Aqua has been securing Amazon ECS workloads throughout its evolution and now we are expanding our support to secure Amazon’s new ECS Exec; a simple, secure, and auditable way to execute commands into containers. This new capability extends Aqua’s runtime protection features, including drift prevention, to ensure that legitimate access to containers is allowed while still preventing disallowed actions.
Amazon ECS Exec simplifies troubleshooting by leveraging the AWS CLI utility and employing SSM Session manager under the hood to facilitate the communication which can be controlled, encrypted and audited. Before, troubleshooting an Amazon ECS task was a hassle. It involved managing key pairs, running SSH on the EC2 instances and using Docker commands – all without limiting access. This problem was further amplified for an ECS task on Fargate, which essentially was a black box with no access to the underlying host or visibility into the container. Amazon IAM has always been at the heart of AWS security for safeguarding the various services and features they offer, and ECS Exec is no exception. IAM policies can be leveraged to control access to execute commands, getting as granular as you want using tag-based access controls.
With this new feature, AWS provides the right set of tools to interact with ECS tasks while owning the operational burden to make it happen. However, this opens up yet another avenue for a malicious attacker to potentially gain access to your application. Aqua has added support for Amazon ECS Exec to its current suite of layered, cloud native security controls. This means that customers can use the new Amazon ECS Exec feature without worrying about Aqua interfering or blocking its capability, and without lowering any of the current protection that customers enjoy from Aqua.
Aqua support has been extended across the following suite of features:
Container Drift prevention – Enforces container immutability and detects any unapproved changes to running containers that deviate from their originating images. This in no way affects the troubleshooting capabilities, but instead offers an additional layer of security for any misuse of this execution feature, be it in the form of code-injection, zero-day attacks or even insider attacks like a rogue administrator with the excessive IAM access.
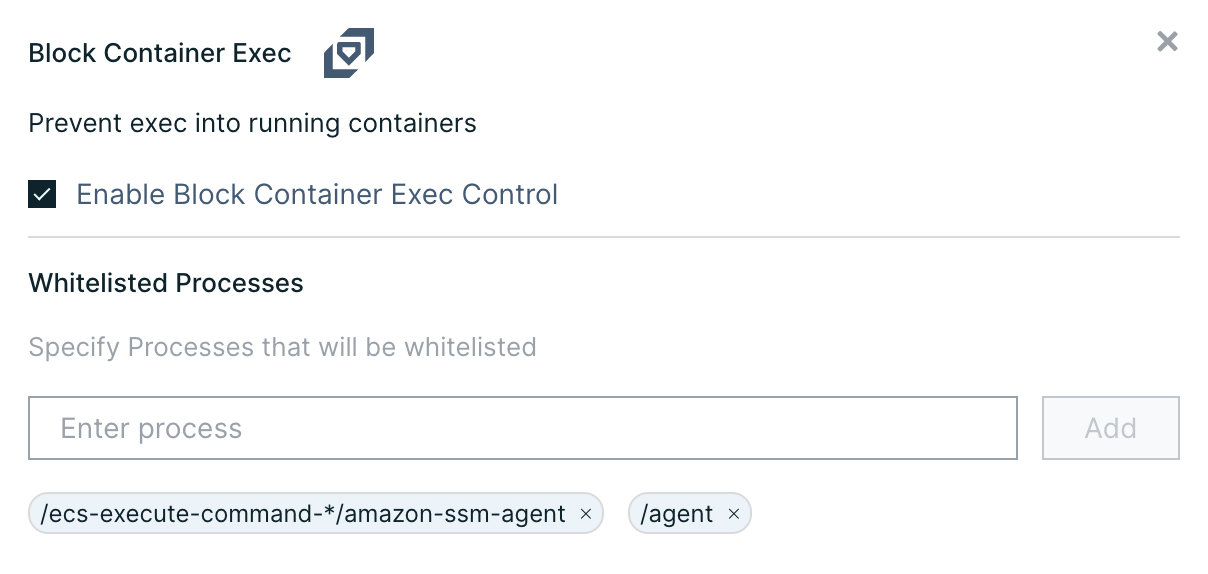
‘Blocking container exec’ – Is another useful control to seal off and discourage the use of docker exec in favor of ECS Exec. The whitelisting capability can be used to establish ECS Exec as the tool of choice for accessing containers. You can also choose to block both Docker and ECS execute capabilities if desired.
Network segmentation – The main motivation of advanced adversaries is authenticated access, which enables them to blend into normal activities and hijack cloud resources. Aqua delivers another powerful control for network segmentation which can limit the blast radius of undetected attacks by making it harder to get to the higher-value cloud resources.
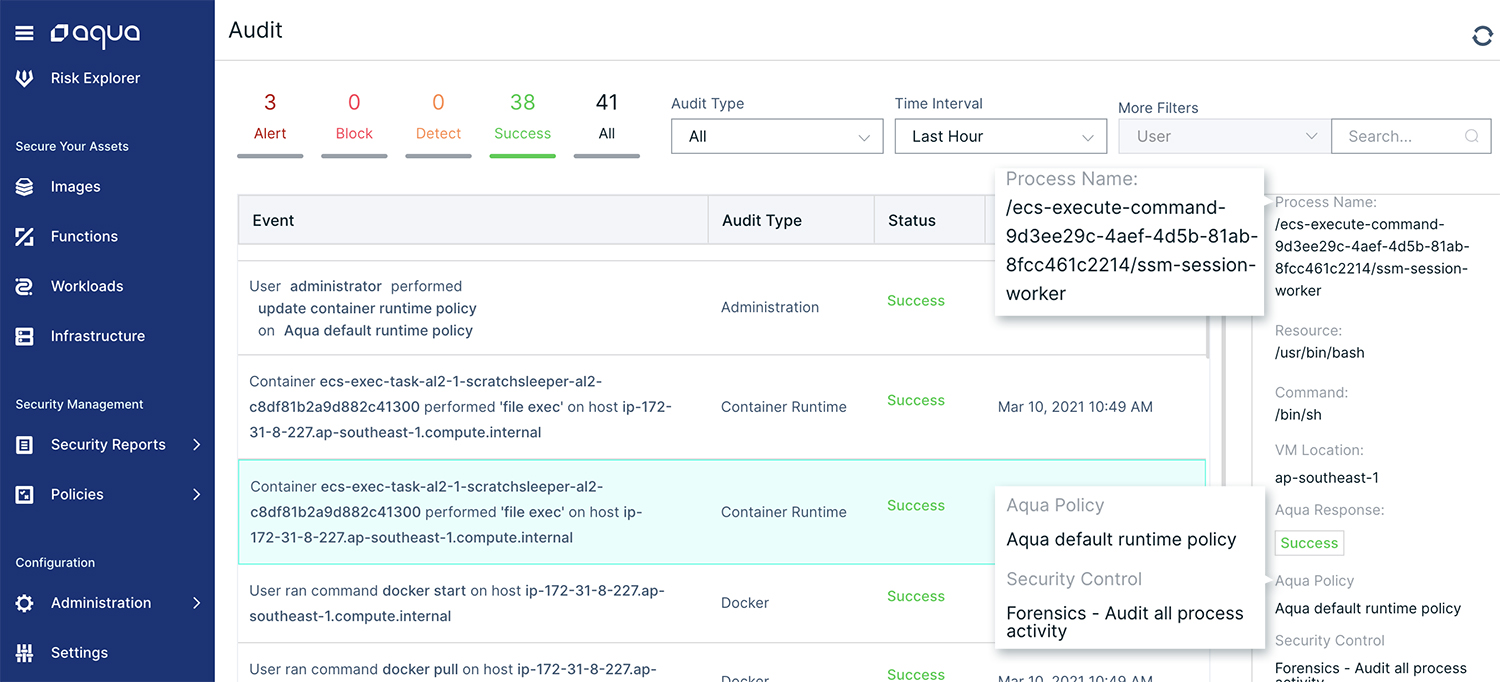
Container Forensics – Using the container forensics control, Aqua reinforces the audit activities performed by AWS, correlating the container actions to security policies and pinpointing the location and origin of the violations when they occur.
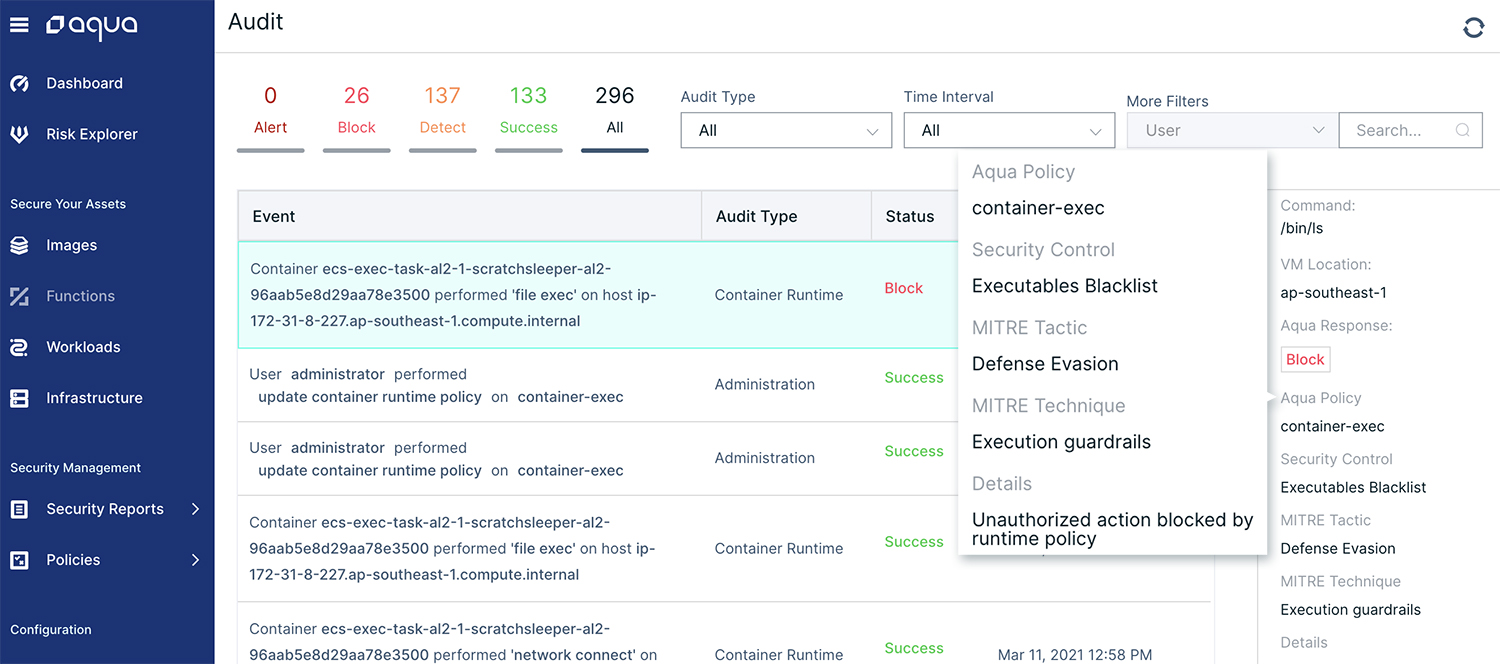
We further map these violations to the appropriate MITRE tactics and techniques to better understand the attack surface and aid in their mitigation. We also provide provenance of the exec attempts, indicating whether they originated from the Docker client or the ECS SSM agent.
Closing thoughts
Amazon ECS Exec is essentially a debug tool to interact with processes in containers during development, but as such it can bypass what is normal, immutable operation of containers. The Aqua platform supplements the IAM policies with an added layer of protection to enforce intended purpose, preventing it from being exploited for malicious intent. At Aqua, we believe in complementing your cloud native projects with flexible, granular security controls that keep application development fast and nimble. We also aim to support customers’ choice in cloud platforms and solutions, allowing them maximum flexibility.

