Every cloud provider has different resources that require detailed understanding to scan for security issues. To make this easier, cloud providers offer built-in security scanners. However, those may often lack functionality and integration into your existing stack.
To make security scanning easier, we have added Cloud Security Scanning to Trivy starting with Trivy AWS. This tutorial provides an overview of the new feature and how you can get started.
Trivy AWS Vulnerability Scanning Sneak-Peak
Overview
Trivy is a multifunctional, open-source security scanner. It can scan various targets including filesystems, containers, and git repositories among many more to discover security issues. The issues that Trivy identifies might relate to vulnerabilities, misconfigurations, or exposed secrets.
Further, Trivy can be run as a CLI on your machine, in your CI/CD pipeline, or as a Kubernetes operator inside your cluster. Since all its tooling is open source, you can run an unlimited number of scans for free.
Introducing Trivy AWS Vulnerability Scanning
As of this week, Trivy v0.31.0 enables users to scan AWS accounts for security issues. The functionality is currently available either through the CLI locally or by integrating Trivy into your CI/CD pipeline.
The most interesting part of this is that all the misconfiguration rules built into Trivy for IaC scanning are the same ones being used to scan AWS. This means the same rules can be applied both on IaC configurations through `trivy config` and, once the resources have been applied, directly in the AWS account. Trivy cannot only be used to discover security issues but also to find the causes of AWS issues when infrastructure is defined with Terraform or CloudFormation.
Lastly, Trivy AWS is expanding on the `trivy config` functionality by scanning AWS CIS benchmarks.
Getting Started
Trivy uses the same authentication methods as the AWS CLI to configure and authenticate your access to the AWS platform. This means if you already use the AWS CLI, you should be able to run Trivy against your AWS account without any extra configuration – just point and shoot! Otherwise, you’ll need to configure Trivy to use your AWS credentials.
We recommend you use a user/role with thew ReadOnlyAccess policy attached.
Kicking off a scan is as simple as:
trivy aws –region us-east-1
Note that you can even omit the `–region` flag if you have a default region configured in your AWS environment vars or config file.
Reviewing Results
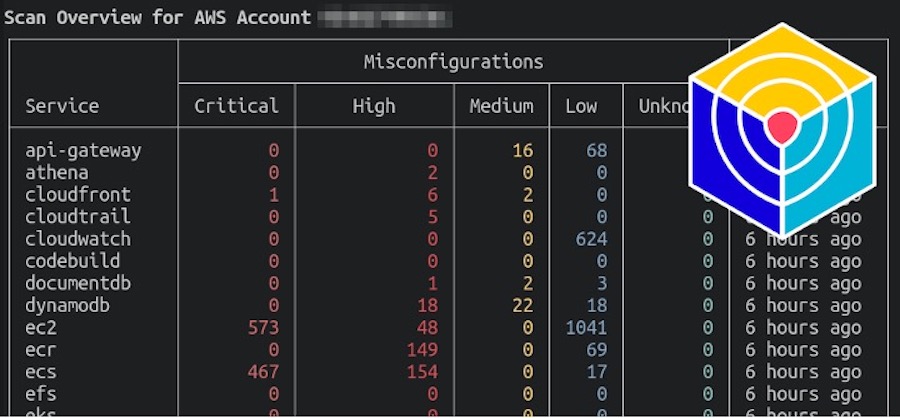
Once the scan is complete, you’ll get an overview in your terminal which should look like this:
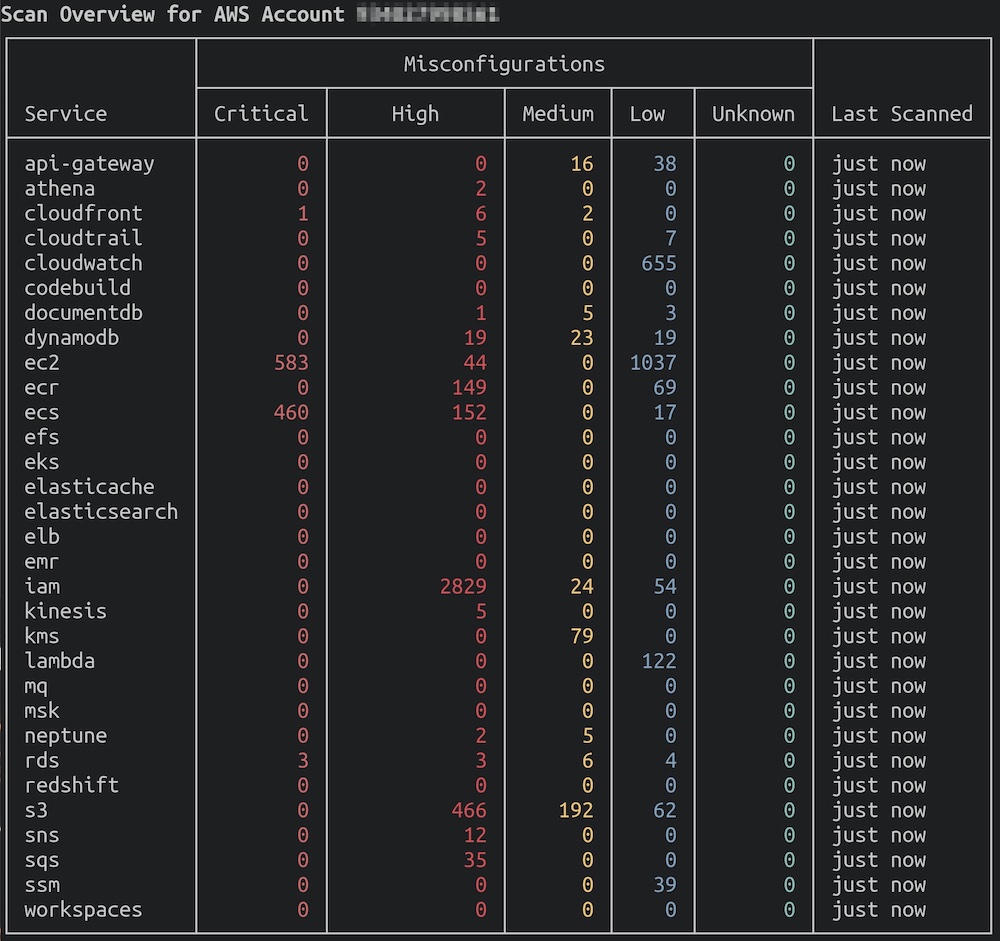
Full Trivy AWS Scan with list of scanned resources and misconfiguration issues
The global scan summarizes the number of results, by severity, for each AWS service scanned.
You can run additional commands to filter the results without having to run the entire scan again – results are cached locally per AWS account/region. Once you scan the same resources again, Trivy will either pull the scan result from the cache or scan and provide further information on specific services, i.e., scan targets.
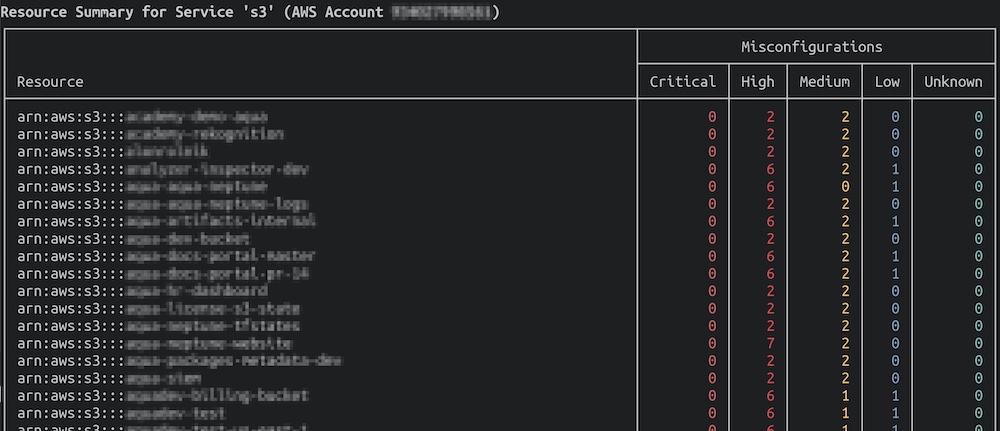
To “zoom in” on results for a particular service, you can use the `–service` flag. In the following command, we scan the s3 buckets in the us-east-1 region:
trivy aws --region us-east-1 --service s3
Note that depending on the resources in your account, you might need to modify the type of service you are scanning. For example, you could scan an EKS Kubernetes cluster instead.
The scan result will show you a summary of the selected service. For each s3 bucket, the Trivy AWS vulnerability scan will show you the associated number of issues, again, sorted by the severity of the issues. Note that this scan will only display resources with detected security issues.
Here’s an example output:
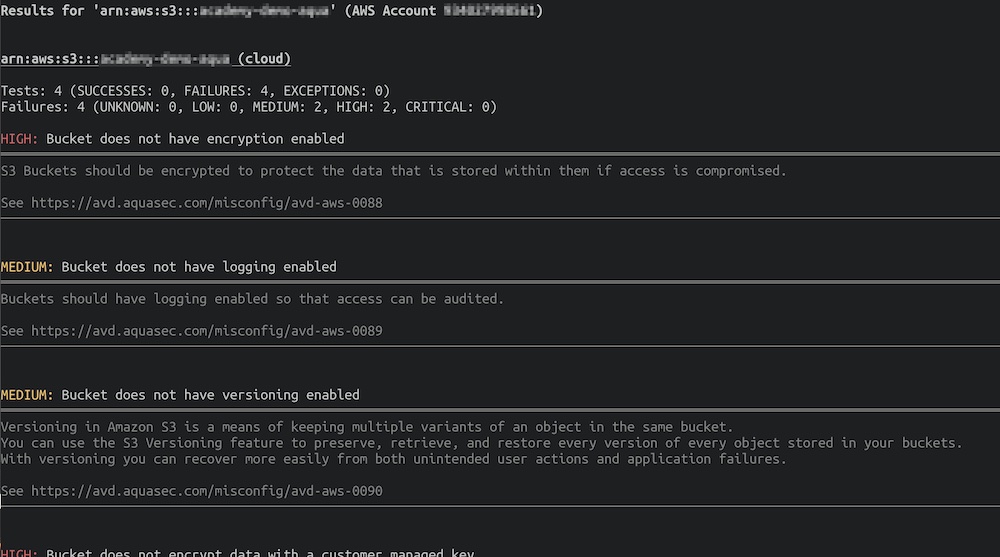
You can show the individual issues for a resource by using the `–arn` flag, for example:
trivy aws --service s3 --arn arn:aws:s3:::example-bucket
Each result contains a severity, a summary, and further information on the issue, with a link to the relevant AVD documentation which includes various guides on resolving the problem.
Summary
Trivy now scans AWS accounts for security issues with all the capabilities of its existing community-enhanced misconfiguration checks.
If you are using AWS, give it a try and let us know what you think. We will be adding scanning of other cloud providers in the near future.
Join the Trivy community
We have lots of exciting plans for Trivy. Become part of the journey by joining our Slack community and contributing on GitHub. Also, let us know if you have questions or if there are other features you’d like to see in Trivy.
And when you try the new Trivy features, share it on social media!