This holiday season, adversaries aren’t taking a vacation, massively exploiting multiple vulnerabilities in Log4j, a highly popular Java logging library. Amid the ongoing efforts of organizations to patch their vulnerable systems, a new Log4j vulnerability, tracked as CVE-2021-44832, has been discovered. It allows for an arbitrary code execution via JDBC Appender when an attacker can modify the logging configuration. Rated ‘moderate’ in severity with a 6.6 score, this is the fifth security vulnerability to be found in Log4j in less than a month.
Technical details
The newly discovered CVE-2021-44832 allows for a remote code execution (RCE) attack where an attacker with permission to modify the logging configuration file can construct a malicious configuration using a JDBC Appender with a data source referencing a JNDI URI which can execute remote code.
Fortunately for some users of applications that utilize Log4j, it seems, based on the project’s advisory page, that it will be harder for attackers to exploit this issue. A prerequisite for exploitation is that attackers have permissions to modify the configuration of the logging system, which is not likely to be the case in most scenarios where Log4j is used.
However, where that is possible, the attackers could use this to escalate their privileges by constructing a malicious log configuration that allows for remote code execution (RCE).
Log4j versions affected by CVE-2021-44832:
All Log4j versions from 2.0-alpha7 to 2.17.0, excluding 2.3.2 and 2.12.4
CVSS Score:
6.6 (moderate)
Mitigation:
Following the disclosure of CVE-2021-44832, Apache has released new Log4j version, 2.17.1. This issue is fixed by limiting JNDI data source names to the java protocol in Log4j2 versions 2.17.1, 2.12.4, and 2.3.2.
Log4j users are recommended to immediately upgrade to Log4j 2.3.2 (for Java 6), 2.12.4 (for Java 7), or 2.17.1 (for Java 8 and later). Log4j 1.x is not impacted by this vulnerability.
Detecting and mitigating the vulnerability with Aqua
As part of our ongoing program to ensure Aqua’s vulnerability database is consistently updated with vulnerabilities as they are identified, Aqua can identify and block the workloads that have CVE-2021-44832.
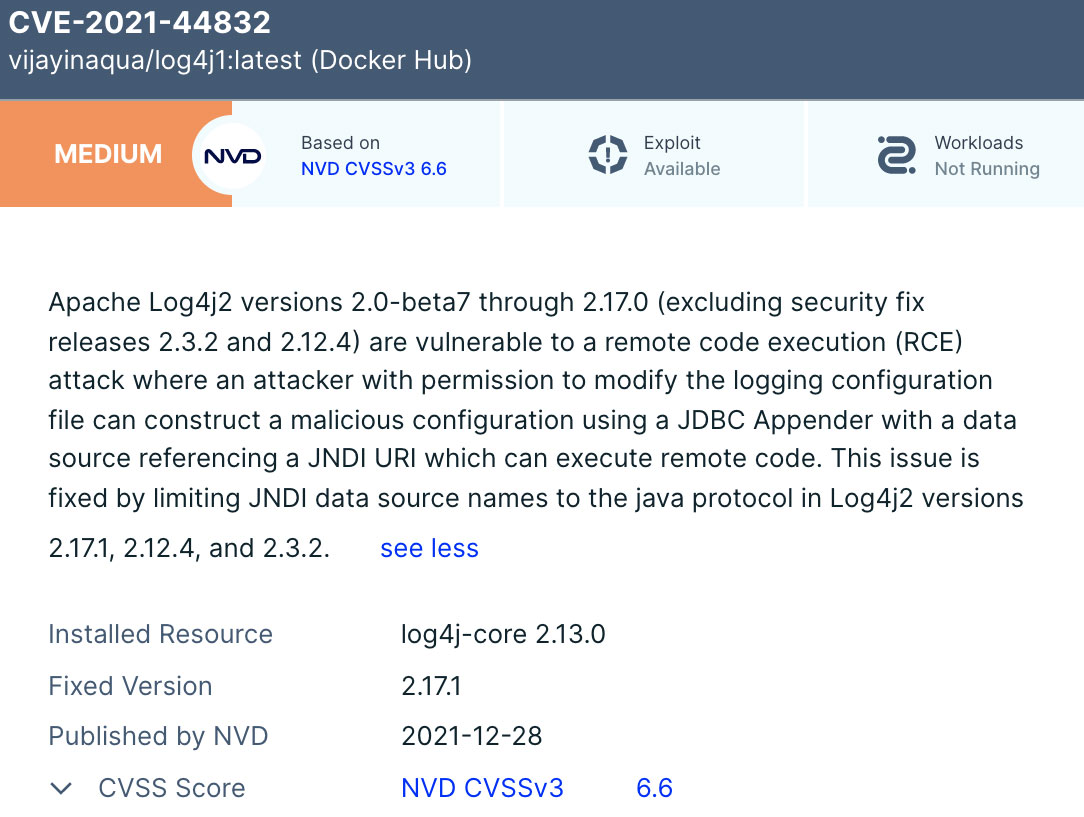
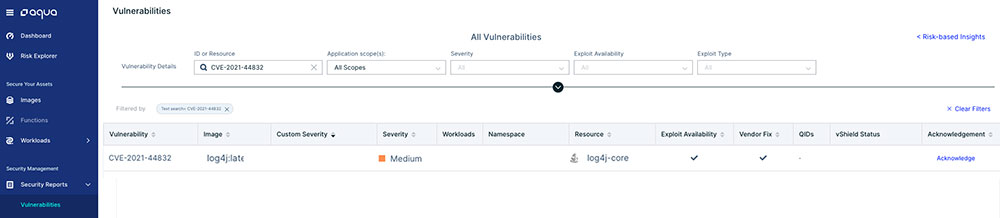
In the Aqua platform, you can see all the impacted container images and their running workloads in your environment.
You can create an assurance policy that will mark these workloads as non-compliant and prevent their execution.
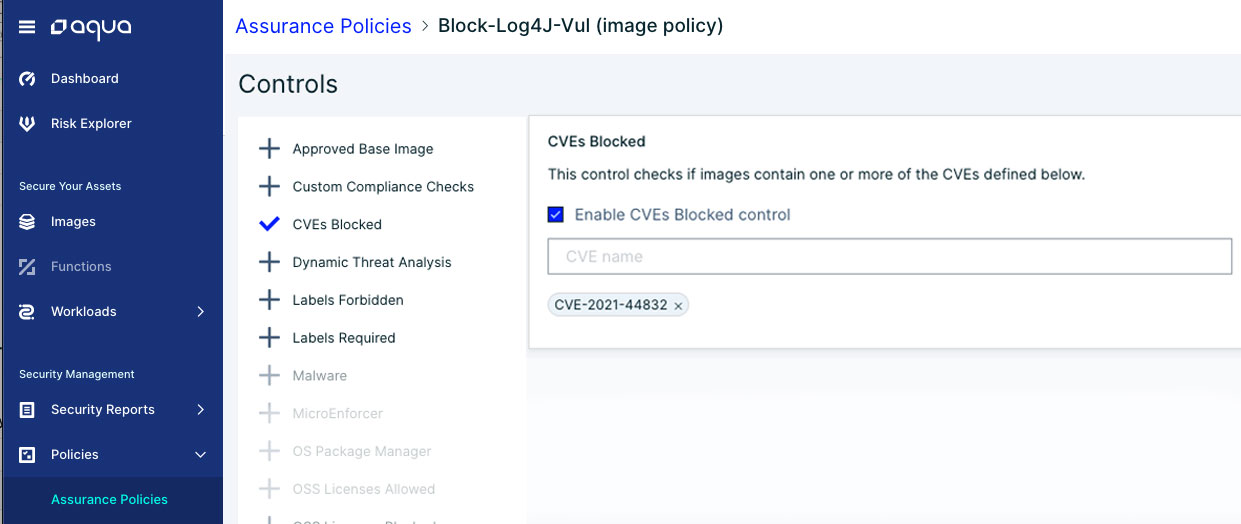
CVE-2021-44832 assurance policy Aqua platform
If CVE-2021-44832 is used to execute a malicious payload, its post-exploitation will be detected and blocked in runtime with Aqua’s drift prevention, which prevents the execution of files dropped during runtime.
Aqua’s advanced malware protection can detect any known threats loaded by the attackers who exploit CVE-2021-44832. Additionally, Aqua CNDR can detect malicious activity executed by the payload, including cryptomining, execution from memory, and escaping to the host.
Conclusion
The Log4j vulnerability has become a major security meltdown, affecting numerous digital systems across the internet, and it will likely continue to develop in the coming months. After the immediate incident response and remediation, organizations should examine how they can enhance their detection and responses processes to address this kind of risk in the future.
Especially as enterprises progress in their cloud native journey, the ability to better and faster evaluate, identify and fix vulnerabilities in both their CI/CD pipeline and containers in production, remains a key component for effective risk mitigation.