The rise in software supply chain attacks presents a profound challenge to the cornerstone of DevOps practices: the heavy use and reuse of open source software (OSS). Aqua Security extends visibility into risks across the software stack – and helps teams maintain a clear view into their software bills of materials (SBOMs) with the integration of our OSS container image vulnerability scanning findings with Sonatype’s Nexus IQ policy engine.
Aqua’s scanner comprehensively scans container base layer images, including the popular Alpine distribution for container base images, for known vulnerabilities, embedded secrets, OSS licensing issues, hidden malware, and configuration issues.
Using a lightweight Postee integration, customers can easily consume the vulnerability output and findings in their Nexus environment to supplement the tool’s open source security monitoring and seamlessly incorporate risk-driven base layer findings in their existing DevSecOps strategy.
The primary use of the open source Postee application is to act as a notification component for Aqua Security products. The application is also useful for sending vulnerability scan findings, incidents, and other alerts from the Aqua Platform to collaboration systems.
The supply chain security risks of OSS
Open source is widely used across cloud native environments, largely because of how it facilitates faster development and shifts some of the code maintenance burden onto a broader community or vendor landscape.
As part of the cloud native approach, we see significant growth in the frequency of updates to OSS and the profusion of additional tools or platforms that help developers better manage or automate their builds relying on OSS. However, these applications are built with complex hierarchies, and the operations teams are tasked with attesting to the security of software in production.
Vulnerabilities can be introduced anywhere throughout the build pipeline process: in the base image, the added components, or the application code itself. DevOps teams can then unknowingly deploy these images on a host – introducing the risk that the host operating system, containers, and orchestration engines could be compromised.
Over the course of 2021, Aqua’s Team Nautilus identified a series of malicious container images posted on DockerHub that would allow attackers to hijack organizations’ resources to mine cryptocurrency or could be used as part of a supply chain attack targeting cloud native environments. Developers had already pulled down one of the five identified images over 100,000 times.
Identifying vulnerabilities in OSS base images – like the popular Alpine distribution – is a key element in managing supply chain risk, and guided remediation of new, high-risk vulnerabilities as part of DevOps workflows can improve overall security posture.
Identifying OSS container image vulnerabilities and risks
The Aqua platform analyzes container images, code, configurations, and permissions for vulnerabilities, provides risk-based vulnerability prioritization, and enables build automation with DevOps pipeline integration.
Aqua’s scanner provides broad coverage of container image layer distributions, operating systems, and programming languages with ongoing updates to the CyberCenter vulnerability database and severity classifications. For instance, Aqua can scan Golang binaries and extract module information, which then allows for vulnerability analysis to take place.
Aqua scans directly within image registries and the CI/CD pipeline as well as function stores, providing comprehensive coverage of vulnerabilities, context, and potential exploits to facilitate rapid remediation before the build.
Aqua’s risk-based insights encompass contextual factors to generate a complete list of vulnerabilities that can be narrowed down and refined based on factors like exploitability, severity, and whether the workloads are running, helping to clearly prioritize vulnerabilities for remediation.
Integration of Aqua findings via Postee
With a lightweight Postee integration, teams can send vulnerability data and findings from Aqua to Nexus IQ Server. Postee is a simple message routing application that is maintained by Aqua as an open source project. Postee receives JSON input messages through a webhook interface and delivers updates based on preconfigured rules.
Postee can be integrated into the Aqua console to deliver vulnerability and audit messages to target systems, including Nexus IQ Server, based on predefined rules. DevOps and DevSecOps teams can configure the Aqua Server to send a webhook notification from the platform whenever a new vulnerability is found.
The application also integrates with application lifecycle management systems (such as JIRA and ServiceNow) and messaging systems (such as Microsoft Teams, Slack, and Simple Email) to facilitate incident response workflows.
Postee can be deployed close to the Aqua Platform as a microservice in a Kubernetes environment. Deployment is easy via Helm charts or Kubernetes manifests.
Customers can configure the integration and event output in a few simple steps:
Navigate to the Image Scan Results Webhook page, under the “Settings” menu in the Aqua console.
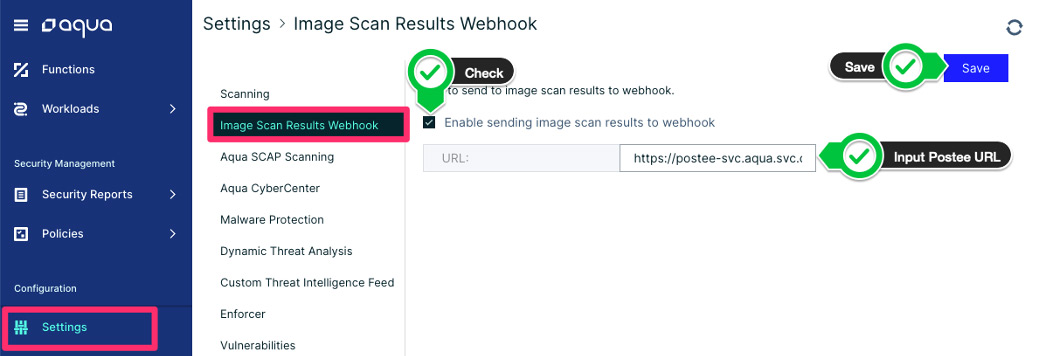
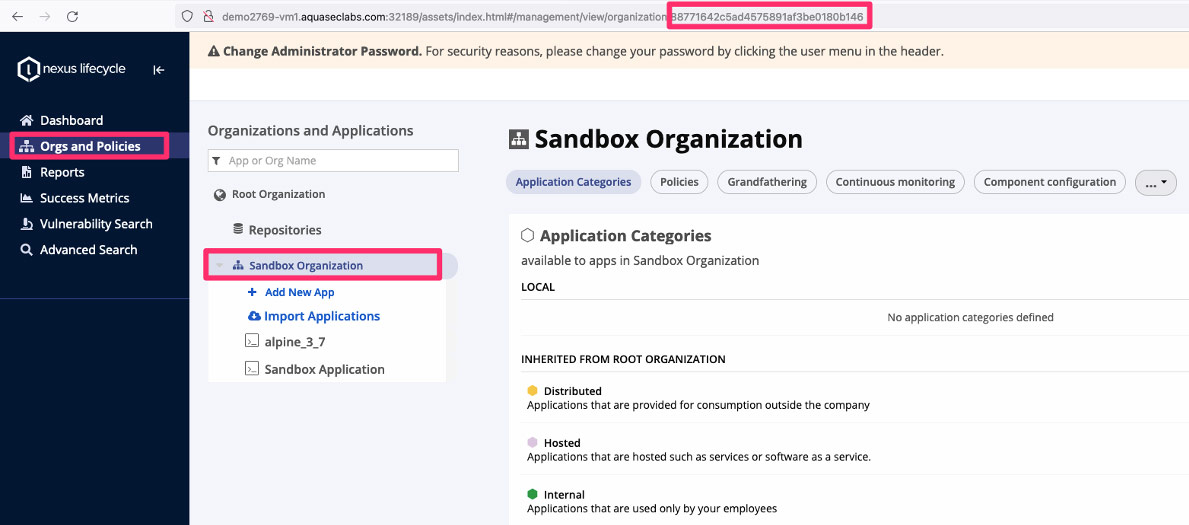
In Nexus, the Aqua integration is tied to an Organization, which then creates application reports under that specific organization.
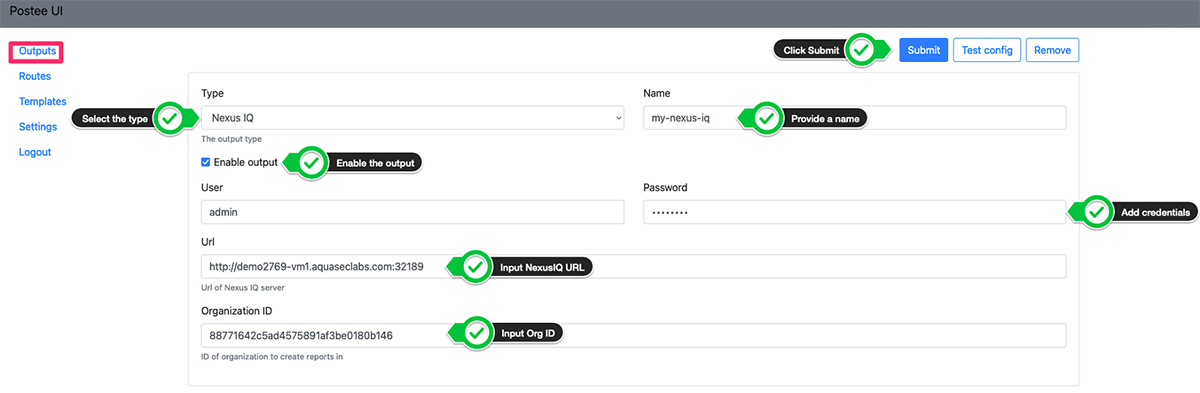
Once the integration from Aqua to Nexus Lifecycle is configured, teams can configure Outputs in Postee. Outputs are remote services that messages should be sent to. Each output has two mandatory fields: ‘name’ and ‘type’.
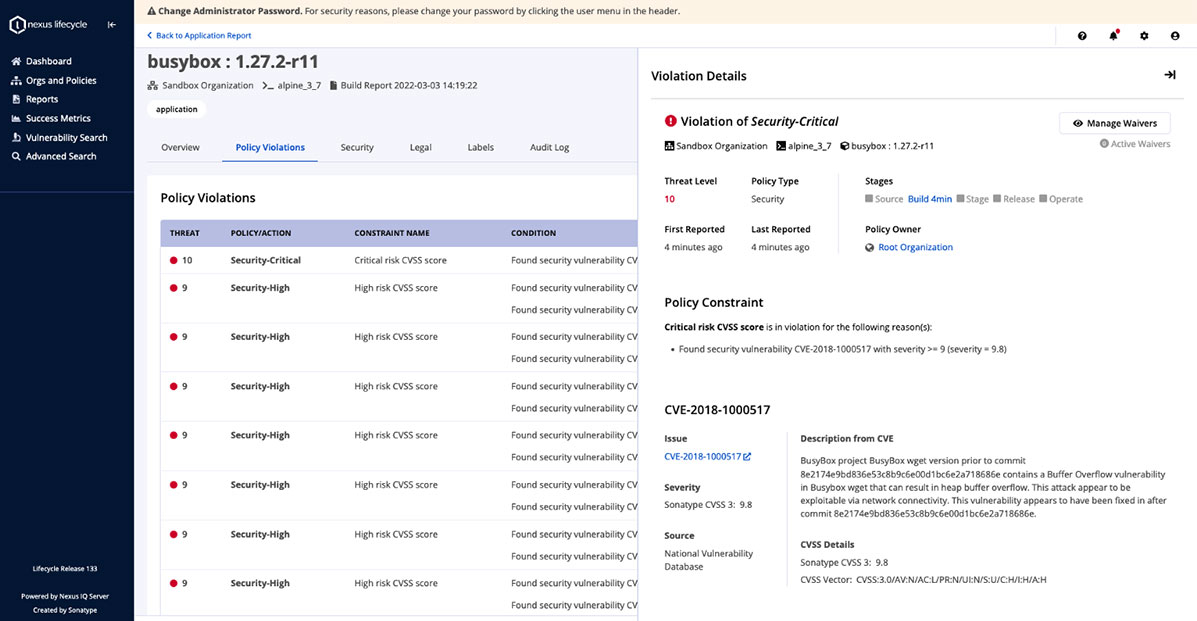
After testing and validating the integration, scan output will appear in a new application report outlining the vulnerability findings from Aqua.
Conclusion
The risks posed by vulnerabilities and supply chain attacks threaten to undermine the value and benefits of open source software for DevOps teams and the businesses they support. Integrating Aqua’s container base layer image scanning findings into Nexus’ open source monitoring tools enables teams to gain full visibility into their OSS stack. It also provides the context that DevSecOps teams need to better secure their cloud native environments and take a proactive stance in addressing the supply chain issues that span the OSS stack.

