators to find information on the articles and vulnerabilities that they encounter every day.
AVD Interface, Free-form Search, Mitigation Resources
AVD offers a free form, type-ahead search input where you can either search by a keyword (e.g., “openssl”) or by a CVE-ID (e.g., CVE-2020-1234). Having a free form search makes it easy to look for articles or vulnerabilities that you might not be aware of through identifiers such as CVE IDs.
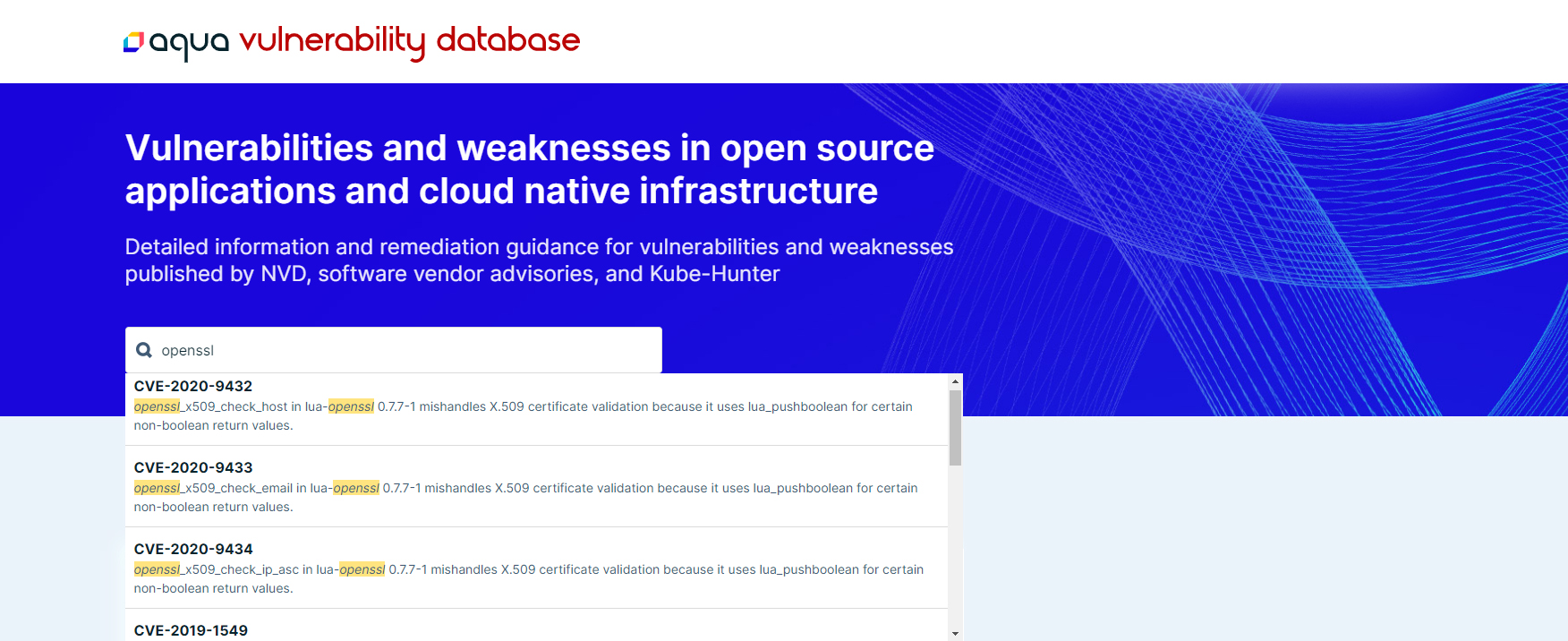
Vulnerability Information
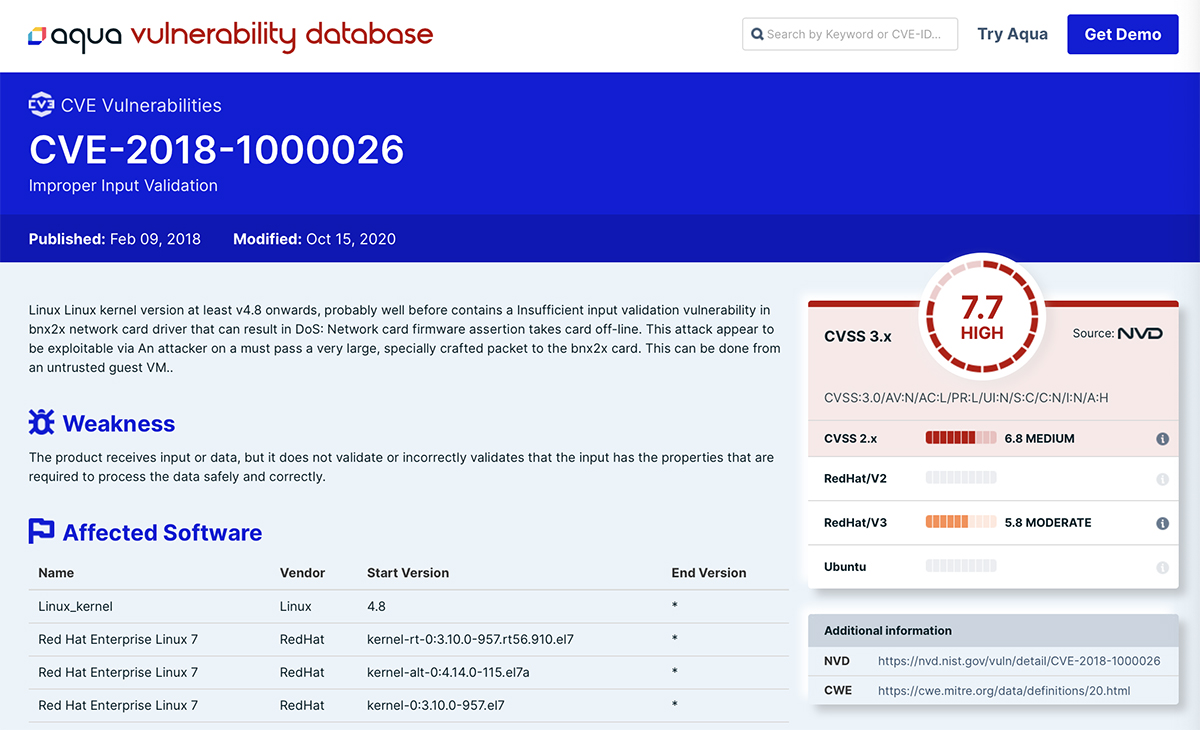
We retrieve information about each vulnerability from a variety of sources so that we can publish a comprehensive list of vulnerability scores across various vendors for each CVE ID.
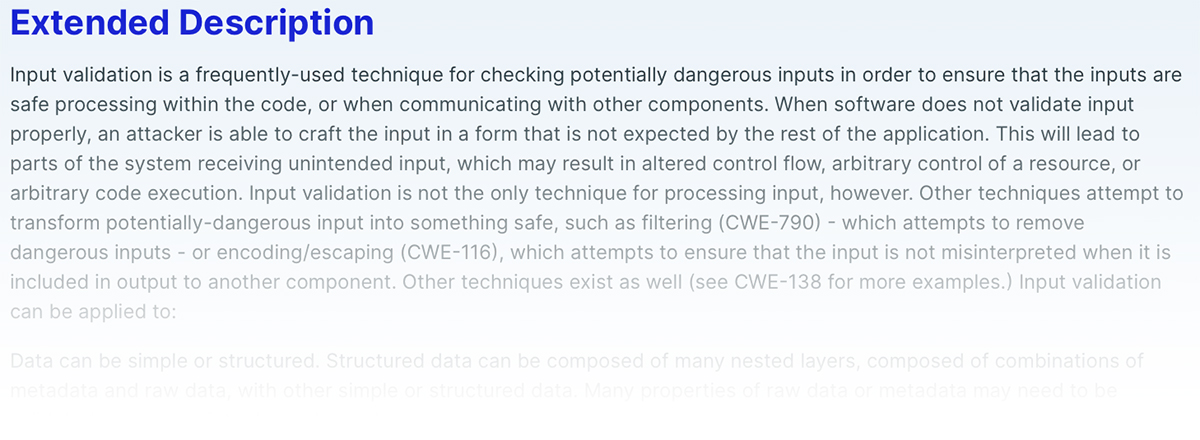
We also present extended information about each vulnerability that defines the various attack vectors that the adversary can take to exploit the vulnerability.
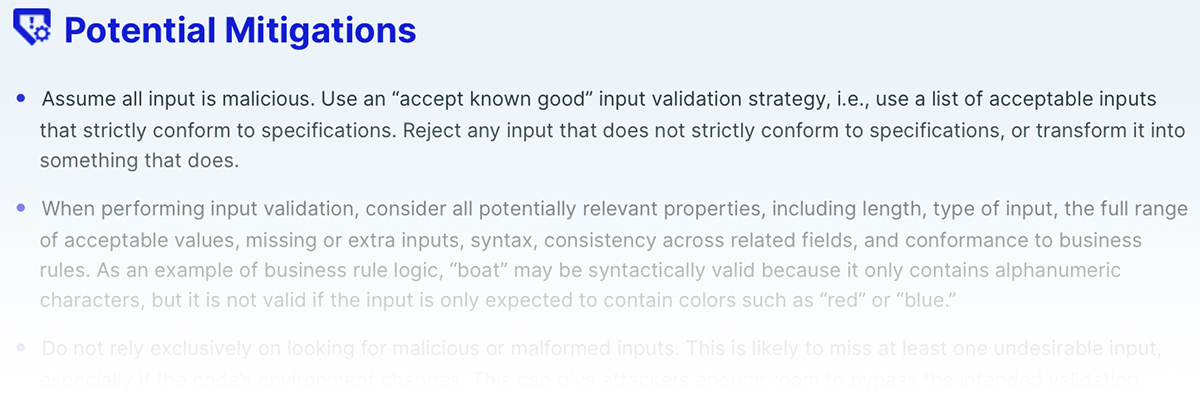
To help the reader, a list of potential mitigations is also presented which includes general hardening techniques and other mitigation strategies related to the vulnerability at hand.
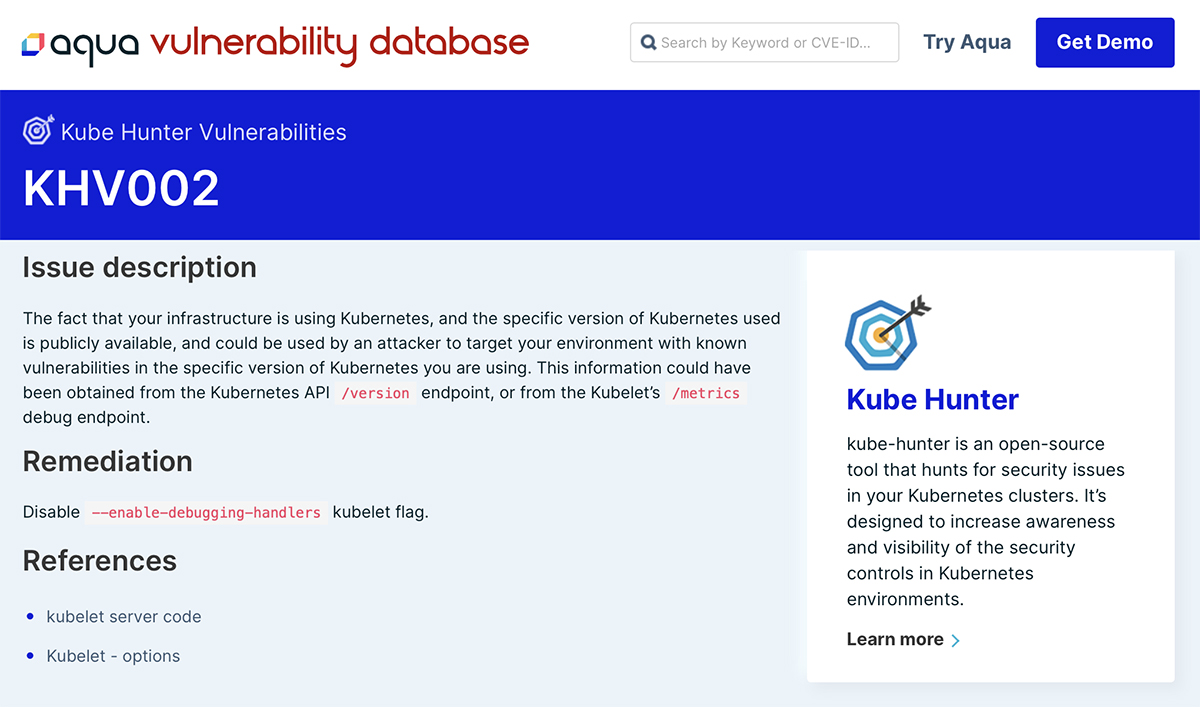
kube-hunter automated pen testing
AVD also includes information about strengthening your Kubernetes clusters. This is powered by our open source tool kube-hunter.
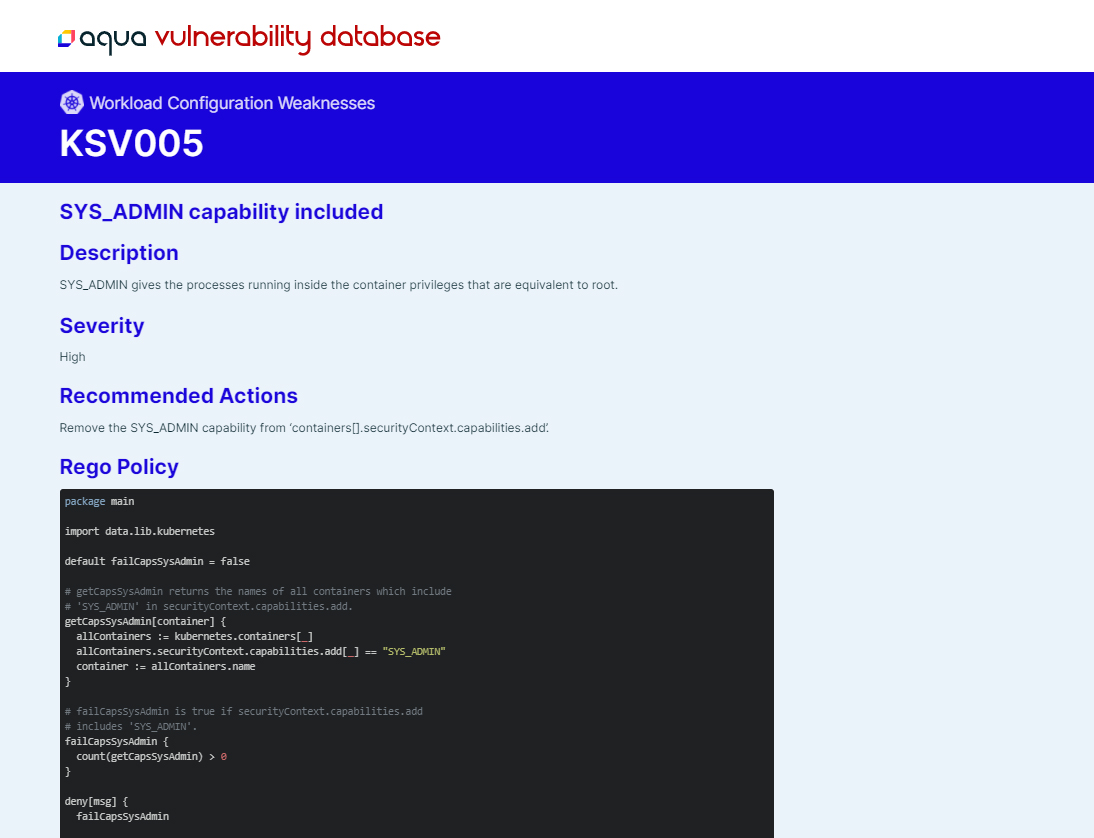
AppShield
Aqua also publishes a set of vetted and validated Rego policies to safeguard users against Kubernetes attacks through our open source project AppShield. These policies are shown as part of AVD’s AppShield advisory pages. Each policy has recommended action items that both Kubernetes admins and end users can apply to their clusters to improve the overall security posture. Furthermore, the Rego policy enables these checks to be applied through a policy agent like OPA.
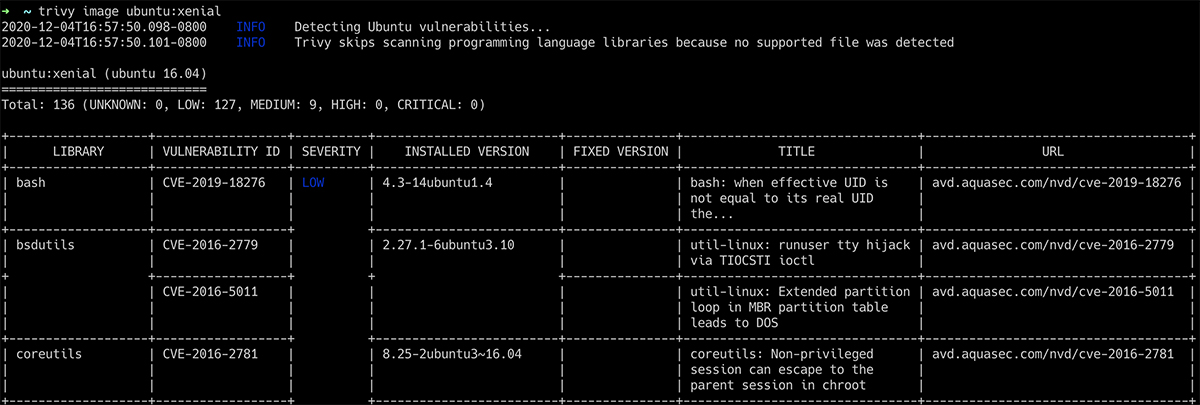
Integrating Trivy with AVD
To make using AVD even easier to use, we augment Trivy scan results with embedded AVD links. Now with every Trivy scan, in addition to the existing information about the vulnerability, you’ll also see a link to the vulnerability page on the AVD. This functionality will be included in the latest release of Trivy.
Integrating Lens IDE with Starboard, Trivy, and AVD
Lens IDE is an IDE for Kubernetes operations management. We recently published an extension for Lens IDE that integrates Starboard reports into the Lens UI. And based on that, we added AVD integration into the Lens Starboard extension as well.
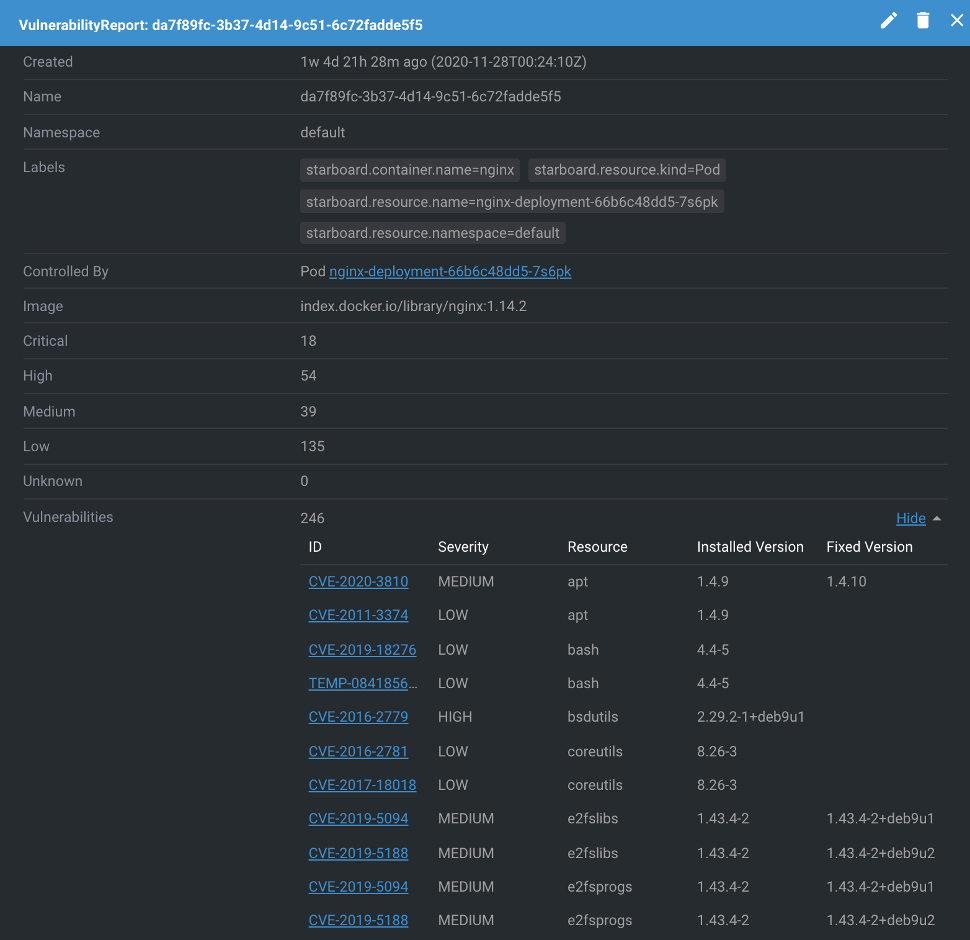
By clicking on each vulnerability, the corresponding AVD page will be shown. This is possible with Starboard’s Vulnerability Reports that get generated through Trivy as the vulnerability scanner. By combining three of our products, we provide an easier to use, more complete picture of the security report.
Trying out AVD
AVD is now live and integrated within Trivy, the world’s best open source vulnerability scanner, or available through Aqua Wave. Delivering robust scanning capabilities for teams of any size, Aqua Wave is also very easy to use — just sign up and run.

