A new vulnerability that impacts Alpine Docker images was published last week. The vulnerability is due to the ‘root’ user password which is set, by default, to NULL on Alpine Docker images from version 3.3 or higher.
This CVE does not impact Alpine distros that are not delivered as Docker images.
Containers that are based on the vulnerable Alpine image and have applications that utilize Linux PAM, or some other mechanism which uses the system shadow file as an authentication database, may accept a NULL password for the ‘root’ user. This may create a scenario in which a non-root user can bypass the authentication process and gain root access inside the container.
Are Your Alpine Images Vulnerable?
To identify whether your image is vulnerable, go to a running Alpine container and execute the following command:
$ cat /etc/shadow | grep root |
A vulnerable container has the following output:
root:::0::::: |
The /etc/shadow file stores the user’s password in an encrypted format. It has a special format in which each line has the user name and fields (separated by a colon) that specifies information about the password, such as the encrypted password, change time, and expiration time.
The second field in the root account of the vulnerable Alpine image is empty. This means that the password is set to NULL.
To fix this vulnerability, use new images for Alpine where the root’s password is set to “!”. This indicates that the root user cannot be used for login applications and you cannot log in to the system with this user. (You can still run applications under this user.)
A fixed Alpine image has this root record:
root:!::0::::: |
Update Alpine Images to the Latest Release
First, we recommend that you update your Alpine-based images to the latest release.
The issue was fixed in the following Docker image releases (March 7, 2019):
- edge (20190228 snapshot)
- 9.2
- 8.4
- 7.3
- 6.5
Versions 3, 4, and 5 are EOL and are still vulnerable, with no available fix.
Using Aqua to Detect and Mitigate This Vulnerability
Use Aqua’s image assurance policies to verify whether your images have an empty root password. Create a script that checks for the CVE-2019-5021 vulnerability:
1. Create a script that checks for the CVE-2019-5021 vulnerability:
#!/bin/sh
|
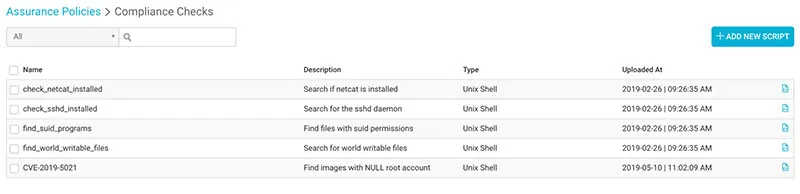
2. Upload this script to the Custom Scripts library:
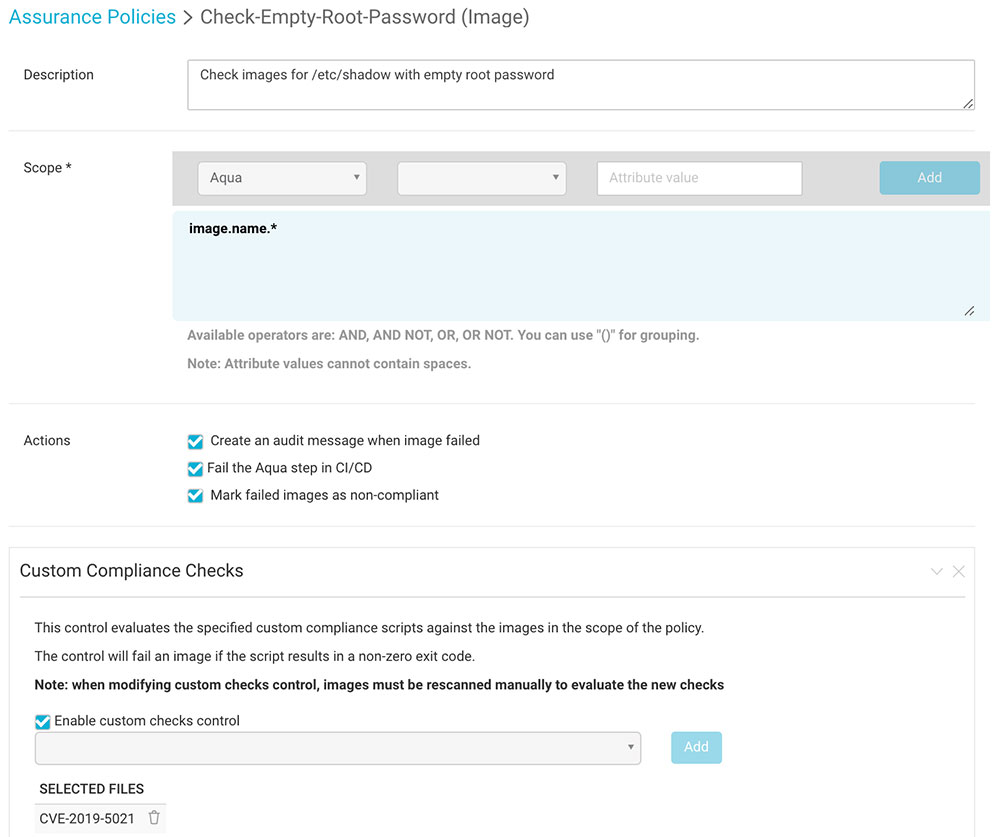
3. Create an Image Assurance policy that checks images for the empty ‘root’ account password:
4. Scan an image. An image, whose /etc/shadow has a null root user, fails the custom compliance check:
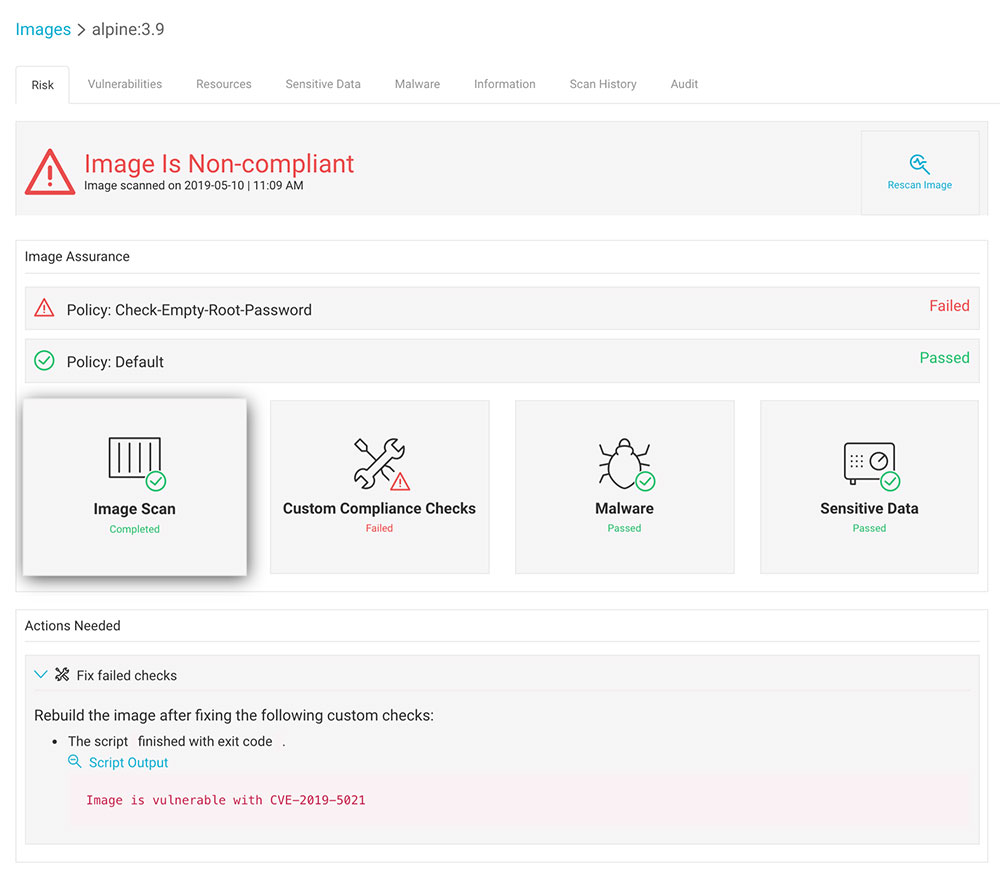
(This screenshot was taken on an Alpine:3.9 image before it was fixed.)
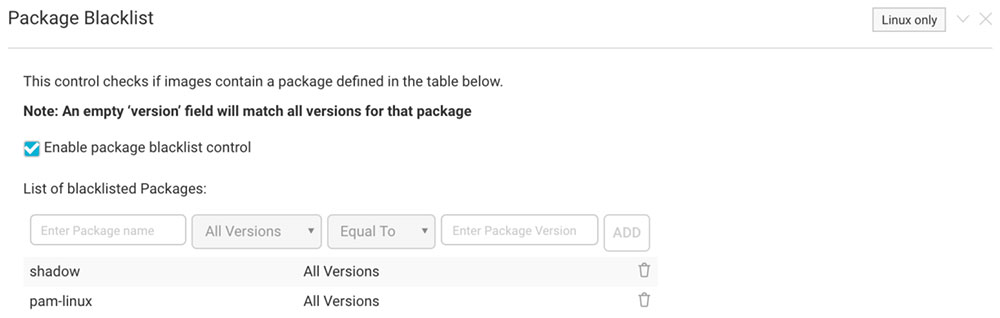
You can also check if shadow or linux-pam packages are installed. These packages are necessary in order to exploit this vulnerability. To check for these packages, add the Package Blacklist control to the Image Assurance policy: