A core part of shifting security left is to check your artifacts and their dependencies for vulnerabilities as early in the dev lifecycle as possible. Whether you’re building your own container images or using third-party images, the Trivy Docker Desktop integration allows you to easily scan any container image directly through the Docker Dashboard. In this blog post, we show how you can get started with this feature.
Scanning your container images with Trivy
Trivy uses a Command Line Interface (CLI) and can be installed quickly either on your machine or it can be integrated within your CI/CD pipeline.
Once installed, you scan container images with the following command:
trivy image <container image>
The list of installation options for the CLI can be found in Trivy’s documentation.
If you are using Docker Desktop frequently, however, you might want to check container images for vulnerabilities directly through the Docker Dashboard. This can be done with the new Trivy integration.
Introducing Trivy for Docker Desktop
Most of the time, you just want to check a container image for vulnerabilities before copying and running it locally or integrating it in your build.
You can now do this directly with the Trivy extension for Docker Desktop. Just follow these steps:
1. Open Docker Desktop.
2. You will see a new section on the left side, called “Extensions”. Selecting “Add Extensions” will lead you to the Docker Desktop marketplace. Here, you can find Trivy.
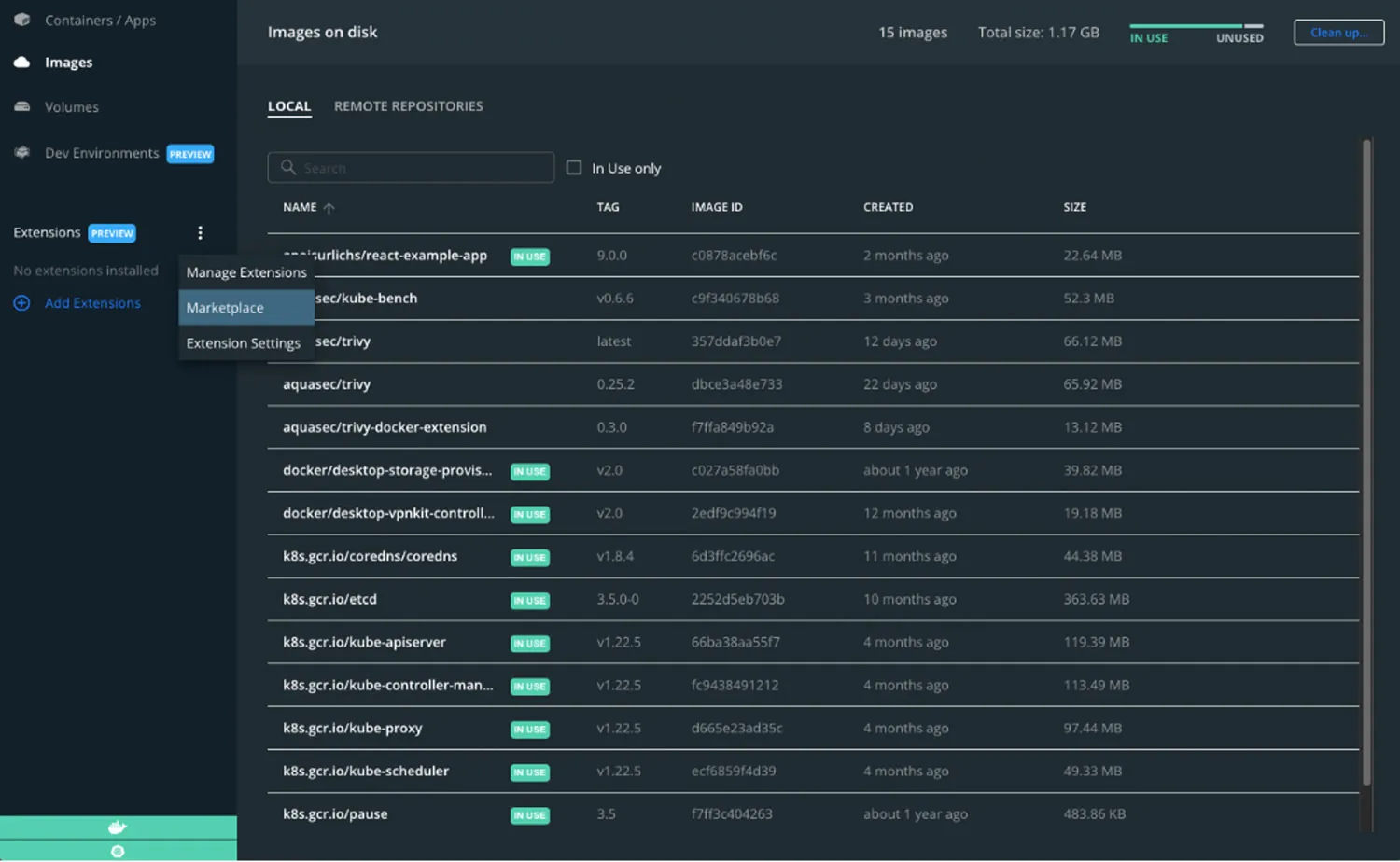
Docker Desktop Dashboard, open the Extension Marketplace
3. Install the extension.
Docker Desktop Dashboard Trivy Extension
Done! You can now scan an unlimited number of container images directly through Docker Desktop. Just open the integration from the Extension section on the left side of the dashboard. Enjoy!
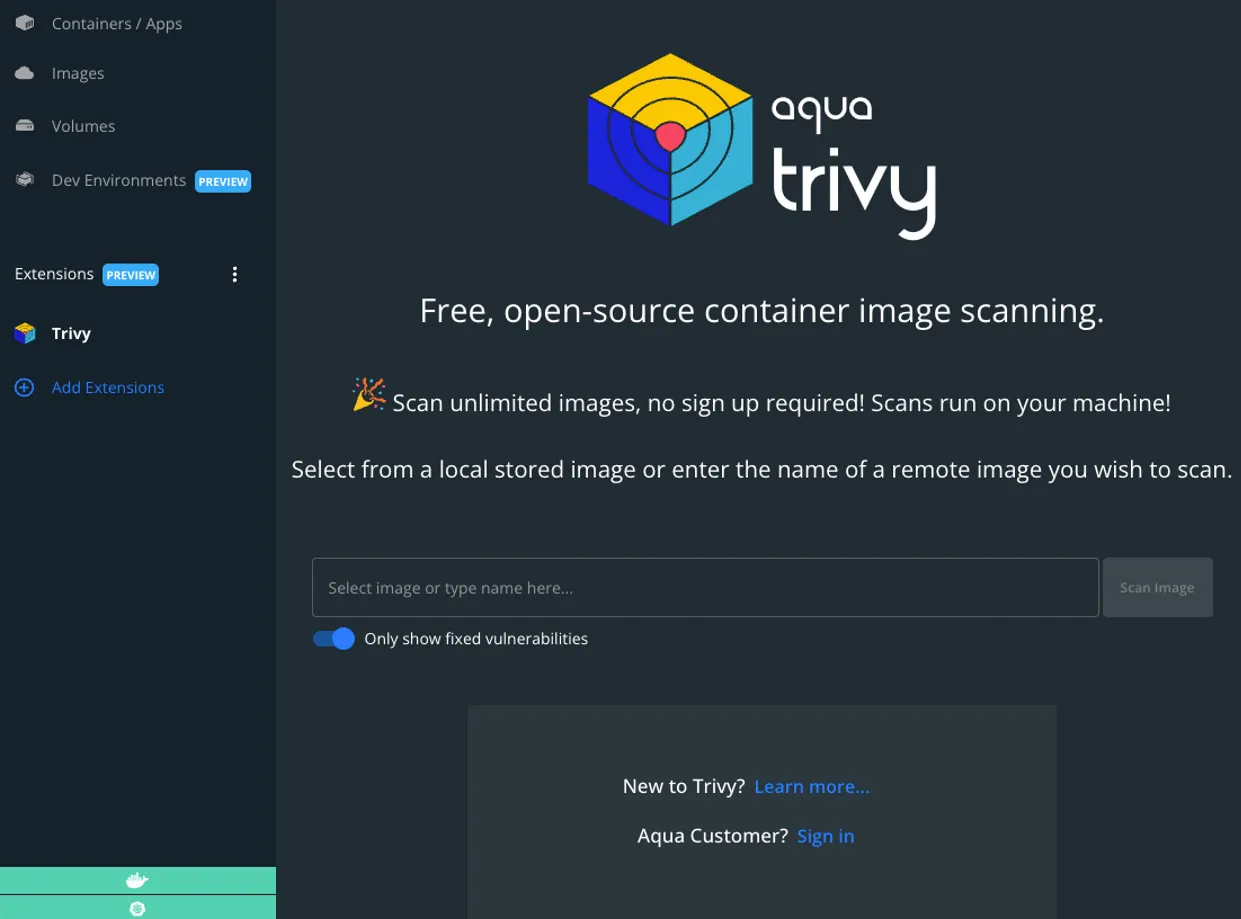
Docker Desktop Dashboard Trivy Extension
Scanning your container images through Docker Desktop
Once you have installed the extension, you can simply parse a container image that you would like to scan into the “Scan Image” section, hit “Enter”, and click “Scan”. You then get the list if vulnerabilities found in the container image:
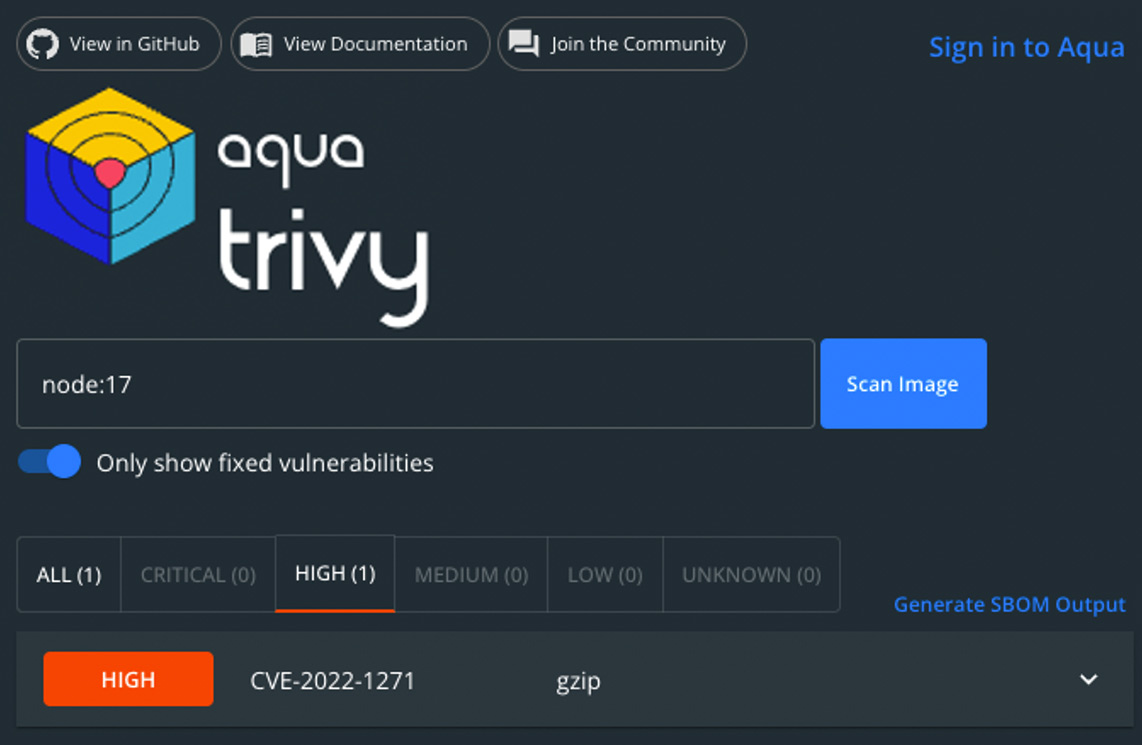
Docker Desktop Dashboard Trivy Extension – Image Scan and Vulnerability list
In our case, Trivy displays only the vulnerabilities that have a fix available. By unchecking the box “only show fixed vulnerabilities”, you’ll see all vulnerabilities that are associated with the image: those that have a fix available and those that don’t.
Below is the output of the same image scan that displays all found vulnerabilities:

Docker Desktop Dashboard Trivy Extension: Image scan and vulnerability list of all associated vulnerabilities
Furthermore, you can scan any container image that you already have locally. Once you select the text box, you’ll see all your existing container images. You can simply select one of them that you would like to scan:
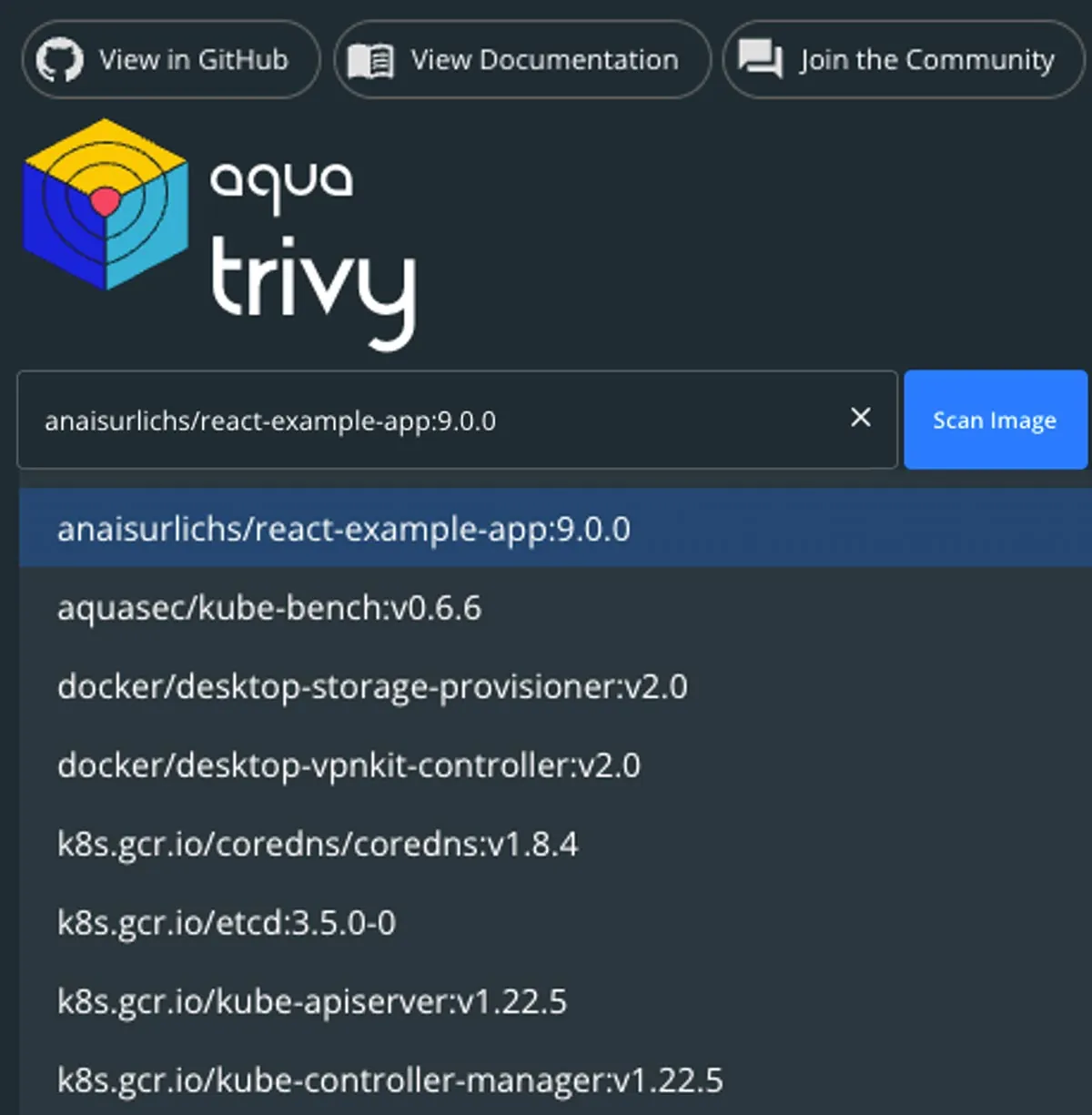
Select container image to scan for vulnerabilities from your local images
Once you scan your container image, all detected vulnerabilities will be displayed below the scan section:
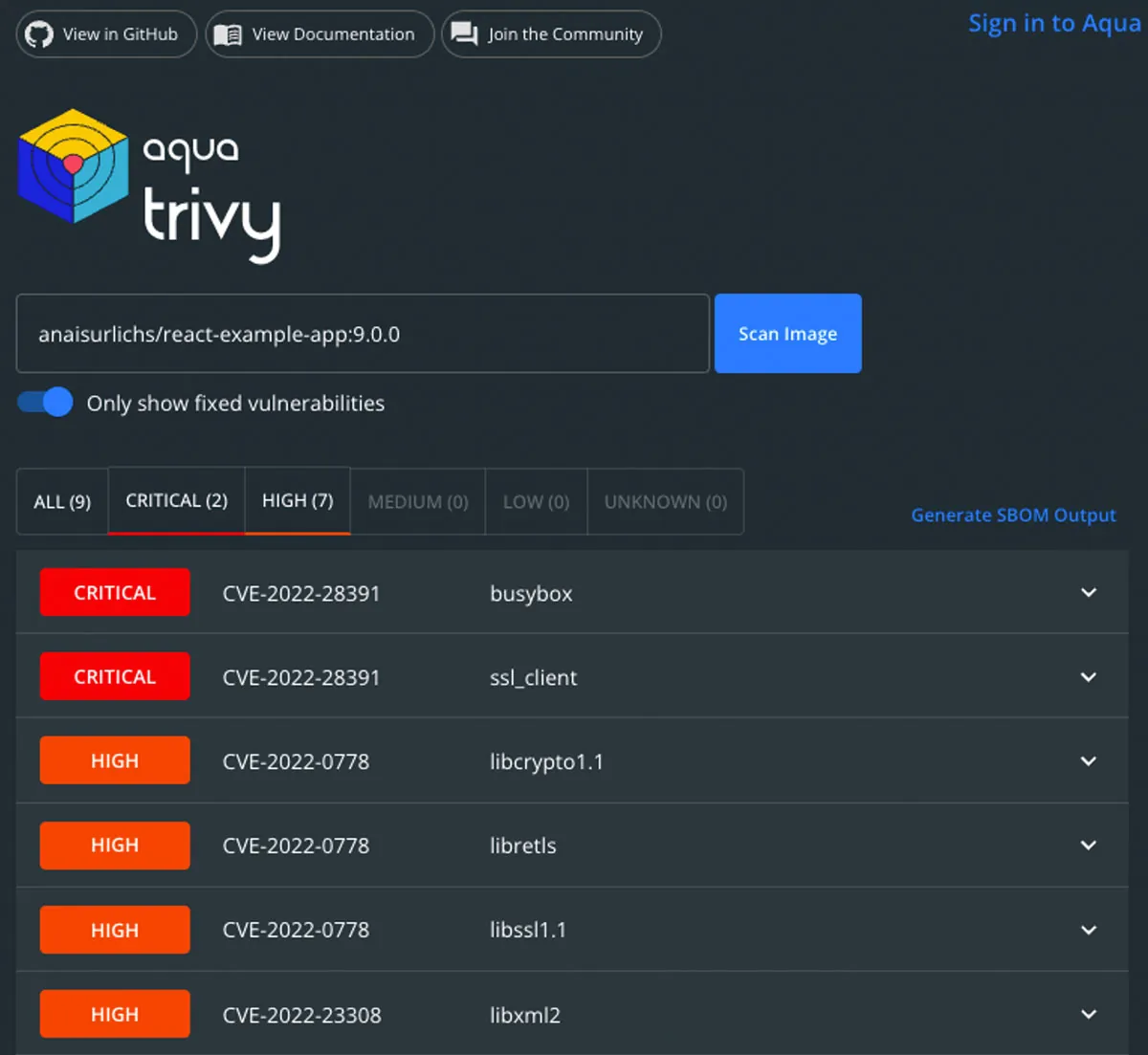
List of vulnerabilities found by Trivy
Trivy SBOM generation
In addition to scanning container images for vulnerabilities, the Trivy extension can also generate software bills of materials (SBOMs) for your container images.
If you’re new to SBOMs, have a look at our previous blog “Software Supply Chain Security with Trivy: Generating SBOMs” for more information on SBOMs and generating SBOMs through the Trivy CLI.
After you scanned a container image, select “Generate SBOM Output” from the right side and you will get an SBOM for your container image:
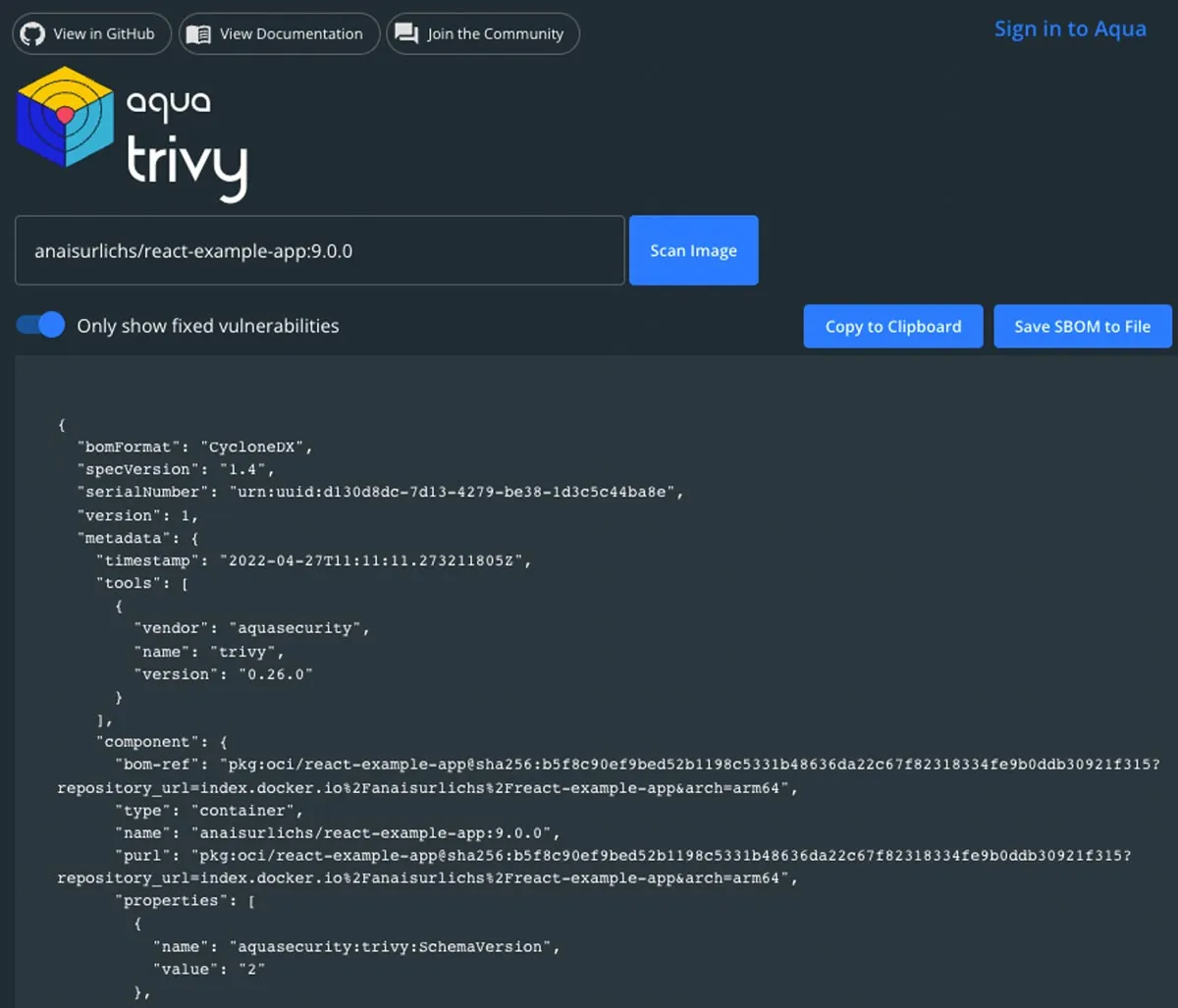
Trivy SBOM output
Note that the SBOM output is supposed to be machine-readable. You can now save the SBOM either to your local desktop or save the output to your clipboard.
Aqua at DockerCon 2022
Trivy for Docker Desktop will be showcased at DockerCon 2022 on the 10th of May. Get your free ticket to join us live!
Summary
If you use Docker Desktop frequently, the new Trivy extension allows you to quickly check your container images for vulnerabilities. In this blog post, we showed how you can install and use Trivy from the Docker Extensions Marketplace, scan container images, and generate an SBOM output.
Make sure to check out the GitHub repository of Trivy to learn more about the different use cases and give us a star ⭐
Also, join our Slack community to ask questions, contribute to Trivy, or just share your feedback and ideas.

