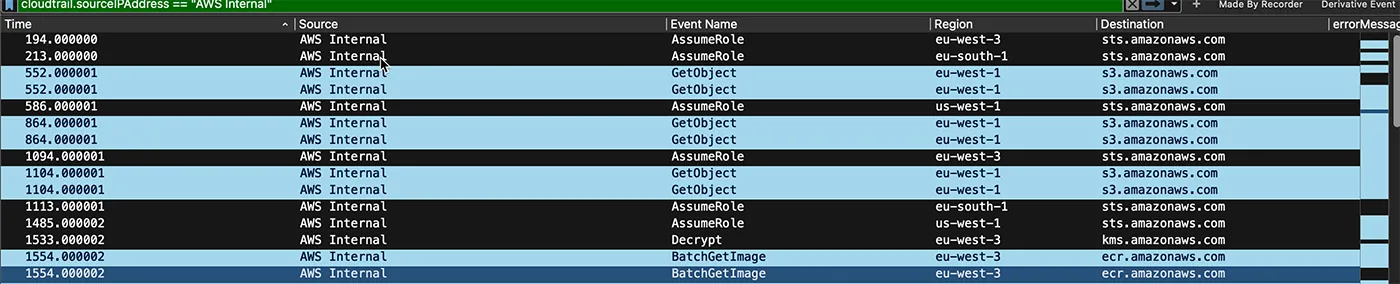
In this blog, we introduce TrailShark, a plugin that connects Wireshark with AWS CloudTrail logs. This open-source tool was developed as part of the “Bucket Monopoly” research, during which we identified six vulnerabilities in AWS by tracking service interactions and internal API calls. These vulnerabilities range from remote code execution (RCE) and full-service user takeover (which could provide powerful administrative access) to manipulation of AI modules, exposure of sensitive data, data exfiltration, and denial of service.
What is TrailShark?
TrailShark Capture Utility is a tool designed to integrate AWS CloudTrail logs directly into Wireshark. This integration allows for near-real-time analysis of AWS API calls, providing invaluable insights for debugging, security and research. With TrailShark, you can capture and examine the internal API calls triggered by AWS services, better understand what is “running under the hood”, consequently shedding light on potential vulnerabilities and security flaws.
Key Features of TrailShark
1. Near-Real-Time Visibility with Advanced Filtering
TrailShark offers near-real-time visibility into AWS CloudTrail data, enabling you to monitor API calls as they happen. This feature enables you to utilize Wireshark capabilities, with its worldwide popularity, advanced filtering and community support, to understand what happens once you create services on AWS and use it for debugging and possibly identifying hidden activities.
2. Inner API Call Analysis
One of TrailShark’s standout features is its ability to analyze the internal AWS API calls made in response to user-initiated activity. This deeper level of analysis provides a comprehensive understanding of AWS service interactions, allowing you to pinpoint exactly where anomaly may lie.
3. Custom Event Creation
TrailShark allows you to create custom events based on specific criteria. In our research for instance, we created a custom event that highlighted unusual API call patterns or the creation of unintended resources like S3 buckets.
Below you can see a demo illustrating the creation of a CloudFormation stack:
Usage Example
1. Shadow Bucket Creation
In the “Bucket Monopoly” research, we utilized the Wireshark GUI to examine the internal API interactions. We found an automatic creation of an S3 bucket as part of AWS CloudFormation operation. This is used later to store templates.
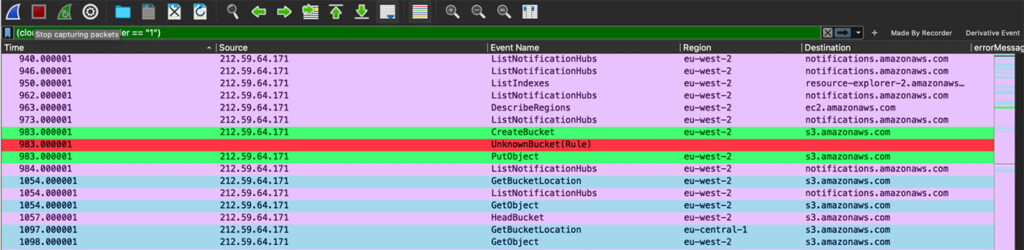
In this image, you can see 3 events marked in green and red. The first green event is a bucket creation, the second green is putting something in the bucket, and the red is a rule we wrote to detect a hidden resource (bucket) creation
2. Inner API Calls
Occasionally, AWS initiates backend API calls on your behalf to enhance and complete missing data or to initialize services. Security practitioners, researchers in particular can benefit this capability to reveal valuable insights.
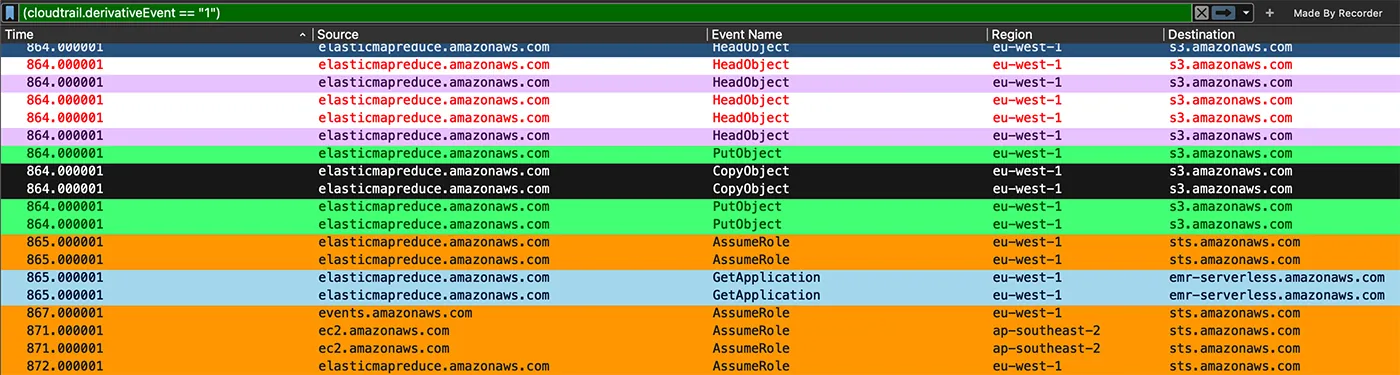
Furthermore, you can also view inner AWS API calls as part of the inner service communication, such as the internal API calls, seen below, between the two service: EMR writes objects to S3.
Conclusion
TrailShark represents a significant advancement in AWS CloudTrail analysis, offering near-real-time visibility, API call analysis, and customizable event creation. By integrating seamlessly with Wireshark, TrailShark empowers users to uncover hidden AWS internal activates swiftly, enhancing the security and transparency of AWS environments.
Disclaimers
TrailShark offers a lightweight solution for recording CloudTrail data and analyzing it with Wireshark.
It’s imperative to mention other tools like Falco who created solutions for integrating CloudTrail logs with Wireshark using Falco agents. In this context, TrailShark is more optimized for near-real-time capture and analysis in addition to enable wide range of customization for these purposes.
For more information and to access TrailShark, visit our GitHub repository here. Join us in making AWS environments more secure and transparent.