https://www.aquasec.com/cloud-native-academy/application-security/cyber-kill-chain/In late October, a supply chain attack affected a popular npm library, ua-parser-js, which put many companies at risk of compromise. In this blog, we will describe the attack and outline a few ways that organizations can mitigate similar threats. This is an example in a growing trend of cyberattacks that leverage the software supply chain to access sensitive data and enterprise resources in the cloud.
Origins of an attack: How ua-parser-js was compromised
In this incident, attackers inserted malicious code into three versions of the popular npm library ua-parser-js after seemingly taking over the developer’s npm account. Ua-parser-js is used to parse user agent strings to identify a user’s browser, operating system, device, and other attributes. It had over 8MN downloads in the final week of October 2021 alone, and many libraries count it as a dependency.
The broad usage of the library highlights the implicit trust that many developers have in community-driven or broadly endorsed software libraries. It appears that an attacker compromised Faisal Salman’s (a lead developer and maintainer of ua-parser-js) npm account and inserted malicious code into versions 0.7.29, 0.8.0, and 1.0.0 of ua-parser-js. Salman raised the warning with the following:
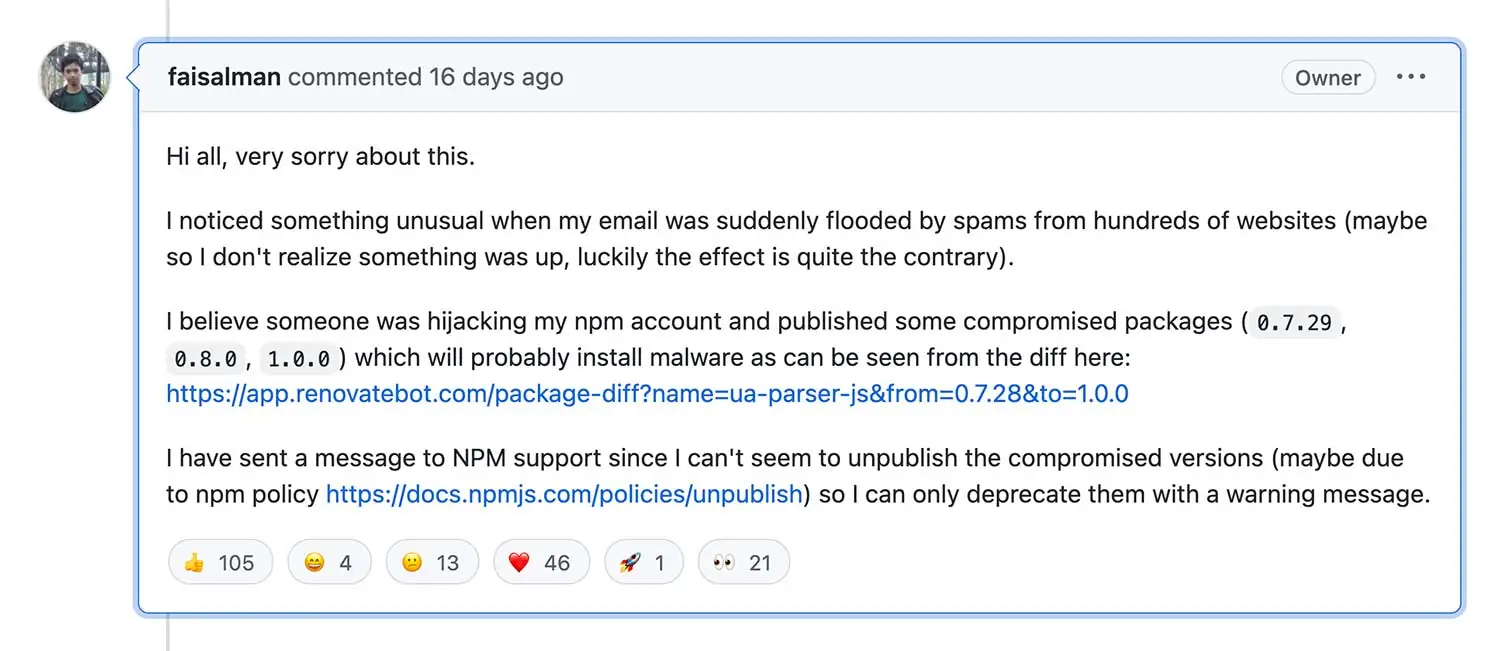
In the October incident, Salman noted that the attacker flooded the developer’s email account with hundreds of spam emails. This tactic, known as email bomb, is intended to act as a smokescreen for sensitive emails, such as password reset notifications. This served as an early alert to the developer about the malicious activity. However, it wasn’t enough to stop the attack, which was left to compromise library users for a few hours. Updated versions of the library – 0.7.30, 0.8.1, and 1.0.1 – fixed the compromise.
How the attack works
After installation, a script detects which operating system is in use and downloads either a Windows batch file or a Linux ELF binary. Both of those, in turn, download a cryptominer from the Internet. Here are the preinstall scripts:
- bat md5: d98a3013336b755b739d285a58528cbe
- sh md5: 4dbee17293a6e54b509a8d99f96bb666
- js md5: a4668a1b3f23b79ef07d1afe0152999e
Once the cryptominer launches with arguments that define the mining pool, wallet, and number of CPU threads, it begins to abuse the affected organization’s cloud resources to mine cryptocurrency for the attacker.
According to Bleeping Computer, on a Linux machine, the preinstall script detects whether the machine is in Russia, Kazakhstan, Ukraine, or Belarus, in which case the attack will terminate. Such activity is generally anomalous.
In Windows machines, the batch file downloads a DLL and saves it as create.dll (md5: de8b54a938ac18f15cad804d79a0e19d). The DLL file is a password-stealing Trojan that steals passwords from more than 100 applications, including email clients, messaging services, browsers, FTP clients, and more. Create.dll also executes a Windows PowerShell script to steal passwords from the Windows credential manager.
Similarities to other malicious libraries used in supply chain attacks
This attack may be linked to three other malicious libraries that previously were published to npm – and that even might have been created by the same threat actor. Evidence for this conclusion can be found with the malware that was used, precisely jsextension.exe (md5: 0ebdea4e452c6358f7d873f5b8da5c23) and the jsextension Linux shell script (md5: 217c5e889c058c3ec7a261a654f39a0c). These scripts have the same file names and hashes as those used in the klow, klown, and okhsa malicious libraries.
In addition, the way the malicious code works is similar across all the malicious libraries, even using the same preinstall and post-install Bash and Batch scripts.
There are two differences, however:
- This attack uses a different Monero wallet address for the mined cryptocurrency.
- This attack uses a password stealer on Windows machines. This has the potential to give attackers what they need to move laterally into applications that contain all kinds of sensitive materials.
How to protect against this attack
Anybody using ua-parser-js — especially one of the compromised versions discussed earlier — should assume their machines are compromised. The many other projects that are dependent on this library may also be compromised, so the full effect of this supply chain attack could be far reaching.
It is also important to determine if the jsextension.exe or jsextension Linux ELF binary are present on any machines, as well as identify any instances of create.dll, the password-stealing Trojan.
In addition to identifying infected machines, rotating all credentials is critical. The password stealer has the potential to compromise many credentials for a variety of sensitive applications. Leaving those credentials in place leaves the door open for persistent attacks and data theft. As always, it is key to apply best practices for securing the software supply chain.
How Aqua can help detect and block malicious activity
Supply chain attacks such as these can be tricky to combat. There are many potential attack vectors that exploit different aspects of the software supply chain. Supply chain attacks like this are designed to gain entry via trusted libraries, relying on shortcomings in developers’ security risk awareness, or on automation baked into build pipelines so compromised packages can infiltrate dev teams’ projects without detection.
The malware used in this attack, specifically jsextension, would have been detected by Aqua’s Dynamic Threat Analysis (DTA) (see the screenshot below). If there is any malicious traffic between the cryptominer and the command-and-control server, DTA also would identify any potential malicious network or Internet communications.
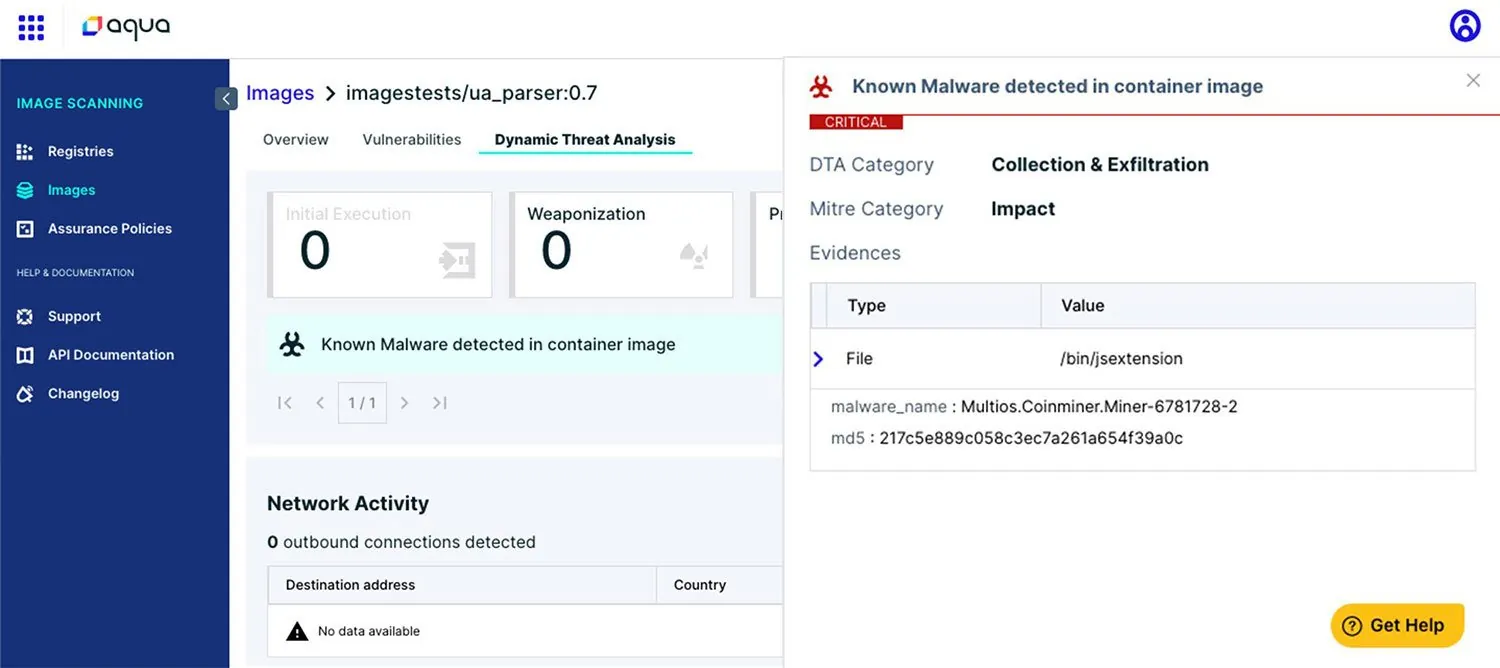
DTA uses a secure hosted sandbox environment to deploy images and document all activity that occurs at runtime, cataloging the attack kill chain and anomalous activity per the MITRE ATT&CK framework for further security review and forensic analysis.
Because these attacks are designed to circumvent security controls, it’s important to monitor for markers of malware and compromise across the entire development life cycle.
To learn more about software supply chain attacks and best practices for securing cloud native applications against them, check out the webinar Securing the Software Supply Chain in the Cloud Native Stack.
While the scale was much smaller than the ua-parser-js compromise, a similar issue was observed earlier this year when Nautilus, Aqua’s threat research team, uncovered five malicious container images that were hosted on Docker Hub.

