Data breaches and ransomware attacks have become a common headline around the globe. Meanwhile, protecting cloud environments has turned into an uphill battle for even the most seasoned CISO. With a broader attack surface, the dynamic nature of open source software, and a growing number of vulnerabilities being discovered each year, being prepared for the next cyber attack is no small task.
Recent statistics such as IDCs revelation that 98% of all companies have experienced a data breach within the past two years, serve as a sobering reminder of the urgency of the situation. These breaches often stem from security gaps within either the software supply chain or production environments. A deeper dive into the numbers from Aqua Nautilus research reveals a startling trend: attacks targeting the code, infrastructure, development tools, or software development process increased by a staggering 300% last year alone.
Why has the battlefield shifted to include the software supply chain? A simple reason – profitability. Imagine you’re a hacker with a choice. You can either spend weeks, if not months, trying to find a vulnerability in one well guarded corporate network or heavily fortified application. Or you can focus on compromising an unmonitored component of an organization’s software supply chain that grants you access across many systems. If you’re even luckier, and you manage to infiltrate the development process of a software vendor, as a hacker you’ve gained the power to infect all of their customers with just one successful breach.
It’s also an inconvenient truth in the world of cybersecurity that application security tools primarily cater to development teams. While these tools identify vulnerabilities in the code, configuration issues, and application dependencies, they lack integration with the broader production environment and security team. This fact makes it difficult for security to stay ahead of threats that target the software supply chain. Effectively blinding them to the source of risk and preventing them from accurately catching and prioritizing threats.
For example, attacks like the Codecov breach are one of many that evade traditional application scanning by compromising the development process. In this case, a software supply chain component (the developer tool) is exploited, then used to inject malicious code. The code changes go undetected because they’re being executed from a trusted source. These abnormal activities could only have been identified by monitoring the entire development process and identifying suspicious behavior that deviates from typical pipeline activity before production.
Therefore, not all vulnerabilities, misconfigurations, and anomalous activity are created equally. Some may have a minimal impact on security, while others could potentially result in a devastating breach.
Without full context, every issue identified, regardless of its actual risk level is communicated to the development team as a critical problem that requires immediate attention. Even if the vulnerability doesn’t create a direct exploit path for attackers to compromise the system.
Cloud security teams are suffering from an inundation of risk alerts that don’t provide the full context needed to analyze the risk to the organization, and as the number of CVEs discovered continues to rise so does the backlog of security remediation efforts put on development. This disconnect creates friction, stalls the issue resolution process and lengthens the window of exposure for organizations when zero-day threats materialize.
Even Gartner emphasizes the importance of an integrated platform:
“As organizations shift to a CNAPP-based approach, the synergy of an integrated platform will provide more benefits than a best-of-breed strategy that is difficult to scale.”
Aqua’s CNAPP stops cloud breaches by distinguishing critical issues from the noise of countless security alerts, stopping attacks at their source, and resolving root causes swiftly. With integrated visibility and control over both the software supply chain and the production environment to significantly reduce the time to detect, respond, and remediate security incidents. This paves the way for a more resilient cloud security posture, better equipped to defend against and prevent threats across the entire application lifecycle.
Transforming how cloud risks are discovered: Cloud-to-Code Tracing
The Aqua platform monitors, tracks, and visualizes the entire threat landscape. This makes it possible for security teams to view end-to-end risk in real-time, so that any changes to the code base, open source components, pipeline activity and configurations, are always reflected with their impact to production.
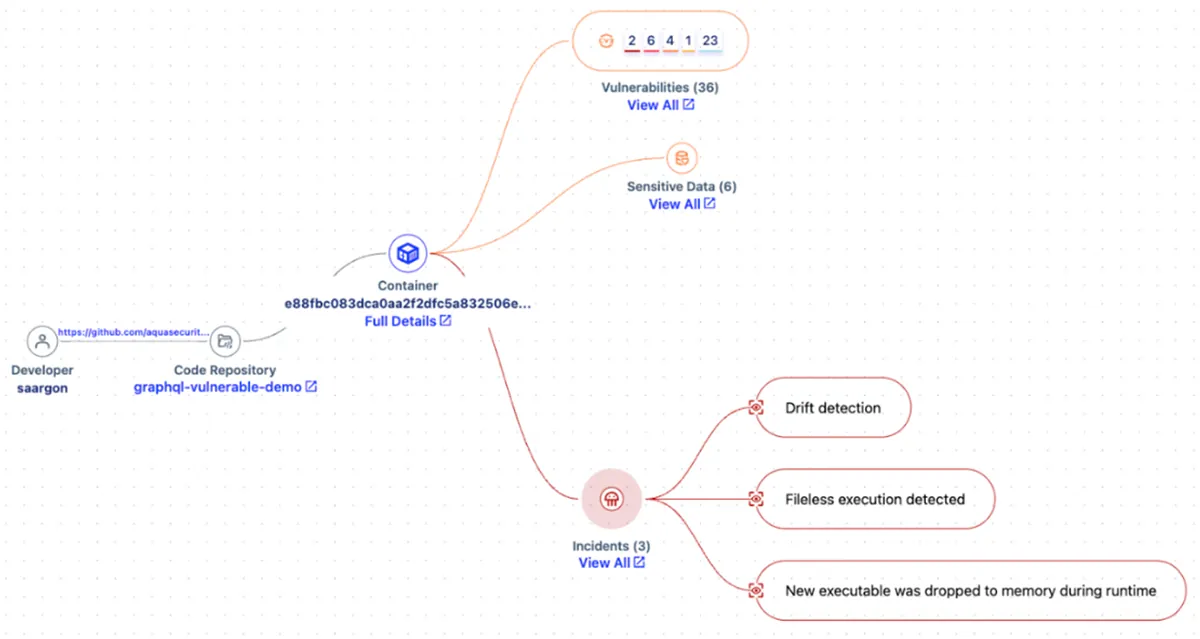
Aqua’s Cloud-to-Code Tracing enables security teams to view risk in production and directly trace it back to the code repository and developer responsible, all within one graph. Unlike limited tools that focus on one securing one element in the application lifecycle, Aqua closes gaps in threat correlation by identifying compounded risk. Compounded risk is a series of minor threat indicators that when added together amount to critical risk.
Equally as important as seeing threats, is the ability to stop the threat. Aqua delivers vulnerability intelligence to the developer in their IDE, highlighting the line of code causing the problem and a suggested fix. This cutting edge communication process between teams prevents developers from slowing down and impacting velocity and reduces remediation efforts by as much as 80%. The security graph above from the Aqua Cloud Security Platform visually represents the cloud-to-code relationships in one complete view.
To illustrate the impact of this innovation, consider the scenario where a vulnerability like log4shell surfaces within a running container. Aqua’s technology swiftly identifies the relevant source code repository and the associated Dockerfile responsible for introducing the vulnerable package, all while tracking ownership. Furthermore, Aqua precisely pinpoints the exact line within the Dockerfile that led to the vulnerability and offers a recommended course of action to the developer.
This streamlined approach expedites incident response and dramatically shortens the window of exposure to potential exploits. With the ability to trace risk from cloud-to-code, security teams accurately assess their cloud security posture, drill into the root cause of issues and fix them. Security can:
- Automatically link risks in production to the dev pipeline
- Ensure that priority issues are resolved quickly
- Empower developers to take ownership of security
- Dramatically simplify and accelerate the remediation process
Delivering a Single Source of Security Truth and Enforcement
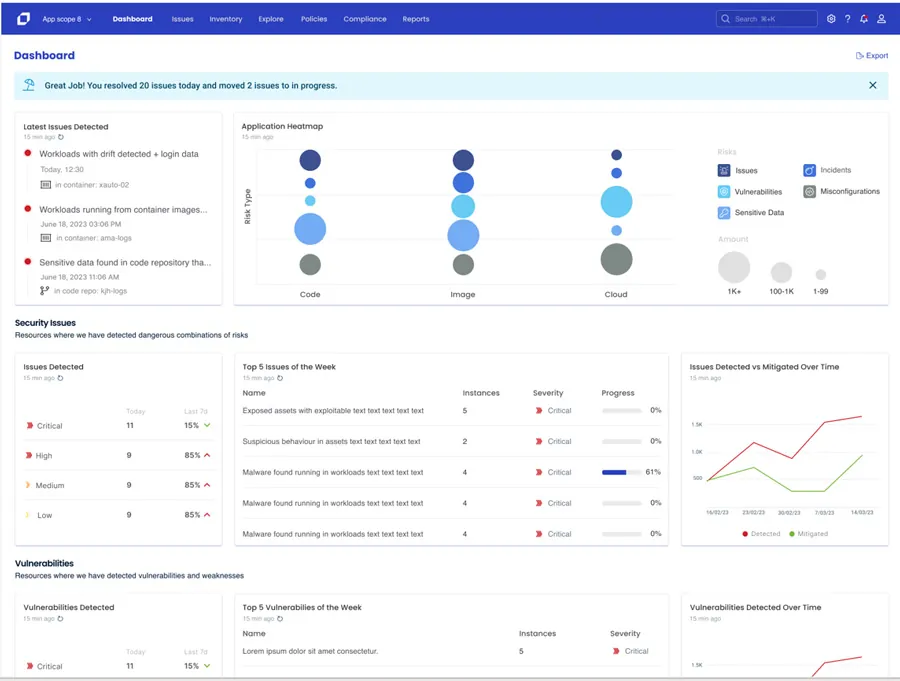
Aqua’s dashboard serves as a holistic view of your organization’s cloud security risk and is a customizable way to measure activity across the code, infrastructure, and production environment. Moreover, providing an easy way to understand security trends over time. With Aqua’s dashboard you can track the evolution of security issues from detection to mitigation, to see at a glance how your security posture improves as vulnerabilities are addressed. By tracking security issues, the dashboard helps you allocate resources effectively by pinpointing areas with the most outstanding risk. Teams armed with real-time data make informed decisions about where to focus your security efforts and investments, strengthening your overall cyber resilience.
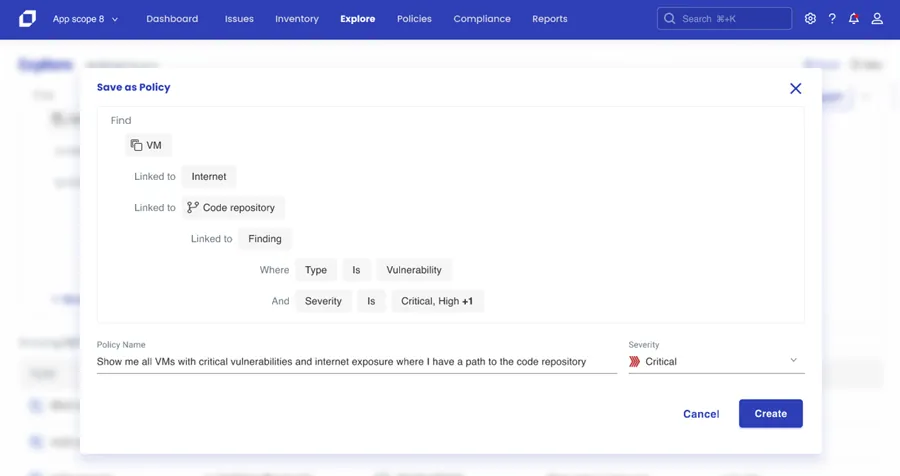
Whenever a new vulnerability is announced, security teams are in a race against hackers trying to find systems running with those CVEs. The first step in closing the window of exploitability is searching for your entire inventory of assets to identify which are impacted. In the screenshot below, teams explore the development to production landscape and select risk parameters that are specific to their unique environments. For instance, they may first need to find any VMs that have critical vulnerabilities, internet exposure, and a direct path to the code repository. This real-time ability to search insights better enables security teams to ruthlessly prioritize and close the window of exposure.
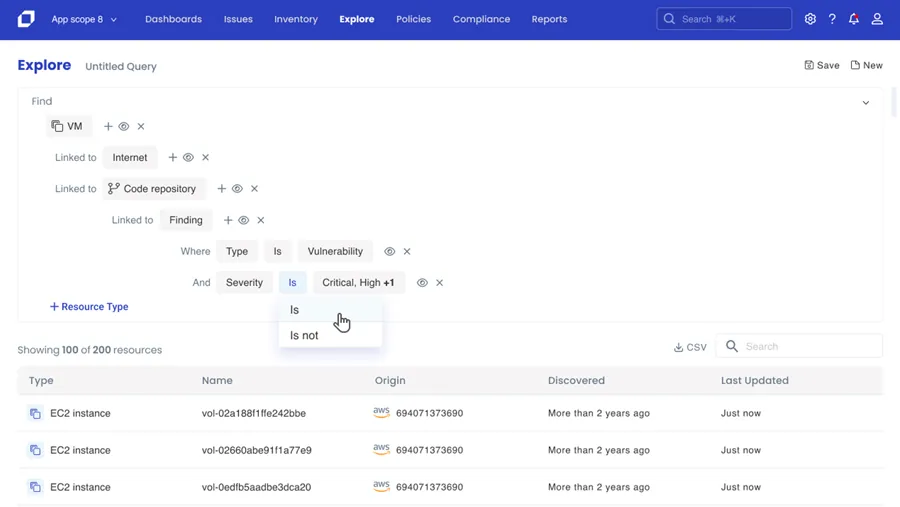
Below you can see how the narrow search of the cloud environment can then be saved as a policy. Now automation of security responses to different infrastructure, code repositories, vulnerabilities etc. can all be leveraged, helping security teams dramatically slim down the list of alerts being deemed critical so action is more impactful.
Commitment to Complete Cloud Security
Cloud-to-code tracing is a game changing approach that revolutionizes how cloud risks are discovered, prioritized, communicated between teams, and resolved. We at Aqua understand that it’s not just about seeing threats, it’s about stopping them in their tracks. The Aqua platform delivers an innovative approach to securing both the software supply chain and cloud so enterprises can not only keep up with threats but stay ahead of them.
In a world where cloud security challenges continue to evolve, it’s time to embrace the future of cloud security. To learn more about our Cloud-to-Code Tracing, check out our demo video above or schedule a full demo with our team today.