A new vulnerability was discovered earlier this week in the sudo package. Sudo is one of the most powerful and commonly used utilities installed on almost every UNIX and Linux-based operating system.
The sudo vulnerability CVE-2019-14287 is a security policy bypass issue that provides a user or a program the ability to execute commands as root on a Linux system when the “sudoers configuration” explicitly disallows the root access. Exploiting the vulnerability requires the user to have sudo privileges that allow them to run commands with an arbitrary user ID, except root.
Verifying Exploitation of the Vulnerability
The following terms need to be met before exploiting:
- In the /etc/sudoers file, a user should be granted permission to execute programs as any users except root.
- The user has sudo privileges that allow them to run commands with an arbitrary user ID.
Run Sudo command with User ID -1 or 4294967295
The function which converts user id into its username incorrectly treats -1,or its unsigned equivalent 4294967295, like 0, which is always the user ID of root user.
Checking if Your Environment is Affected
To find out if you are vulnerable you will have the sudo version prior to 1.8.28 and run the following command in your terminal to seek for a match:
cat /etc/sudoers | grep “(s*ALLs*,s*!roots*)” |
cat /etc/sudoers | grep “(s*ALLs*,s*!#0s*)” |
Use Aqua to Mitigate and Detect the Vulnerability
This security vulnerability is more interesting than concerning as the sudo package is not commonly run in containers. Containers usually run with a single user with ability to run as root in the container but not outside of it. Further, there is no typical operational reason to run a container with more than a single user.
However, in the event sudo is in your container environment in a fundamentally insecure way this is how Aqua can help you:
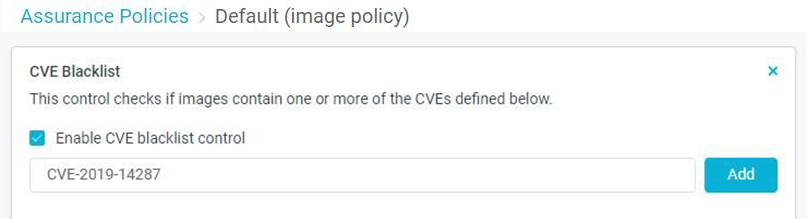
Aqua Image Assurance policy
- Create an assurance policy that scans your container images and find out which images are exposed to the vulnerability
- Allow only specific versions of packages to run
- Apply the policy on your Container images or your VM (Host)
- Prevents affected images from being deployed in your environment, preempting operational errors, image sprawl, and rogue deployments
- Integrates with your pipeline to scan images as they are built
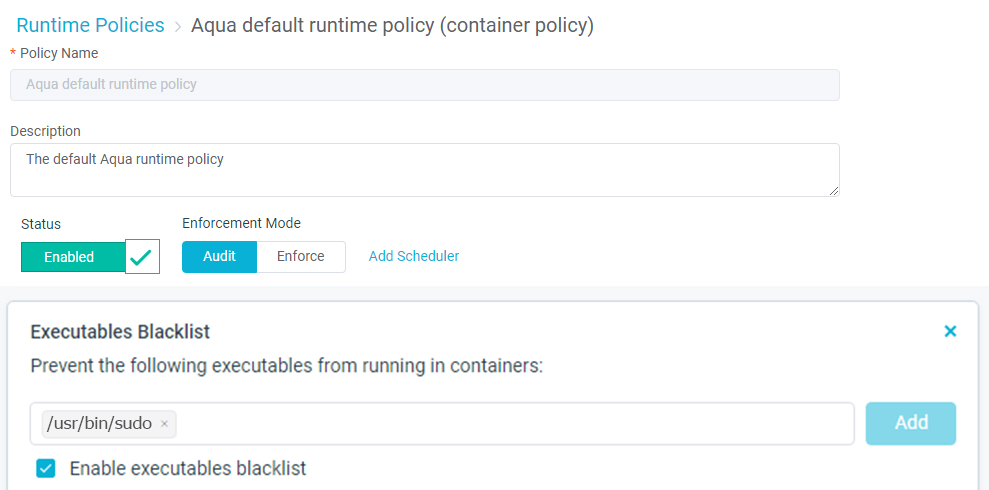
Aqua Runtime protection
- Implement immutability on your running containers
- Monitor and control container activity in real-time
- Prevent images from running whose parameters have changed
- Alert on or block unauthorized processes without killing or pausing containers
Aqua Image profile
- Provides controls to define authorized image activities
- Apply to containers instantiated from a specific image
These features and more can help you to have more control and visibility. Use Aqua to protect your Cloud Native environment without disrupting business continuity or pausing containers.

