Each day, Aqua monitors millions of cloud infrastructure changes for misconfigurations, and control-plane events for security issues or malicious activity in our users’ cloud accounts. But we’ve learned that just identifying misconfigurations is not enough to protect cloud assets in a modern fast-paced environment. Operating efficiently at scale requires fixing security issues on the fly. With an overwhelming number of variables that exist in cloud environments today, automating the remediation process becomes key.
Several months ago, we introduced Remediations as a feature in Aqua CSPM that enables our customers to automatically address security gaps in their AWS accounts with flexible remediation options. Now we’re extending these capabilities and bringing Remediations to Azure environments.
Understanding Aqua Remediation Types
In cloud environments, the time between detection and remediation of security risks is a crucial factor in reducing the likelihood of them being exploited by a malicious actor. With the sheer number of risks, implementing the proper security controls simply cannot wait until an engineer is able to review a report, schedule a change, and deploy a fix. Remediation must take place quickly enough to prevent exploitation of any misconfigurations.
As a customer of the cloud provider, you get default access to their native security tools that, among other functionality, can provide assisted remediation. However, these are limited in scope and are typically only used for controls that have a quick fix. Within providers’ native offerings, you don’t get granular auto-remediations capabilities that can respond to misconfigurations in real time – which is so critical in modern cloud environments.
Since the earliest versions of Aqua CSPM, we have provided guided remediations – detailed and actionable documentation, guides, links, and references to assist security and engineering teams in fixing the issues CSPM detects. With Remediations, we have added robust capabilities to reduce the critical time between detection and remediation of cloud security misconfigurations. It includes multiple operational modes to match the needs of different use cases and scenarios and to balance the level of automation needed for each security finding.
To ensure maximum flexibility and configurability for any setting, we provide guided, assisted, and automated remediations. Assisted remediations allow developers to evaluate a detected security risk and implement a fix using a pre-defined process directly from the Aqua CSPM dashboard. This ensures that fixes are made in secure, reliable, and repeatable ways, according to organizational requirements.

Automated remediations occur in response to cloud provider control plane activity in which insecure configurations or resource deployments are detected. When these events match a user-defined remediation policy, Aqua will instantly apply a pre-defined fix, preventing the misconfiguration from ever being actively exploited.
To make the use of Remediations as easy as possible, the feature is fully integrated into your existing Aqua CSPM workflows. You can access scan reports, dig into the details, and implement a Remediation all from the same UI. As Aqua provides a single pane-of-glass view into all your accounts and subscriptions across multiple cloud providers, you can easily apply Remediations to just a single account or thousands of accounts in a single location.
Extending Remediations to Azure
With an estimated market share of almost 18% (Gartner, “Market Share: Enterprise Public Cloud Services, Worldwide, 2019”), Microsoft’s Azure is the second most popular public cloud provider that has become a critical infrastructure part for many organizations. As multi-cloud deployments are rapidly becoming the go-to strategy for most enterprises, AWS and Azure are considered the most common cloud combination.
With the growing usage of Microsoft’s cloud offering, being able to automatically resolve configuration issues in Azure environment gets increasingly important. With Aqua Remediations available now for Azure, you can quickly handle misconfigurations across multiple clouds while maintaining granular control over chosen fixes.
For example, organizations often configure Network Security Groups (NSGs) with broader permissions, which can enable unwanted access into their Azure environment. However, a user can define a remediation policy to address this. For example, when a NSG is defined to open a service on the cloud, the user can define the remediation – which can be to block the remote access altogether, or to restrict it to specific known IP ranges. The user has the option to provide that value as part of a manual remediation, or it can be set to a preconfigured value in the auto-remediation policy.
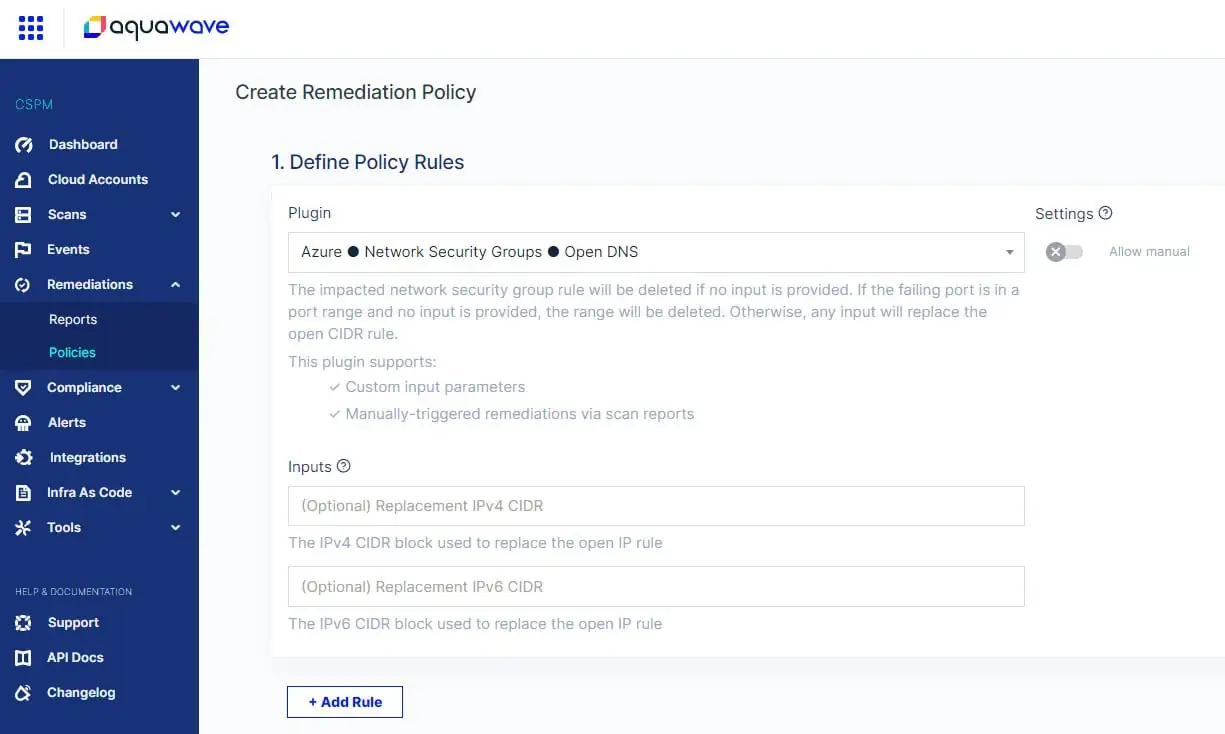
Creating a remediation policy in Aqua CSPM
Security-First Auto-Remediation Model
The key challenge with remediations is ensuring the highest security of the process. A traditional approach to performing remediations involves granting owner access. The case is, to make changes to your cloud resources, most CSPM solutions typically require read/write permissions. As virtually every cloud object might need remediation at some point, granting a third-party full owner-level access to your entire cloud creates huge risk and can potentially open a backdoor. It also violates the principle of least privilege when you should always aim to assign only needed privileges to the necessary resources instead of allowing full admin access to everything.
Another common approach to executing remediations consists in installing remote agents (functions) across all cloud accounts on the customers’ side. However, in this case you need to deal with security and maintenance of these agents on your own – in addition to managing an already complex cloud environment. Most organizations simply can’t afford adding complexity to or increasing maintenance cost of their cloud infrastructure. To overcome this challenge and maintain the ease of use, Aqua uses a different approach.
Our Auto-Remediation feature was developed with a security-first mindset to ensure security and reliability at every step of the remediation process. We came up with a unique security model that uses a temporary token (rotating 6-digit code) to connect to your cloud account. This way, to implement the necessary fix, Aqua gets access only to specific settings within services and for a limited amount of time. The token is never stored by us and the customer only provides it (manually or automatically) upon request. This is a very secure and granular way of performing remediations that is different from how other tools on the market are approaching this.
Maintaining Full Visibility
Remediations is an opt-in feature that is deployed on top of the traditional CSPM scanning connection process. The existing connections between Aqua’s infrastructure and our users’ infrastructure, used for scanning and reporting, remain 100% read-only and limited in scope to specific API calls required to obtain configuration data. This design ensures that only you own the execution of remediations in your environment and that Aqua cannot accidentally make changes in your cloud accounts.
Besides the security controls built into the architecture, the entire remediation workflow is designed to be as transparent as possible. No matter how remediations are triggered, you have full visibility into the progress of the changes made to your cloud resources. To achieve this, Aqua keeps extremely detailed logs – all session details, such as who or what triggered remediation, how it was performed, and others, are recorded at every step. Additionally, a complete snapshot of your cloud environment is recorded before, during, and after the remediation is performed.
Conclusion
While there are currently several remediation products on the market, we have designed Remediations to be unique, both in its security approach and ease of use. With these capabilities, you can automatically fix security risks across your cloud environments while maintaining full control over the whole remediation process.
In one of the future posts, I will delve into technical details of what’s happening behind the scenes when Remediations are invoked and go through the whole remediation flow in a technical deep dive.

